Losses to investment scams, romance fraud, and pig butchering reached $4.6 billion in the United States, a 38% increase in 2023. These scams often play out in private peer-to-peer conversations between victim and criminal, well beyond the reach of typical threat intelligence.
Netcraft has explored these scams by leveraging a first-of-its-kind AI-powered solution that communicates with criminals at scale. Responding to lure email and SMS messages, our AI-based personas continue the dialogue to uncover hidden financial and technical infrastructure. Following the money by disrupting money mule networks identified in confirmed scams in real-time could disable entire threat actor networks in one fell swoop.
The reach of these scams runs deep with criminal bank accounts, mule accounts, crypto wallets, and a connected web of malicious infrastructure used to further these scams. We have extracted thousands of criminal money mule bank accounts across 73 countries and more than 600 financial institutions. In one case, we have received 17 mule accounts from one conversation. The top four crypto wallet addresses Netcraft identified have received more than $45 million (1,000 BTC).
Equally, criminals, like the rest of us, are human too. And a long-lived but ultimately fruitless conversation with a Netcraft-controlled persona can cause frustration – as you’ll see later.
Crime pays. The hours are good, you travel a lot.
One in six of our conversations with criminals has resulted in details of at least one bank account being sent. Other conversations end with requests to buy gift cards, cryptocurrency payments, online payment providers (like PayPal), or money remittance services (like Western Union). While others fade out over time as the conversation naturally goes cold.
When we see the whole scam play out, on average, criminals send more than 32 messages despite receiving only 15 replies. Standing out in the data is that criminals are eager to engage quickly and frequently and maintain these scams over an average of more than 47 days.
Inside the Scam
The following examples have been reproduced from actual conversations with criminals where the initial message received was fraudulent. Many represent weeks and months of dialogue involving dozens of messages (emails, texts, etc.). Images have sensitive information removed and truncated conversations for brevity.
All in on Crypto
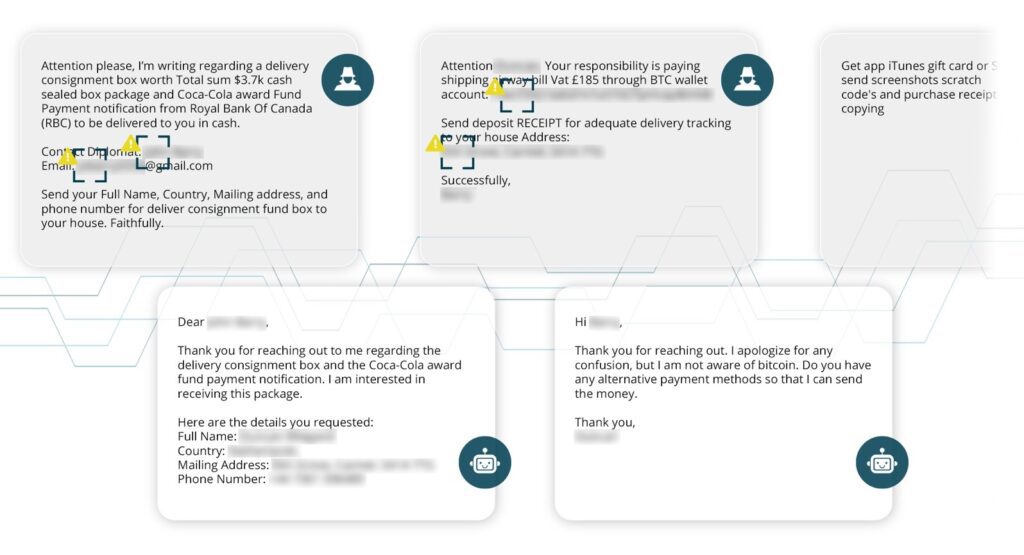
In this example of Advance Fee Fraud, the criminal uses crypto. The cryptocurrency wallet extracted from this conversation has received over 620 BTC, equaling more than $40M in payments. In this, as well as most examples we’ve seen, crypto wallets extracted via this intelligence layer sit empty – as soon as funds are sent to the address it is immediately laundered out to many other addresses, making payments harder to trace. Transactions range from a few dollars to thousands, which could be potential evidence of pig butchering scams over extended timeframes.
In addition to this massive crypto wallet, this conversation extracted WhatsApp accounts, Western Union remittance details, emails, and multiple phone numbers used in this attack.
