WHAT COULD GO WRONG? – Hey.
A lack of encryption and easily enumerated IDs open users to a host of creepy attacks.

Shenzhen I 365 Tech
(An estimated) , 00 0 GPS trackers for monitoring the location of kids, seniors, and pets contain vulnerabilities that open users up to a host of creepy attacks, researchers from security firm Avast have found.
The $ 25 to $ 50 devices are small enough to wear on a necklace or stash in a pocket or car dash compartment. Many also include cameras and microphones. They’re marketed onAmazonand other online stores as inexpensive ways to help keep kids, seniors, and pets safe. Ignoring the ethics of attaching a spying device to the people we love, there’s another reason for skepticism. Vulnerabilities in the T8 Mini GPS Tracker Locator and almost 30 similar model brands from the same manufacturer, Shenzhen i 365 Tech, make users vulnerable to eavesdropping, spying, and spoofing attacks that falsify users’ true location.
Researchers at Avast Threat Labs found that ID numbers assigned to each device were based on itsInternational Mobile Equipment Identity, or IMEI. Even worse, during manufacturing, devices were assigned precisely the same default password of 123456. The design allowed the researchers to find more than 600, 00 0 devices actively being used in the wild with that password. As if that wasn’t bad enough, the devices transmitted all data in plaintext using commands that were easy to reverse engineer.
The result: people who are on the same network as the smartphone or Web-based app can monitor or modify sensitive traffic. One command that might come in handy sends a text message to a phone of the attacker’s choice. An attacker can use it to obtain the phone number tied to a specific account. From there, attackers on the same network could change the GPS coordinates the tracker was reporting or force the device to call a number of the attacker’s choice and broadcast any sound within range of its microphone. Other commands allowed devices to return to their original factory settings, including the default password, or to install attacker-chosen firmware.
Another command allows attackers to change the IP address of the server that the tracker communicates with. The Avast researchers exploited the weakness to set up aman-in-the-middle attackthat allowed them to permanently control the device. From that point on, attackers would no longer need to be connected to the same network as the smartphone or Web app. They would be able to view and modify all plaintext passing through their proxy.
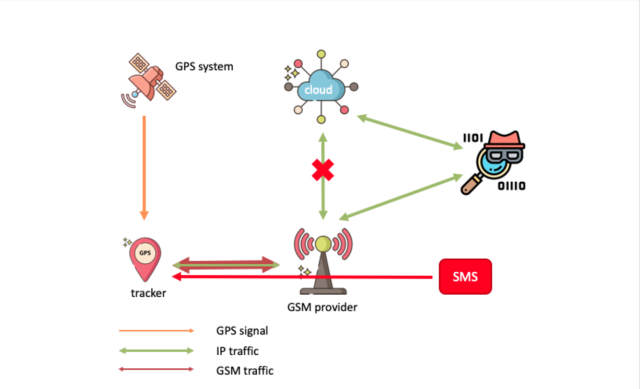
Enlarge/A diagram of the man-in-the-middle attack that allowed Avast researchers to divert GPS tracking data through a rogue server.
(Avast)
The researchers also determined that all data traveling between the GSM network to the cloud server was not only unencrypted but also unauthenticated. The only thing tying the device down was its IMEI. The researchers said they privately notified the vendor of the T8 Mini GPS tracker of the vulnerabilities on June 24 and never got a response. Attempts by Ars to reach company representatives were unsuccessful.
In a blog post scheduled togo liveThursday morning, the Avast researchers identified 29 generic model names of a subset of the 600, 00 0 Internet-connected trackers they found using a default password. They are:
(T)
A9
T8S
T 28
TQ
A 16
A6
3G
A 18
A 21
T (A) A 12
A 19
A 20
A (S) S1
P1
FA 23
A 107
RomboGPS
PM 01
A (P) PM 02
A (X) PM 03
WA3
P1-S
S6
S9
GPS trackers can provide protection and peace of mind in the right cases, which at a minimum require fully informed consent of the people being tracked. But the Avast research demonstrates how the capabilities of these devices can cut both ways and make users more vulnerable than if they used no protection at all. People who have bought one of the vulnerable devices should stop using it at once.





GIPHY App Key not set. Please check settings