04/05/2024
summary
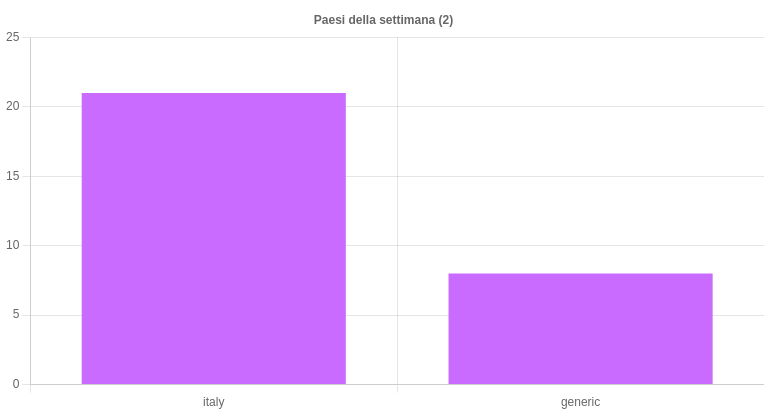
This week, CERT-AGID found and analysed, in the Italian scenario of its reference, a total of 29 campaign malevolentof which 21 with Italian objectives and 8 generic ones which in any case involved Italy, making available to its accredited bodies the relatives 218 Indicators of Compromise (IOC) identified.
Below we report the details of the typologies illustrated in the graphs, resulting from the data extracted from the CERT-AGID platforms and which can be consulted via the Statistics page.
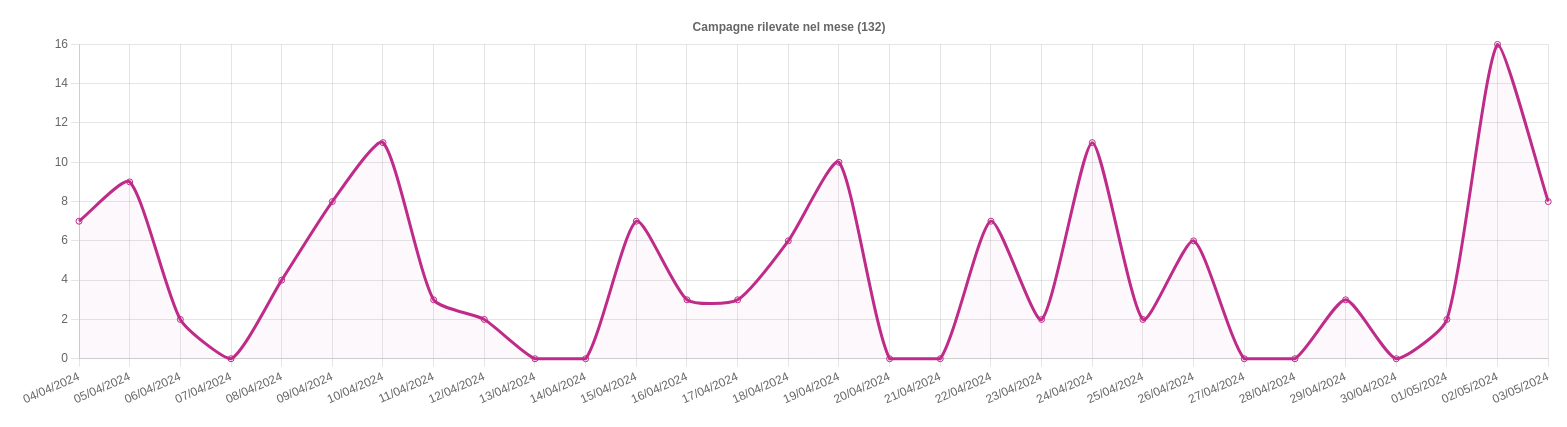
Trend of the month
The most relevant topics of the week
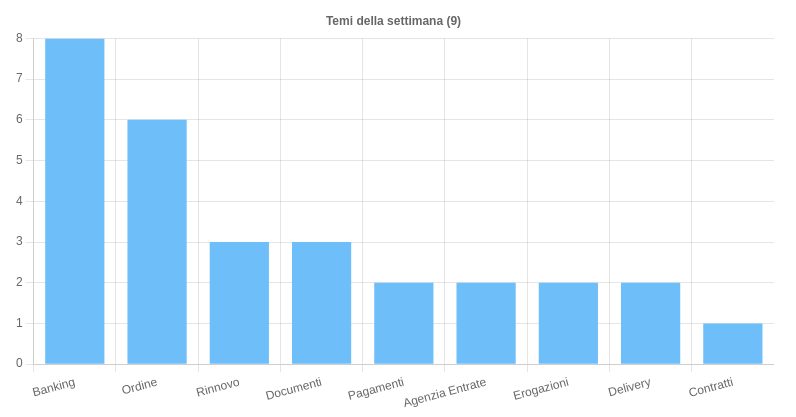
I am 9 the themes used this week to convey malicious campaigns on Italian territory. In particular it is noted:
- Banking – Recurring theme in phishing and smishing campaigns aimed mainly at customers of Italian banking institutions and to spread malware Angry with the aim of compromising devices Android of Italian users.
- Order – Topic exploited for malware campaigns AgentTesla, Formbook e ZgRat.
- Renewal – Theme used for phishing campaigns aimed at customers Aruba.
The rest of the themes were exploited to convey malware and phishing campaigns of various types.
Events of particular interest:
- Spread of Keylogger malware via fake Revenue Agency – PuntoFisco page
- Italian Remcos campaign via Guloader
- INPS smishing campaigns aimed at stealing identity documents
- Lockbit ransomware campaign detected again
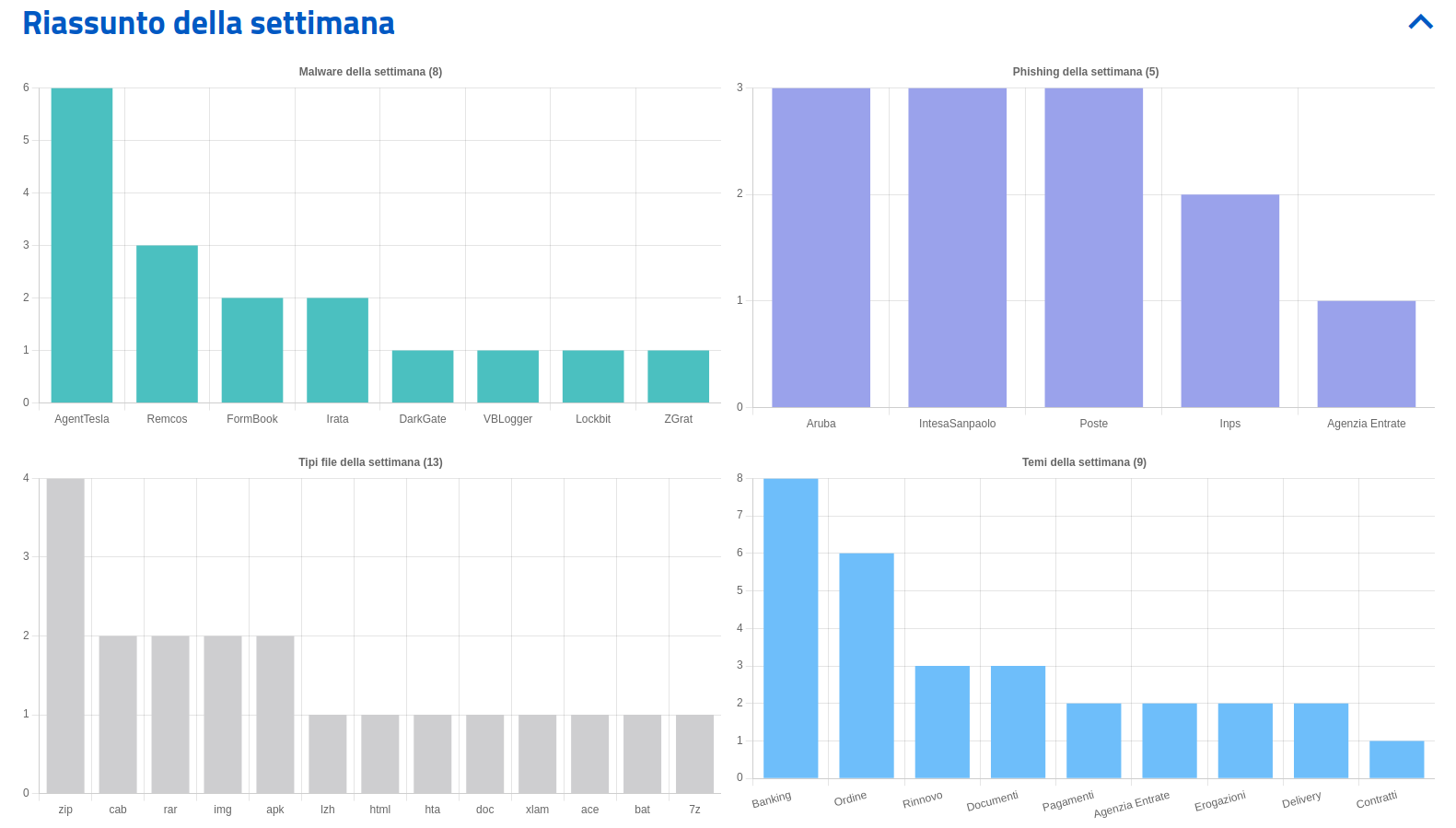
Malware of the week
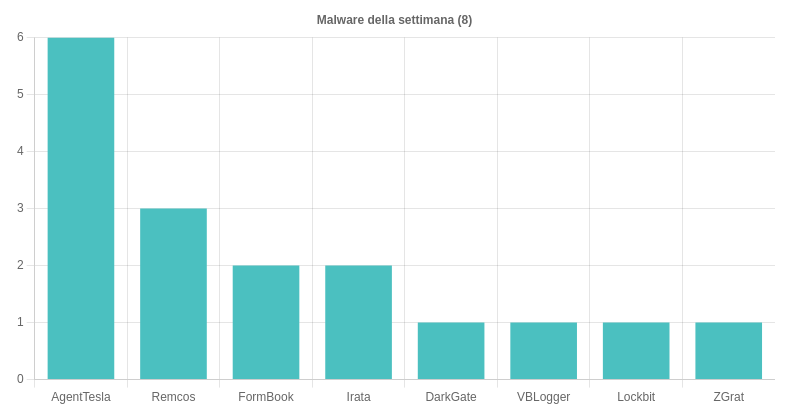
They have been observed in the Italian scenario 8 malware families. Specifically, of particular importance this week, we find the following campaigns:
- AgentTesla – Six campaigns identified, four of which are Italian and two generic, themed “Order”, “Contracts” e “Delivery“, sent via email with RAR, CAB, IMG, RAR and ACE attachments.
- RemcosRAT – Three campaigns were detected, two Italian and one generic, themed “Payments“ e “Documents“, spread via emails with ZIP, 7Z and CAB attachments. One of the Italian countryside uses Guloader and uses the Leonardo company logos.
- Formbook – Observed two generic themed campaigns “Order“ e “Delivery“, spread in Italy via emails with LZH and ZIP attachments containing DOC that exploit the old Equation Editor vulnerability.
- Angry – Two Italian themed campaigns opposedBanking” conveyed via SMS with a link to the download of a malicious APK.
- DarkGate – A generic themed campaign detectedDocuments” conveyed via email HTML attachments from which an HTA script is downloaded.