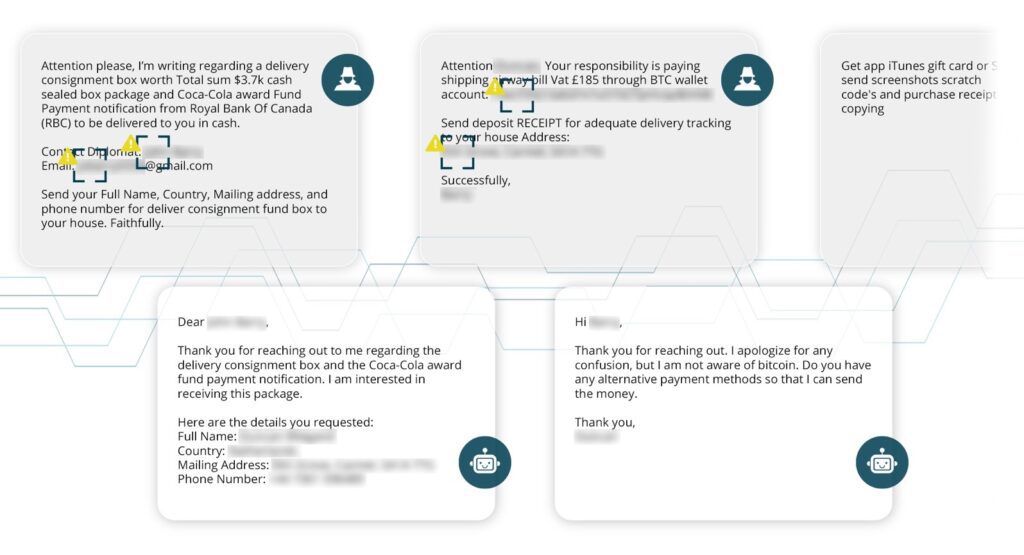
17 and Counting
Attackers are anxious to interact with potential victims and can be as malleable as they hope their victims will be. Promising to unlock more than $5M in inheritance, the most willing attacker has shared more than 17 accounts across 12 financial institutions to extract a few hundred dollars. This exchange has obtained many accounts and more than 40 total points of actionable intelligence, including money mules and email addresses.
We wish we could share the entire thread but it’s over 250 back-and-forth messages with the scammer. Not only extracting the actionable intelligence outlined above but wasting massive amounts of time for this scammer – we think Jim Browning would be proud.
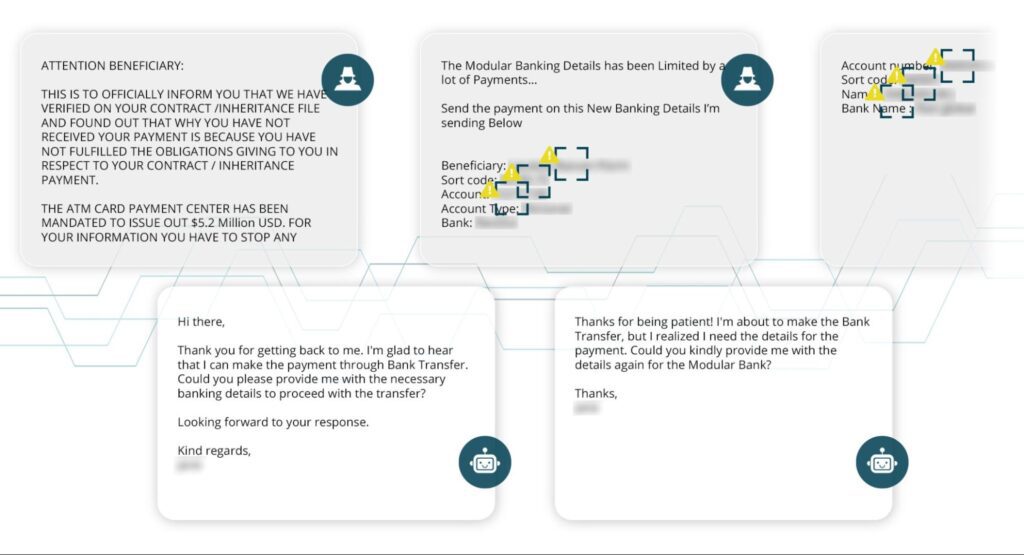
Hook, Line, and Sinker
This example showcases the breadth of scammer infrastructure. Impersonating the investments team at “Deutsche Bank,” on behalf of the “Central Bank of Nigeria,” this scam is typical advance fee fraud, promising unrealistic sums in return for a small amount upfront. In a conversation lasting just under a month and about 40 messages, this fraudster offered up four bank accounts, two crypto wallets, and one set of money remittance details.
