

 Jeremy Morgan
Jeremy Morgan


 Jeremy Morgan
Jeremy Morgan  Note: Pluralsight is currently having a Free Weekend , so you can take any of their courses this weekend for free. Including a huge Security library !!
Note: Pluralsight is currently having a Free Weekend , so you can take any of their courses this weekend for free. Including a huge Security library !! 
 I was casually doing a security audit on my blog ( JeremyMorgan.com recently and decided to look a little deeper into my security logs. With a bit of Linux command line kung fu, some Golang, and Google sheets, I was able to get a pretty good idea of where the attacks are coming from.
I was casually doing a security audit on my blog ( JeremyMorgan.com recently and decided to look a little deeper into my security logs. With a bit of Linux command line kung fu, some Golang, and Google sheets, I was able to get a pretty good idea of where the attacks are coming from.  To start, I’m using CentOS to host my site, so I checked out / var / log / secure. This log is where authentication logs are stored on my server.
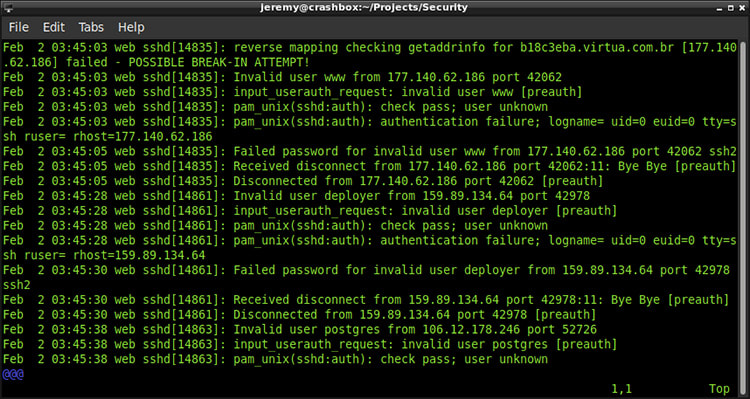
To start, I’m using CentOS to host my site, so I checked out / var / log / secure. This log is where authentication logs are stored on my server.  This is what the log file looks like:
This is what the log file looks like: 



 and with 348, lines it’s not likely I’m going to manually look around much. Let’s automate this a bit.
and with 348, lines it’s not likely I’m going to manually look around much. Let’s automate this a bit. 
Getting the IP Address of attackers
I wanted to extract the IP address of attackers from this file. That way I can block them. 
 I started to mess around with Linux commands until I came up with this script .
I started to mess around with Linux commands until I came up with this script . 
What it does is pretty simple, it’s going to look for these strings:
declare -a badstrings=(“Failed password for invalid user” “input_userauth_request: invalid user” “pam_unix (sshd: auth): check pass; user unknown” “input_userauth_request: invalid user” “does not map back to the address” “pam_unix (sshd: auth): authentication failure” “input_userauth_request: invalid user” “reverse mapping checking getaddrinfo for” “input_userauth_request: invalid user” )
These are strings that identify logs of failed attacks. If they put in the wrong username or tried some other form of attack, it would have one of these strings. 
So we loop through that list and search for these strings, then extract an IP address from the line the string exists in. 
cat / var / log / secure | grep "$ i" | grep -E -o "([0-9] {1,3} [.]) {3} [0-9] {1,3}" | awk '{print $ 0}' | sort | uniq>> "temp.txt"
It then dumps the IP into a (temp.txt) file. It will do this for all of the messages I have in my "badstrings" list. 
That text file had a ton of duplicates in it, so I removed the duplicates and put only the unique IPs into a file: 
# grab unique ips from temp and put them in a file cat "temp.txt" | sort | uniq> "badguyips.txt" # remove the temp file rm "temp.txt"
Cool, now I have a list of IP addresses ready to go. 

Yikes, I have (1, IP addresses here. 

Now I want to block these IP addresses. Since I'm running iptables, I can just drop them with this simple script:  #! / bin / bash
#! / bin / bash 
Cool. Now the attackers blocked from my server. 
Then I got curious. Where the heck are these attacks coming from? 

