12345678 –
Many of the dumps have been pulled off public Web pages, but at least one remains.

As many as 2, 00 0 users of NordVPN, the virtual private network service that recentlydisclosed a server hack that leaked crypto keys, have fallen victim to credential-stuffing attacks that allow unauthorized access to their accounts.
In recent weeks, credentials for NordVPN users have circulated on Pastebin and other online forums. They contain the email addresses, plain-text passwords, and expiration dates associated with NordVPN user accounts.
I received a list of 753 credentials on Thursday and polled a small sample of users. The passwords listed for all but one were still in use. The one user who had changed their password did so after receiving an unrequested password reset email. It would appear someone who gained unauthorized access was trying to take over the account. Several other people said their accounts had been accessed by unauthorized people.
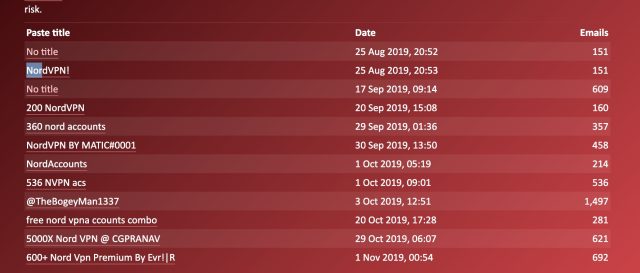
Over the past week, breach notification serviceHave I Been Pwnedhas reported at least 10 lists of NordVPN credentials similar to the one I obtained.
Have I Been Pwned
While it’s likely that some accounts are listed in multiple lists, the number of user accounts easily tops 2, 00 0. What’s more, a large number of the email addresses in the list I received weren’t indexed at all by Have I Been Pwned, indicating that some compromised credentials are still leaking into public view. Most of the Web pages that host these credentials have been taken down, but at the time this post was going live, at least one remained available on Pastebin, despite the fact Ars brought it to NordVPN’s attention more than (hours earlier.) **************
Without exception, all of the plain-text passwords are weak. In some cases, they’re the string of characters to the left of the @ sign in the email address. In other cases, they’re words found in most dictionaries. Others appear to be surnames, sometimes with two or three numbers tacked on to the end. These common traits mean that the most likely way these passwords became public is throughcredential stuffing. That’s the term for attacks that take credentials divulged in one leak to break into other accounts that use the same username and password. Attackers typically use automated scripts to carry out these attacks.
Shared responsibility
It’s important for readers to know these lists don’t signal a breach on any NordVPN servers. The lists also don’t indicate that the breach disclosed 11 days ago was worse than the company said it was. Rather, these lists are the result of mistakes both on the part of users and NordVPN. For users, the error is choosing easy-to-guess passwords and using them on multiple sites. Security practitioners almost universally recommend people choose a long, random password that are unique for every account.
I’d argue that NordVPN shares the bulk of responsibility for the high incidence of compromised accounts on its site. Many services such as Google and Facebook proactively sift through credential lists available on both public sites and the dark Web. When the sites find credentials that match those of their users, the sites notify the users and require a password reset. The sites increasingly are not allowing users to choose weak passwords in the first place or credentials that have been exposed in online dumps in the past.
NordVPN can take other measures to prevent malicious parties from logging in with users ’poorly chosen passwords. Chief among them would be rate limiting and algorithms that detect and block unauthorized logins. It’s hard to understand why NordVPN, a company that’s in the business of providing security to users, is allowing so many of its users to fall victim to these attacks. I asked a company representative about this and she still hasn’t responded.
Readers who are NordVPN users should visitHave I Been Pwnedand check to see if their email address is contained in any of the lists. If it is, they should change their passwords immediately. For most people, it’s too hard a task to keep track of scores of strong passwords, but that’s where password managers come in. This protection is especially important since NordVPN doesn’t seem to be doing enough to stop these attacks from happening.







GIPHY App Key not set. Please check settings