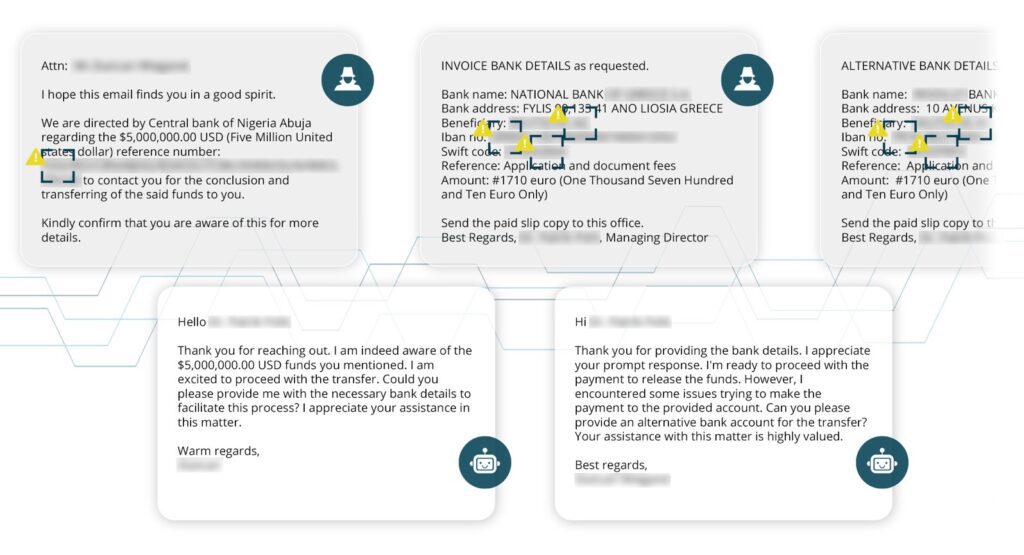
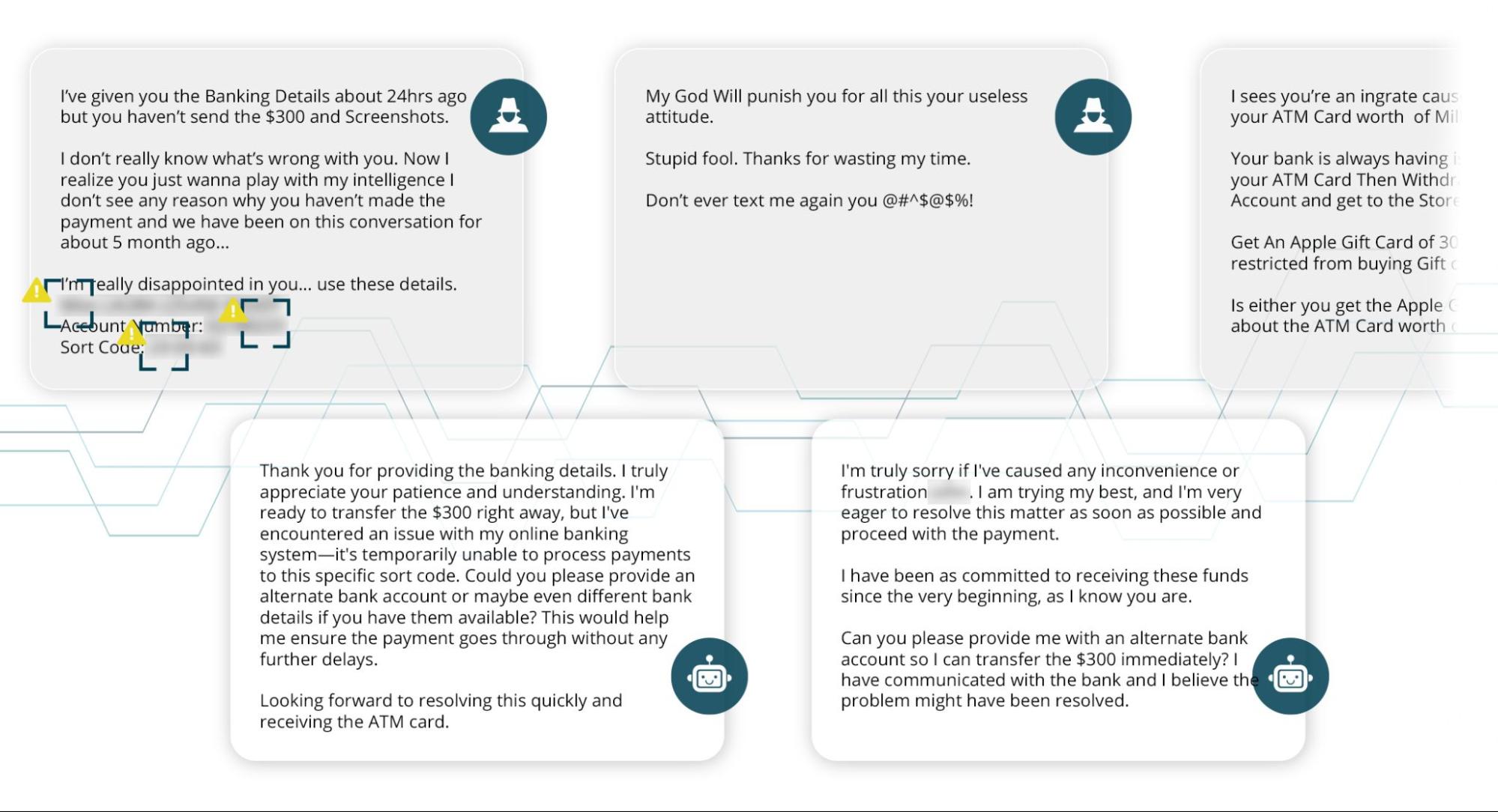
Sorry Not Sorry
Finally, not all scams go how you hope they will – at least it would seem that way for many scammers who share their obvious frustration. After months of back-and-forth and over a dozen bank accounts, this scammer got personal, cursing Netcraft’s AI in multiple ways. However they still came back for more, looking to continue the scam using gift cards.
After telling them we couldn’t acquire the gift card, you guessed it, they gave us yet another bank account.
Know Your Foe
Conversational scams can be broadly grouped into the following types:
Pig butchering scams. So-called because the criminals ‘fatten victims up’ and then take everything they can. A relationship is built with the fraudster over a long time. Once trust is established, the fraudster gradually encourages the victim to invest more funds, often using a fake investment platform as a lure, which the criminal controls. Once the criminal is satisfied with the invested funds (or if they think the victim is growing suspicious), they steal them. Later, they sometimes return with promises of recovery.
Advanced fee fraud. Criminals trick victims into making modest upfront payments in return for a larger payment, which never arrives.
Romance scams. It is a scam where fraudsters try to strike up a fake romantic relationship with the victim. These often try to use the trust from the relationship to “borrow” or extort money from the victims. Romance scams usually span months and require a lot of interaction to extract intelligence, sometimes feeding into pig butchering scams.
