Rising obtains evidence of the “Rattlesnake” hacker group's attack on my country
Date: June 17, 2024
Views:7
Recently, Rising Threat Intelligence Platform conducted an in-depth analysis of the SideWinder organization's attack on the Nepalese government at the end of 2023, and found a large number of source files and malicious programs of phishing websites. It was learned that SideWinder (also known as “Rattlesnake”) organization's phishing attacks on government departments in Asian countries accounted for as much as 40.9%. Among these attacks, Rising found three phishing websites specifically targeting the Chinese government and enterprises. Although the SideWinder organization's attack on my country was not successful, this discovery still revealed that China has become a key target in the organization's attack target list.
Attack groups that aim to steal secrets and engage in espionage
Rising Security experts said that SideWinder, also known as “Rattlesnake”, is a suspected hacker group from India. The group's activities can be traced back to 2012, with targets concentrated in China, Pakistan, Afghanistan and other countries, mainly targeting key areas related to national security and interests such as government, military industry, energy, and scientific research, and will carry out targeted attacks on specific targets to achieve the purpose of information theft and espionage.
Historical attacks
Rising has been tracking the activities of the SideWinder organization for a long time and has captured multiple APT attack incidents since 2019:
In early September 2019, Rising detected two APT attacks against my country. One was disguised as a department of the Ministry of National Defense, sending false invitation letters to military attachés in embassies of various countries in China; the other was sending false security and confidentiality manuals to the overseas representative office of a certain technology company.

In mid-October 2019, Rising captured three attacks against domestic government enterprises. One was to deliver a disguised document of the “Regulations on Civilian Personnel of the People's Liberation Army of China” to a national government department; another was to send a false management document containing malware to a domestic defense research enterprise; and another was to send a false “9th Beijing Xiangshan Forum” agenda to defense and military-related departments.

In late October 2019, Rising captured an attack against the Pakistan Navy. The organization launched a phishing email attack on the target by disguising itself as “a press release on the meeting between the leaders of India and China issued by the Pakistan Navy Public Relations Directorate General.”

