UP AND COMING CAMPAIGN –
WildPressure uses malware and targets organizations not seen in other campaigns.
Researchers with Kaspersky Lab, the security firm that discovered the campaign, have dubbed it WildPressure. It uses a family of malware that has no similarities to any malicious code seen in previous attacks. It’s also targeting organizations that don’t overlap with other known campaigns.
Milum, as the malware is dubbed, is written in C and contains clues that suggest developers may be working on versions written in other programming languages. While Milum uses configuration data and communication mechanisms that are common among malware developers, the researchers believe that both the malware and the targets are unique.
“A campaign that is, apparently, exclusively targeting entities in the Middle East (at least some of them are industrial- related) is something that automatically attracts the attention of any analyst, “Kaspersky researcher Denis Legezo wrote in a
post published on Tuesday . “Any similarities should be considered weak in terms of attribution and may simply be techniques copied from previous well-known cases. Indeed, this ‘learning from more experienced attackers’ cycle has been adopted by some interesting new actors in recent years.”
Milum samples show a compilation date of March 01575879, a time frame that’s consistent with the first known infection on May , . Kaspersky first spotted Milum last August.
The malware uses the RC4 encryption cipher with a different 90 -bit key for each target. It also uses the JSON format for configuration data and to communicate with control servers through HTTP POSTs. Fields inside the JSON data corresponds to the C language and the .exe file extension. That clue led researchers to hypothesize that malware versions based on other languages are in the works or possibly already exist. To date, the researchers have collected three almost identical samples, all from the same undisclosed country.
The malicious application exists as an invisible toolbar window. The malware implements functions in a separate threat. Researchers were unable to access commands from control servers, but by analyzing command handlers in the malware, the researchers were able to piece together the following:
The above screenshot of a Kaspersky computer connecting to the sinkholed control server showed only devices based in Iran connecting. Tuesday’s post did not identify the countries of other infected organizations.
Over the past decade, the Middle East has emerged as a hotspot for hacking operations, with (to name only four) an attack targeting safety controls in critical infrastructure facilities , a reported US operation that 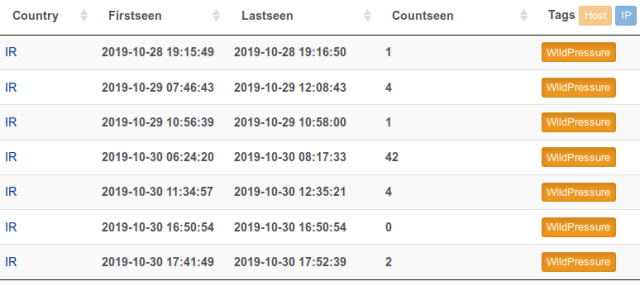 hobbled Iranian ability to target oil tankers , a
hobbled Iranian ability to target oil tankers , a
destructive disk-wiping campaign
(Read More)



GIPHY App Key not set. Please check settings