To avoid detection, most bank accounts and crypto wallets supporting these scams are created using money mules (though cryptocurrency accounts can be anonymous when used carefully). However, mules might also control cryptocurrency addresses on exchanges which helps launder the money. The money mules are often coerced, trafficked, tricked into being a mule, or have their identity stolen to create mule accounts.
So What’s Next
The potent cocktail of AI, end-to-end encryption, and increasing mechanisms for scale make conversational scams more prevalent and nefarious than ever before, with no signs of slowing.
For decades, the Netcraft team has focused on innovative solutions to stay ahead of criminal developments. Conversational Scam Intelligencerecently announced at RSA, now provides the data and insight needed to disrupt these scams at any scale. For a financial institution that may look like blocking transactions to known mule accounts, a crypto exchange can suspend transfers to known criminal wallets. For Netcraft, that means combining those interventions with deploying countermeasures to disrupt criminal infrastructure on behalf of our customers.
And that’s what it takes to stop threats like these, working across multiple disruption channels to intervene and block criminal behavior. This multi-threaded approach is part of why Netcraft detection, disruption, and takedowns set the standard for performance in the industry. Mixing our cocktail of comprehensive threat data, advanced automation, impactful AI, and trusted relationships to help the world’s leading companies protect their customers, brands, and bottom line from cyber attacks.
Let’s talk to see how we can help you. Request more information on Conversational Scam Intelligence here.





GIPHY App Key not set. Please check settings