GOT CERT VALIDATION? –
Attack demoed less than hours after disclosure of bug-breaking certificate validation.
Dan Goodin – Jan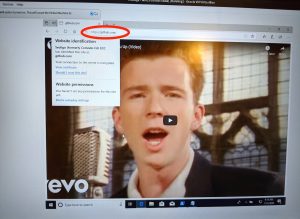 ,
,
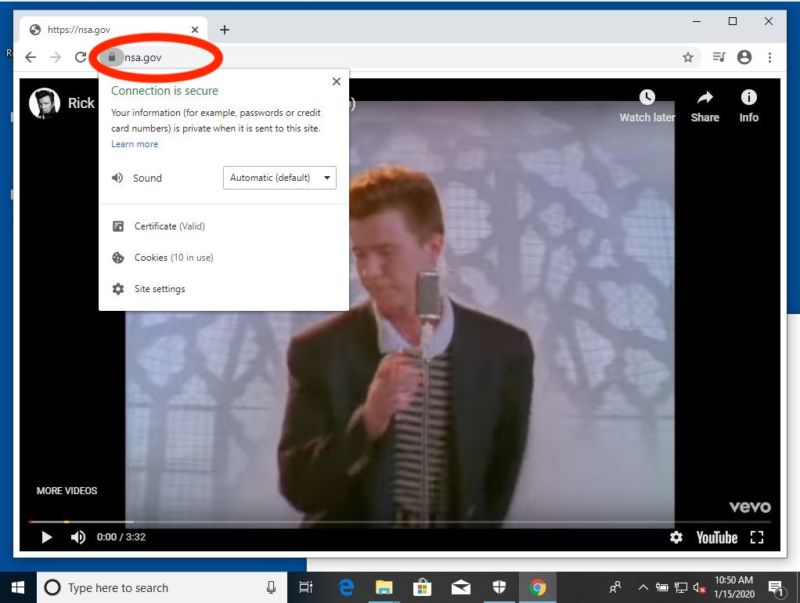
Researcher Saleem Rashid on Wednesday tweeted images of the video “Never Gonna Give You Up,” by s heartthrob Rick Astley, playing on Github.com and NSA.gov. The digital sleight of hand is known asRickrolling
Rashid told me his exploit uses about 300 lines of code but that he could compress it down to 10 lines if he wanted to remove a “few useful tricks” his attack has. While there are constraints and several potentially difficult requirements in getting the exploit to work in real-world, adversarial conditions (more about that later), Wednesday’s proof-of-concept attack demonstrates why the NSA assesses the vulnerability as “severe”and said sophisticated hackers could understand how to exploit it “quickly.” “Fairly terrifying”Other researchers shared the NSA’s sense of urgency.
The flaw involves the way the new versions of Windows check the validity of certificates that use elliptic-curve cryptography
The attacker examines the specific ECC algorithm used to generate the root-certificate public key and proceeds to craft a private key that copies all of the certificate parameters for that algorithm except for the point generator. Because vulnerable Windows versions fail to check that parameter, they accept the private key as valid. With that, the attacker has spoofed a Windows-trusted root certificate that can be used to mint any individual certificate used for authentication of websites, software, and other sensitive properties.
The The behavior is tantamount to a law enforcement officer who checks someone’s ID to make sure it properly describes the person’s height, address, birthday, and face but fails to notice that the weight is listed as pounds when the person clearly weighs less than half that.
“It’s such a strange bug, because it’s like they’re only halfway checking something that is at the root of the entire trust system, “White said. “It’s a core part of the whole chain of trust.”For more detailed technical explanations of the bug, see posts hereandhere, and the Twitter threadhere (*************. ********** The caveatsAs noted earlier, there are several requirements and constraints that significantly raise the bar for Rashid’s attack to work in real-world uses by an adversary. The first is that it most likely requires an activeman-in-the-middleattack. These types of attacks, which modify data as it passes through networks, may be difficult to carry out. An alternative to an active MitM is to convince a target to click on a fake URL. This method is much easier, but it also requires some targeting. (It wouldn’t apply to attacks against websites or other servers that require a certificate from the connecting client.)
The exploit also requires that the target has recently visited a site with a (transport layer securitycertificate that’s chained to an ECC-signed root certificate. That’s because the root certificate must already be cached by the targeted system. In the event a targeted system does not have the root certificate cached, Rashid said, an attacker could still pull off an exploit by adding JavaScript that accesses a site chained to the root certificate.
 Another constraint: Chrome uses a mechanism known as certificate pinningfor google.com and a variety of other sensitive websites. Pinning requires that the certificate authenticating a website contain a specificcryptographic hash, even if the certificate offered is otherwise valid. This measure would prevent exploits from working when they spoofed protected sites.
Another constraint: Chrome uses a mechanism known as certificate pinningfor google.com and a variety of other sensitive websites. Pinning requires that the certificate authenticating a website contain a specificcryptographic hash, even if the certificate offered is otherwise valid. This measure would prevent exploits from working when they spoofed protected sites.
Despite the requirements and limitations, the vulnerability is serious. As NSA officials put it in the above-linked advisory:The vulnerability places Windows endpoints at risk to a broad range of exploitation vectors. NSA assesses the vulnerability to be severe and that sophisticated cyber actors will understand the underlying flaw very quickly and, if exploited, would render the previously mentioned platforms as fundamentally vulnerable. The consequences of not patching the vulnerability are severe and widespread. Remote exploitation tools will likely be made quickly and widely available. Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners.
**************************************
The vulnerability may not pose as extreme a threat as those caused by the (Heartbleed flaw in) that allowed attackers to steal private keys, passwords, and other highly sensitive data from hundreds of thousands of vulnerable sites. But because of the breadth of security measures foiled by the Microsoft vulnerability, it’s worse even than Apple’s critical
goto fail flaw, which prevented iOS and macOS systems from detecting invalid TLS certificates served by websites. That makes CVE – 22048619 – 603 one of the most severe vulnerabilities in recent memory.************************************************** (Post updated to correct description of certificate pinning and discussion of man-in-the-middle attacks.)
(****************************************************(Read More) ********************************************




GIPHY App Key not set. Please check settings