In late December 2023, Rising captured an attack against the Nepali government. The organization sent forged “Nepalese Prime Minister Pushpa Kamal Dahal's itinerary information” to Nepali government agencies via email to deceive the trust of relevant personnel.
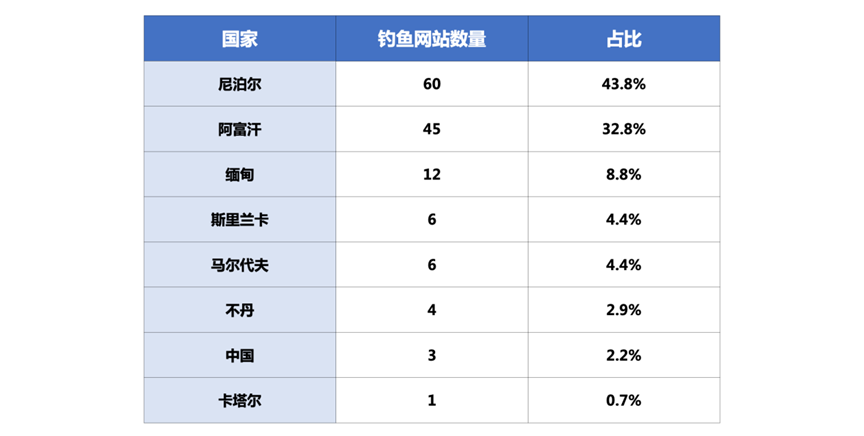
Nepal and Afghanistan were attacked most
After an in-depth analysis of the 2023 attack, the Rising Threat Intelligence Platform obtained the SSH login credentials of one of the servers controlled by the SideWinder organization, and thus discovered not only a large number of source files of phishing websites and some malicious programs, but also some server-side components and data such as files/folders created by the server for each independent victim.
After analyzing the source code of all the phishing websites on the server, Rising learned that the main countries attacked by the SideWinder organization were Asian countries. In the statistics of this server, Nepal and Afghanistan accounted for the highest proportions, 43.8% and 32.8% respectively, and my country accounted for 2.2%.
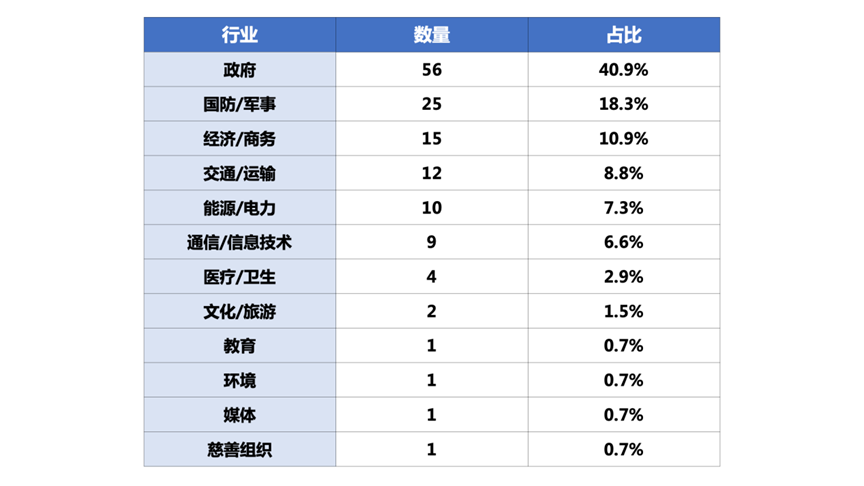
By industry classification, SideWinder's target industries are mainly government and defense/military, accounting for 40.9% and 18.3% respectively.
Rising Security experts analyzed and screened the data of the phishing website and found that the login credentials submitted by Nepal and Afghanistan accounted for the highest proportion on the server, 74.7% and 17.3% respectively. Therefore, it can be seen that there is no record of information submitted by my country on the server.
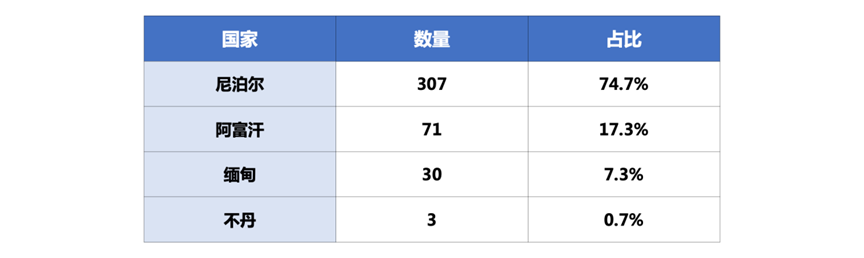
Three phishing websites targeting my country
From the above data, we can see that among the captured servers, there are three phishing websites targeting my country, two of which impersonate my country’s government departments, and one impersonates the management backend login page of a Beijing consulting company.
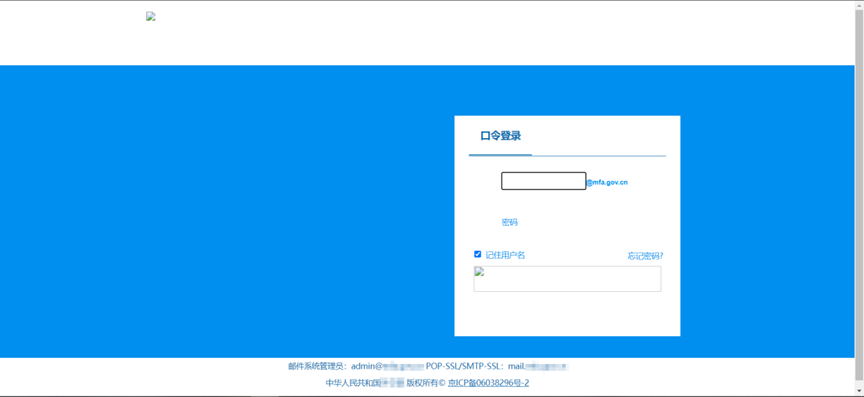
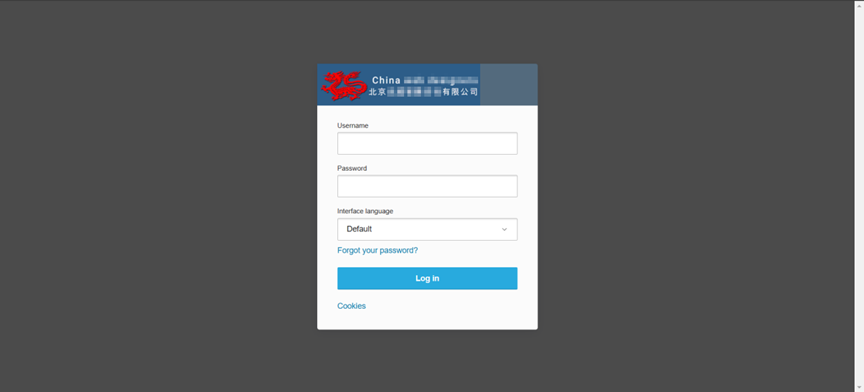
It can be seen that SideWinder's attacks on my country are also mainly concentrated in government departments. Its purpose is to obtain the data and information of government-related personnel, and then steal important confidential data of my country and conduct espionage activities.
The most common attack methods are phishing emails and vulnerabilities
Rising security experts said that SideWinder often uses spear-phishing emails, which use fake government or military-related documents as bait and send them through emails to induce the target to click, thereby activating the remote control backdoor and stealing government or military confidential information. At the same time, the organization also frequently exploits vulnerabilities to attack, such as embedding malicious programs in CVE-2017-11882 or CVE-2017-0199 vulnerabilities, and using these vulnerabilities to execute malicious programs to download and execute remote control programs.
In addition, SideWinder also uses backdoor viruses written in Nim language, which can increase the difficulty of analysis for security personnel, thus reducing the detection rate of security software. In addition, the organization also uses DLL side loading technology, using legitimate system processes to load disguised malicious DLLs to evade defense detection.
How to defend against attacks from this organization?
As SideWinder has posed a serious threat to the network security of the Chinese government and enterprises, Rising recommends that relevant departments and enterprise users take precautions and do the following:
- Improve security awareness: The SideWinder organization mainly uses “watering hole attacks” and “spear phishing attacks” for specific target attacks, both of which belong to the category of phishing. Therefore, sufficient network security awareness and sense of crisis are important. Do not open suspicious files and emails from unknown sources to prevent social engineering and phishing attacks.
- Deploy safe and effective products: SideWinder uses some known “LOLBAS” methods in some attack chains. The core of this method is to make full use of the operating system's own applications to evade detection by traditional security software. In response to this method, most of my country's current security software (anti-virus, EDR) has carried out special targeted processing.
- Timely patch system patches and patches for important software: Since the SideWinder organization is good at exploiting vulnerabilities to attack, governments and enterprises should ensure that all Office software and its components are updated to the latest version to fix known security vulnerabilities.
Source: Rising




GIPHY App Key not set. Please check settings