Since I have a list of IP addresses, I thought I'd run them against a database like Maxmind
to find some location information. So I did just that.
 I wrote this Golang program called "find the bad guys" that would go through the text file of IP addresses, and look up their location information, then write it to a series of text files.
I wrote this Golang program called "find the bad guys" that would go through the text file of IP addresses, and look up their location information, then write it to a series of text files.
 I wrote out locations based on:
I wrote out locations based on:  (Continent) (Countries) (Cities) (Subdivisions of Cities)
(Continent) (Countries) (Cities) (Subdivisions of Cities)
I wanted to see where the attacks are coming from and share. that information. so I ran the program I built, and now have some helpful lists of location information: 

 Continents
Continents  So now I want to take a look at continents.txt.
So now I want to take a look at continents.txt. 


 Well, that's going to be a problem, there are some duplicates.
Well, that's going to be a problem, there are some duplicates. 
 I can run a quick command and get unique values:
cat continents | sort | uniq
I can run a quick command and get unique values:
cat continents | sort | uniq The results should come as no surprise if you've ever looked at a globe: 



 But I want to see how many attacks from each continent. So I call on my old friend awk for that:
But I want to see how many attacks from each continent. So I call on my old friend awk for that:  awk -F ' n' '{print $ 0}' continents.txt | sort | uniq -c
awk -F ' n' '{print $ 0}' continents.txt | sort | uniq -c 


Pretty sweet, right? So I'll remove the leading spaces, insert a comma after the count and drop it into a text file. awk -F ' n' '{print $ 0}' continents.txt | sort | uniq -c | awk '{$ 1=$ 1}; 1' | sed -r 's / s /, /'> contintent-totals.txt 


 Now I can drop it into Google sheets.
Now I can drop it into Google sheets. 



 and get this nice chart:
and get this nice chart: 

This is the process I repeat for the other locations (country, city, subdivision), so I won't repeat it. So here are my results: 


Countries 
 Here are the top 25 countries attackers are coming from: (China 365) (United States) 178) (France) 120) (India)
Here are the top 25 countries attackers are coming from: (China 365) (United States) 178) (France) 120) (India)
(Singapore) ) (South Korea) 50) (Germany) 50) (Russia) 50) (Brazil) ) (United Kingdom) 44) Cities 


Attacks per city are a little more aggregated.  (Beijing) 76) (Shanghai) 68)
(Beijing) 76) (Shanghai) 68)
(Hefei) 44) (Amsterdam) ) (Bengaluru) ) (London) ) (Xinpu) ) (Clifton) )
- (North Bergen (9)) But still pretty interesting.
 Subdivisions
Subdivisions 
This one is aggregated even more. But it drills down a bit more. Here are the top (subdivisions attackers are coming from:
(Beijing) 184  (Shanghai) 078)
(Shanghai) 078)
(Anhui) 44) (England) 40 (Jiangsu) 042 (New Jersey) ) (North Holland) ) (California) 36  (Sao Paulo) 36) (Karnataka) 035) Conclusion
(Sao Paulo) 36) (Karnataka) 035) Conclusion
Great things always come from curiosity. I'm curious about what other kinds of patterns and data I can extract from this, so I'm going to keep experimenting and playing with it.
If you decide you want to do this for your website, try it these steps, and [Let me know] if you need any help with it.
And, as a reminder, Pluralsight is having a free weekend
, and they have tons of security (related courses) you can take right now
that will help you secure your website and keep attackers out. ()  Jeremy Morgan
Jeremy Morgan
Silicon Forest Developer / hacker. I write about .NET, DevOps, and Linux mostly. Once held the world record for being the youngest person alive. 

 With our technology skills platform, companies can upskill teams and increase engineering impact.
With our technology skills platform, companies can upskill teams and increase engineering impact. 


(Read More)


 I started to mess around with Linux commands until I came up with this script .
I started to mess around with Linux commands until I came up with this script . 
These are strings that identify logs of failed attacks. If they put in the wrong username or tried some other form of attack, it would have one of these strings. 
So we loop through that list and search for these strings, then extract an IP address from the line the string exists in. 
cat / var / log / secure | grep "$ i" | grep -E -o "([0-9] {1,3} [.]) {3} [0-9] {1,3}" | awk '{print $ 0}' | sort | uniq>> "temp.txt"
It then dumps the IP into a (temp.txt) file. It will do this for all of the messages I have in my "badstrings" list. 
That text file had a ton of duplicates in it, so I removed the duplicates and put only the unique IPs into a file: 
# grab unique ips from temp and put them in a file cat "temp.txt" | sort | uniq> "badguyips.txt" # remove the temp file rm "temp.txt"
Cool, now I have a list of IP addresses ready to go. 

