CERT-AGID 01 – 07 June 2024: 202 IOCs and an unknown malware campaign
Jun 10, 2024
Attacks, Malware, News, Phishing, Vulnerability
This week, the CERT-AGID identified and analyzed overall 31 malicious campaigns in the Italian context, of which 18 specifically aimed at Italian targets and 13 of a general nature which nevertheless involved Italy. Its accredited bodies have been provided with the relevant 202 indicators of compromise (IOC).
The most relevant topics of the week
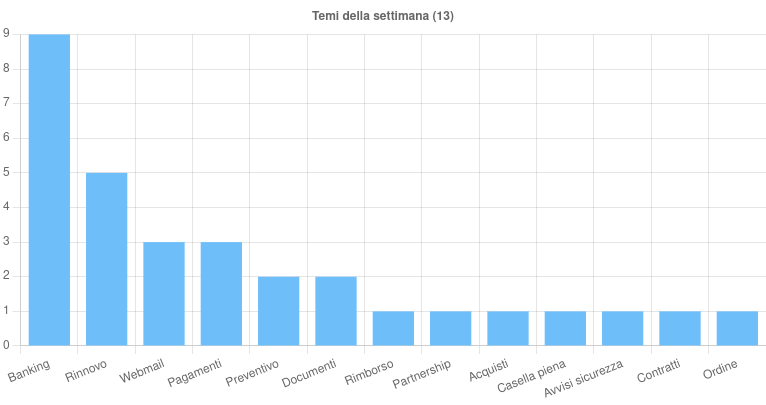
This week they were identified 13 themes used to spread malicious campaigns in Italy. Among these, the theme Banking it has often been exploited in phishing campaigns aimed mainly at customers of Italian banks, post offices, credit and prepaid cards, and has also been used to spread the Irata malware through a smishing campaign.
The theme of Renewal was used in phishing campaigns linked to Aruba and OVHcloud, taking advantage of the lack of confirmation of the domain renewal. The theme Webmail it was predominantly used for phishing campaigns targeting cPanel users. The other themes supported various malware and phishing campaigns.
A case of particular interest was the phishing campaign conveyed via PEC specifically registered, which CERT-AGID counteracted with the help of the PEC Managers.
Fonte: CERT-AGID
Malware of the week
This week in Italy they were observed five malware families. Of particular note are the campaigns relating to Guloaderwith three identified campaigns, two of which are specifically Italian, on topics such as “Estimate”, “Payments” and “Documents”, conveyed via email with IMG, PDF and ZIP attachments containing VBS scripts.
AgentTesla saw two campaigns, one Italian and one general, on “Contracts” and “Purchases” respectively, spread via email with IMG and GZ attachments.
A campaign was then observed that spread a malware still unknownexploiting the “Payments” theme and conveyed via email with a ZIP attachment containing a JAR archive disguised as IMG.
Angry was the protagonist of an Italian “Banking” themed smishing campaign, which distributes an APK file via a link. Finally there was also an Italian campaign themed “Preventive”, spread by Remcos via email with RAR attachments.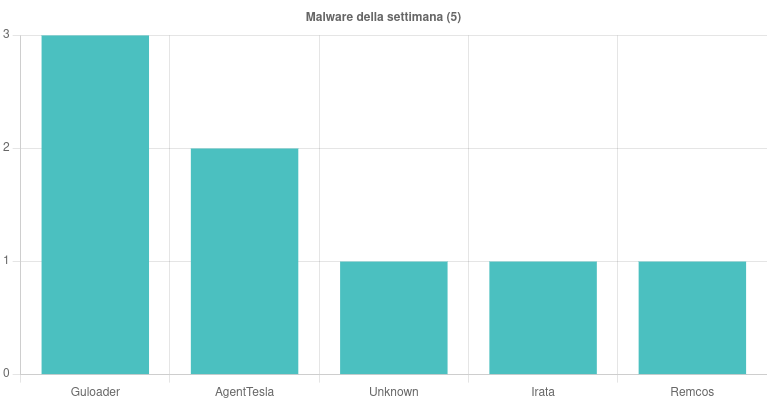
Fonte: CERT-AGID
Phishing of the week
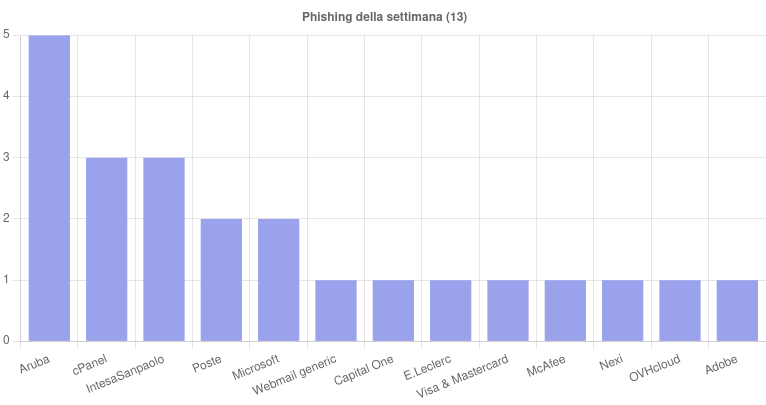
This week they got involved 13 brands in phishing campaigns. Of particular importance were the numerous campaigns aimed at Aruba e Intesa Sanpaolowho mainly exploited the excuse of non-renewal of the domain and the need to carry out banking operations.
We also note a phishing campaign carried out via fraudulently registered PEC email, and the aforementioned banking-themed smishing aimed at spreading the Irata ransomware.
Fonte: CERT-AGID
Formats and distribution channels
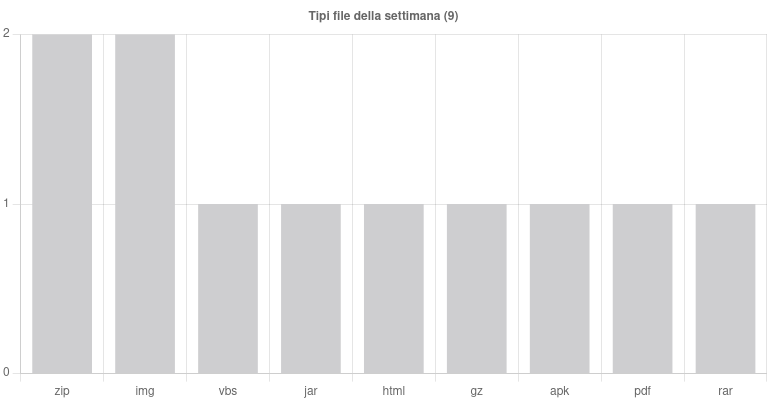
This week the attacks were carried out through 9 different file types. The most popular were ZIP and IMG (2). With a single use we find VBS, JAR, HTML, GZ, APK, PDF and RAR files.
Regarding the distribution channels, the emails were used 30 timesPECs only once.




GIPHY App Key not set. Please check settings