UK-based gym chain Total Fitness has been accused of sloppy security, following the discovery of an unsecured database containing the images of 470,000 members and staff – all accessible to anyone on the internet, no password required.
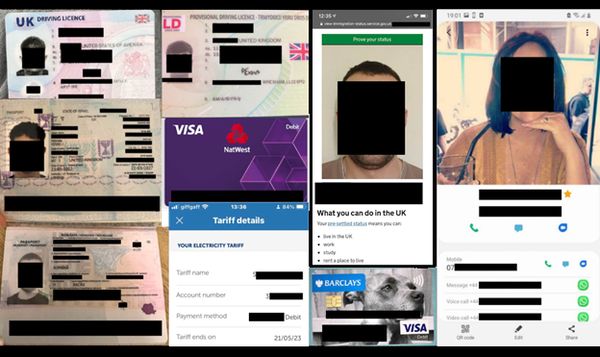
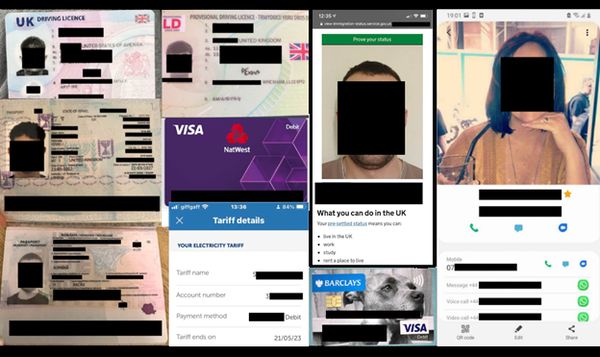
A 47.7GB database belonging to the health club was discovered by cybersecurity researcher Jeremiah Fowler, who told The Register he had also uncovered images of members’ identity documents, banking and payment card details, phone numbers, and even – in some cases – immigration records.
According to the researcher, lax practices at Total Fitness meant serious questions had to be asked about how the company had collected customer images, how they were stored, who had access to the images, and how long they were retained.
“Nearly all social media accounts offer users the ability to have a private profile and have strict control over who can access their content. However, this doesn’t seem to be the case for member-uploaded images on Total Fitness platforms,” said Fowler. “It is hypothetically possible that the images stored in the backend database are potentially retained even after being deleted by the member. This would potentially explain why the database contained images of sensitive documents.”
According to Fowler, highly sensitive pictures of passports and utility bills were exposed in the unsecured database.
Total Fitness has disputed the extent of the data breach, claiming that members’ images only comprised a “subset” of the database, and that most images did not contain personally identifiable information.
For his part, Fowler claims that members’ images took up roughly 97% of the database.
Regardless of whether Total Fitness or the security researcher is accurate in their portrayal of the breach, I wouldn’t be happy if it was an image of myself or my child that I had uploaded believing it would be stored securely that had then been exposed.
Total Fitness says it has now secured the database, and the breach has been reported to the UK’s data regulator, the Information Commissioner’s Office (ICO), for investigation.
While Total Fitness claims there is no evidence of unauthorized access to the database aside from that by Fowler, it’s clear that the potential for abuse was definitely present. The exposed images could be used for a number of criminal pursuits including identity theft, romance scams, or even the creation of deepfakes.
Organisations who wish to avoid similar breaches would be wise to follow best practices, including implementing strong access controls, data minimisation, data encryption, and regular security audits.




GIPHY App Key not set. Please check settings