xHelper came to light last May when a researcher from security firm Malwarebytes published this brief profile . Three months later, Malwarebytes provided a deeper analysis after the company Android antivirus app detected xHelper on , 02 Devices mostly located in the US, making the malware one of the top Android threats. The encryption and heavy obfuscation made analysis hard, but Malwarebytes researchers ultimately concluded that the main purpose of the malware was to act as a backdoor that could remotely receive commands and install other apps.
On Wednesday, Malwarebytes published a new post that recounted the lengths one Android user took to rid her device of the malicious app. In short, every time she removed two xHelper variants from the device, the malware would reappear on her device within the hour. She reported that even performing a factory reset was not enough to make the malware go away.
Blind alleys
Company researchers initially suspected that pre-installed malware was the culprit. They eventually dropped that theory after the user performed a technique that prevented system apps from running. Malwarebytes analysts later saw the malware indicating that Google Play was the source of the reinfections, but they ruled out this possibility after further investigation.
Eventually (and with the help of the Android user), company researchers finally identified the source of the reinfections: several folders on the phone that contained files that, when executed, installed xHelper. All of the folders began with the string com.mufc. To the researchers ’surprise, these folders weren’t removed even though the user performed a factory reset on the device.
“This is by far the nastiest infection I have encountered as a mobile malware researcher,” Malwarebytes’ Nathan Collier wrote in Wednesday’s post. “Usually a factory reset, which is the last option, resolves even the worst infection. I cannot recall a time that an infection persisted after a factory reset unless the device came with pre-installed malware. ”
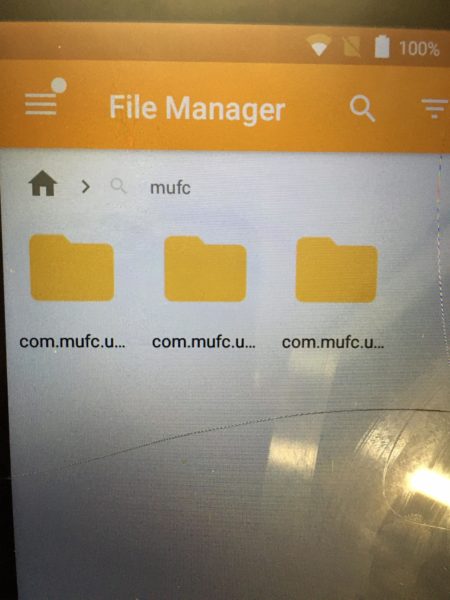
Collier still isn’t sure how the mufc folders came to reside on the phone in the first place or why they weren ‘t deleted during factory reset. In October, security firm Symantec also reported that users were complaining that factory resets did not kill xHelper , but company researchers were also unable to explain why. One theory, Collier said, is that an xHelper variant installed the folders and made them appear as an SD card that was not affected by the factory reset (the user reported that her device did not have an SD card).
“I was under the assumption that files / directories were removed after a factory reset, but this proves that some things can be left over, ”Collier wrote in an email. “There are still a lot of unknowns with this one. We’re just glad to have a resolution for our customers who may be struggling with this infection. ”





GIPHY App Key not set. Please check settings