Yikes, I have (1, IP addresses here. 

Now I want to block these IP addresses. Since I'm running iptables, I can just drop them with this simple script:  #! / bin / bash
#! / bin / bash 
Cool. Now the attackers blocked from my server. 
Then I got curious. Where the heck are these attacks coming from? 

Since I have a list of IP addresses, I thought I'd run them against a database like Maxmind
to find some location information. So I did just that.
 I wrote this Golang program called "find the bad guys" that would go through the text file of IP addresses, and look up their location information, then write it to a series of text files.
I wrote this Golang program called "find the bad guys" that would go through the text file of IP addresses, and look up their location information, then write it to a series of text files.
 I wrote out locations based on:
I wrote out locations based on:  (Continent) (Countries) (Cities) (Subdivisions of Cities)
(Continent) (Countries) (Cities) (Subdivisions of Cities)
I wanted to see where the attacks are coming from and share. that information. so I ran the program I built, and now have some helpful lists of location information: 

 Continents
Continents  So now I want to take a look at continents.txt.
So now I want to take a look at continents.txt. 


 Well, that's going to be a problem, there are some duplicates.
Well, that's going to be a problem, there are some duplicates. 
 I can run a quick command and get unique values:
cat continents | sort | uniq
I can run a quick command and get unique values:
cat continents | sort | uniq The results should come as no surprise if you've ever looked at a globe: 



 But I want to see how many attacks from each continent. So I call on my old friend awk for that:
But I want to see how many attacks from each continent. So I call on my old friend awk for that:  awk -F ' n' '{print $ 0}' continents.txt | sort | uniq -c
awk -F ' n' '{print $ 0}' continents.txt | sort | uniq -c 


Pretty sweet, right? So I'll remove the leading spaces, insert a comma after the count and drop it into a text file. awk -F ' n' '{print $ 0}' continents.txt | sort | uniq -c | awk '{$ 1=$ 1}; 1' | sed -r 's / s /, /'> contintent-totals.txt 


 Now I can drop it into Google sheets.
Now I can drop it into Google sheets. 



 and get this nice chart:
and get this nice chart: 

This is the process I repeat for the other locations (country, city, subdivision), so I won't repeat it. So here are my results: 


Countries 
 Here are the top 25 countries attackers are coming from: (China 365) (United States) 178) (France) 120) (India)
Here are the top 25 countries attackers are coming from: (China 365) (United States) 178) (France) 120) (India)
(Singapore) ) (South Korea) 50) (Germany) 50) (Russia) 50) (Brazil) ) (United Kingdom) 44) Cities 


Attacks per city are a little more aggregated.  (Beijing) 76) (Shanghai) 68)
(Beijing) 76) (Shanghai) 68)
(Hefei) 44) (Amsterdam) ) (Bengaluru) ) (London) ) (Xinpu) ) (Clifton) )
- (North Bergen (9)) But still pretty interesting.
 Subdivisions
Subdivisions 
This one is aggregated even more. But it drills down a bit more. Here are the top (subdivisions attackers are coming from:
(Beijing) 184  (Shanghai) 078)
(Shanghai) 078)
(Anhui) 44) (England) 40 (Jiangsu) 042 (New Jersey) ) (North Holland) ) (California) 36  (Sao Paulo) 36) (Karnataka) 035) Conclusion
(Sao Paulo) 36) (Karnataka) 035) Conclusion
Great things always come from curiosity. I'm curious about what other kinds of patterns and data I can extract from this, so I'm going to keep experimenting and playing with it.
If you decide you want to do this for your website, try it these steps, and [Let me know] if you need any help with it.
And, as a reminder, Pluralsight is having a free weekend
, and they have tons of security (related courses) you can take right now
that will help you secure your website and keep attackers out. ()  Jeremy Morgan
Jeremy Morgan
Silicon Forest Developer / hacker. I write about .NET, DevOps, and Linux mostly. Once held the world record for being the youngest person alive. 

 With our technology skills platform, companies can upskill teams and increase engineering impact.
With our technology skills platform, companies can upskill teams and increase engineering impact. 


(Read More)








GIPHY App Key not set. Please check settings