
Enlarge/Louisiana state agencies were taken offline during the response to a Ryuk ransomware attack but are now largely up and running again thanks to backups.
In October, the (Federal Bureau of Investigation issued a warning) of increased targeting by ransomware operators of “big game” —targets with deep pockets and critical data that were more likely to pay ransoms to restore their systems. The past week has shown that warning was for good reason.
On November 18, a ransomware attack caused Louisiana’s Office of Technology Services to shut down parts of its network, including the systems of several major state agencies. These included the governor’s office, the Department of Health (including Medicare systems), the Department of Children and Family Services, the Department of Motor Vehicles, and the Department of Transportation. Louisiana Governor John Bel Edwards activated the state’s cybersecurity response team.
Today, we activated the state’s cybersecurity team in response to an attempted ransomware attack that is affecting some state servers. The Office of Technology Services identified a cybersecurity threat that affected some, but not all state servers.# lagov# lalege
– John Bel Edwards (@LouisianaGov) (November) , 2019
While some services have been brought back online — in some cases, within hours — others are still in the process of being restored. Most of the interrupted services were caused by “our aggressive actions to combat the attack,” according to Louisiana Commissioner of Administration Jay Dardenne. “We are confident we did not have any lost data, and we appreciate the public’s patience as we continue to bring services online over the next few days.”
We will Ryuk you (or DopplelPaymer you)
The state did not pay the ransom demanded by attackers, who — based on the analysis of several researchers — were using a variant of the same Ryuk ransomware used in attacks on several Louisiana school districts’ networks in July. That attack prompted Gov. Edwards todeclare a state of emergencyto allow for state agencies to assist local governments in their recovery from the attack. Ryuk attacks this summer also affectedGeorgia’s court system and at least two Florida cities.
On November 15, the Charles-Nicolle University (CHU) Hospital in Rouen, France,was hit by ransomware that spread across five sites. The hospital was forced to shut down its networks to prevent the malware from spreading, according to a report from Le Monde, and staff were forced to use paper and pencil for tracking patients. While there were reports of a demand of a ransom payment of 1, 500 euros for each of the over 6, 00 0 computers affected at the hospital, a hospital spokesperson denied that a ransom demand had been made and said none would be paid. As of November 18, about 25% of the hospital’s applications had been restored.
Also on November 15, the government of the Canadian territory of Nunavut suffered a ransomware outbreak that affected about 5, 00 0 computers territory-wide. That attack, according to Nunavut government spokesperson Chris Puglia, used a variant of DoppelPaymer ransomware; the same malware hitMexico’s state-owned oil company PEMEXon November 12.
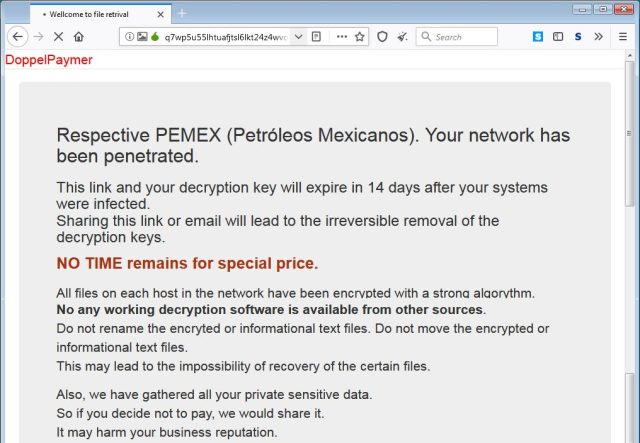
Enlarge/The PEMEX Tor payment site was widely posted on social media.
Despite documentation of the Pemex attack, company executives have continued to deny the company was affected.
📌 # Pemex🇲🇽reitera hacer caso omiso a boletines apócrifos que circulan en medios de información y redes sociales. Toda la información referente a la empresa productiva del Estado es publicada únicamente por vías institucionales y las redes oficiales.
– Petróleos Mexicanos (@Pemex) (November) , 2019
According to security researcher Vitali Kremez, both the Nunavut and PEMEX ransomware attacks used the same Tor “hidden service” Web portal. Within the portal, the actors behind the ransomware left the note rationalizing their attack: “We don’t care who you are and why this happens. No one died. That’s all.”
While they may or may not use the same type of communications with victims as opportunistic attacks — DoppelPaymer uses a Web portal similar to those used by opportunistic attacks, while Ryuk keeps its communications over email — both of these attacks were targeted rather than opportunistic. While they may use similar initial compromise methods as opportunistic attacks (phishing, automated vulnerability scanning and exploitation, or attacks using Remote Desktop Protocol), targeted attacks are the product of researching a compromised network and releasing the ransomware only after determining who the target is ( and how likely they will be to pay). As a result, they require less work for attackers because they reduce the number of victims they need to communicate with.
Diminishing returns due to backups
While it’s not certain whether PEMEX did or did not pay the ransom demanded from the company, the others did not pay — largely because they had disaster recovery and backup systems in place and were able to restore functionality after it was interrupted. And that, according to senior FBI cyber officials, is a key to ending the continuing growth of targeted ransomware attacks.
In a press briefing attended by Ars Technica, senior cyber officials of the FBI speaking on background said that the only real way to stop ransomware attacks was improved “cyber hygiene.” That includes backups and software updates. As part of its effort to help raise state and local agencies’ awareness around ransomware, the FBI recentlyhosted a ransomware summit in Pittsburghat Carnegie Mellon University.
But because of a number of issues, state and local agencies, as well as hospitals, have been an easy target for ransomware operators because of their reliance on legacy systems and lack of organic information security skills. This year alone, there have been over 100 reported ransomware attacks against state and local governments.







GIPHY App Key not set. Please check settings