COMEUPPANCE –
Hackers are behind attacks that wreak destruction and steal hundreds of millions of dollars.
Dan Goodin –)

Enlarge/Hacking for their home country, we guess.
The Trump administration is sanctioning three North Korean hacking groups widely accused of carrying out attacks that targeted critical infrastructure and stole millions of dollars from banks in cryptocurrency exchanges, in part so the country could finance its weapons and missiles programs.
All three of the groups are controlled by North Korea’s primary intelligence agency, the Reconnaissance General Bureau, or RGB, officials with the US Department of Treasury said in astatement published on Friday. Collectively, the groups are behind a host of cyber attacks designed to spy on adversaries and generate revenue for nuclear weapons and ballistic missile programs.
“Treasury is taking action against North Korean hacking groups that have been perpetrating cyber attacks to support illicit weapon and missile programs,” Sigal Mandelker, Treasury under-secretary for terrorism and financial intelligence, said in Friday’s statement. “We will continue to enforce existing US and UN sanctions against North Korea and work with the international community to improve cybersecurity of financial networks.”
The best-known of the three sanctioned groups is Lazarus, the name given to a team created as early as 2007 that targets militaries, governments, and companies in the financial, manufacturing, publishing, media, entertainment and shipping industries. The FBI tied Lazarus to the2014 hack of Sony Picturesthat destroyed data on thousands of company computers and published embarrassing emails from company executives to avenge a film that depicted the assassination of North Korea’s leader.
But the best-known work widely attributed to Lazarus was theWannaCry ransom worm outbreak in 2017. The malware used a Windows exploit developed by andlater stolen from the National Security Agencythat allowed the worm to spread rapidly from computer to computer with no user interaction.
Within hours, WannaCry had spread to 150 countries and shut down an estimated 300, 00 0 computers. Hospitals in the UK were hit particularly hard, leading to the cancellation of more than 19, 00 0 appointments and costing the country National Health Service more than $ (million.
The new sanctions also apply to two Lazarus subgroups. The first is known as Bluenoroff, which was formed as a means to earn revenue in the wake of increased global sanctions against the North Korean government. This is the group that was behind a 2016 hack on a Bangladesh central bank that almost got away with stealing $ 851 million. A typographical error prevented the illicit transaction from going through, but the attackers still made off with $ 81 million. Bluenoroff has also carried out successful hacks against banks in India, Mexico, Pakistan, the Philippines, South Korea, Taiwan, Turkey, Chile, and Vietnam.
Security firms includingSymantecandFireEyehave chronicled the work of this Lazarus subgroup as it systematically exploited weaknesses in the SWIFT payment network used by banks around the world. The name Bluenoroff wascoined in (by researchers from Kaspersky Lab) , who were the first to attribute the group as a standalone subunit of Lazarus. The group’s name was based on atool it used called “nroff_b. exe. ”
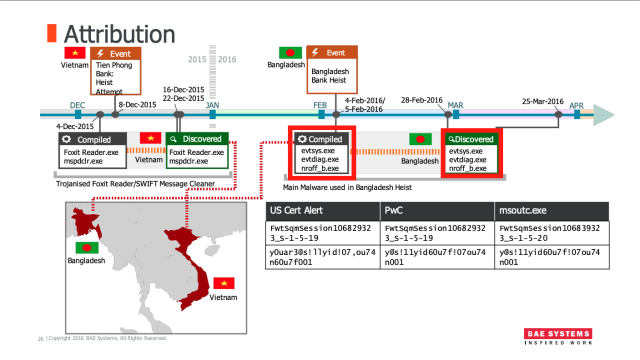
Enlarge/The tool called nroff_b.exe is highlighted in red.
The other Lazarus subgroup is known as “Andariel.” It focuses on hacks targeting foreign businesses, financial services, and government agencies . Security companies first noticed Adariel around 2015 when it hit targets in South Korea. The team has been responsible for attempts to steal bank card information by hacking into ATM networks to withdraw cash or steal data that could be sold to other criminals. The group, which was discovered by South Korea’s Internet and Security Agency, or Kisa, is also responsible for developing malware to hack online poker and gambling sites.
Trend Micro has a useful breakdown of the three North Korean hacking groupshere.
Friday’s statement said North Korean hacking operations have also targeted virtual asset providers and cryptocurrency exchanges, possibly in an attempt to obfuscate revenue streams used to support the countries weapons programs. The statement also cited industry reports saying that the three North Korean groups likely stole about $ 571 million in cryptocurrency from five exchanges in Asia between January (and September) . News agenciesincluding Reutershave cited a United Nations report from last month that estimated North Korean hacking has generated $ 2 billion for the country weapons of mass destruction programs.
It’s not clear how a new round of sanctions will affect an impoverished nation that is already ostracized by most of the world. And if the UN’s $ 2 billion estimate is correct, it’s hard to think Friday’s move will have any practical effect.





GIPHY App Key not set. Please check settings