- VBLogger – Italian themed campaign “Internal Revenue Service” aimed at compromising systems with a keylogger written in VB6. Details and IoCs are available in a specific press release.
- LockBit – Another themed campaign identifiedDocuments” aimed at conveying the ransomware via email with ZIP attachments an SCR executable such as observed last week.
- ZGrat – A themed campaign detectedOrder”, spread through emails with XLAM attachments.
Phishing of the week
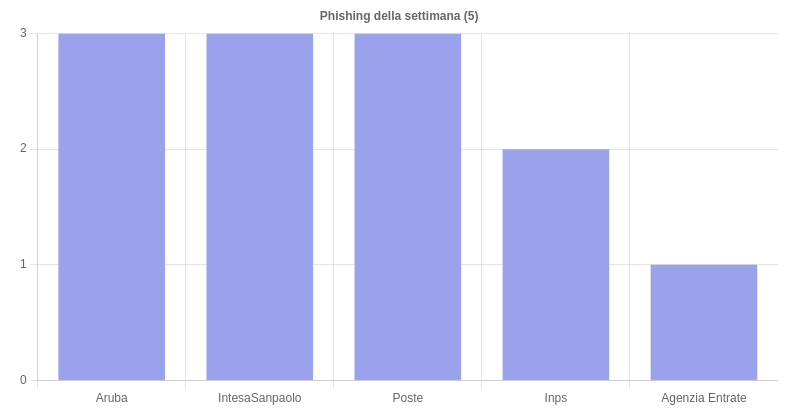
I am 5 the brands of the week involved in phishing and smishing campaigns. Of particular interest this week: a phishing campaign Revenue Agency (Tax Point) and smishing campaigns INPS.
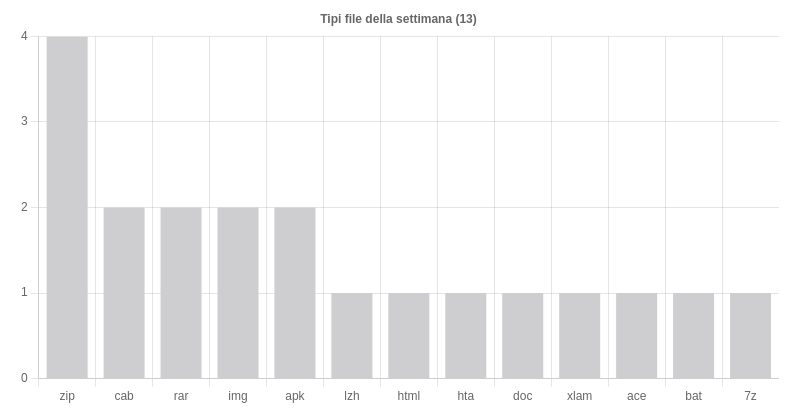
File formats mainly used to deliver malware
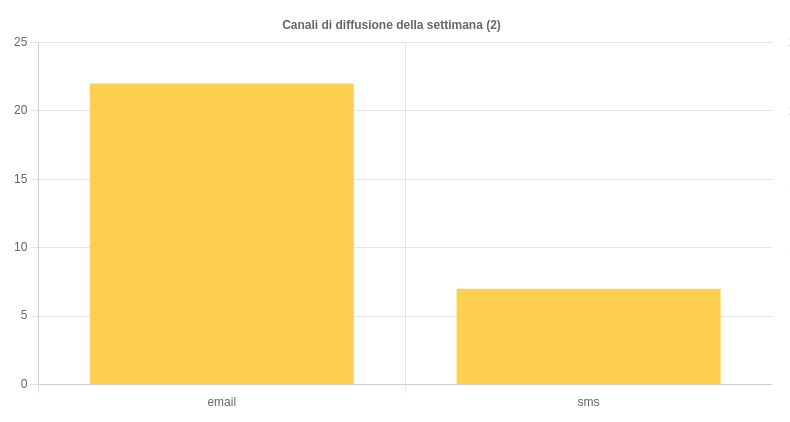
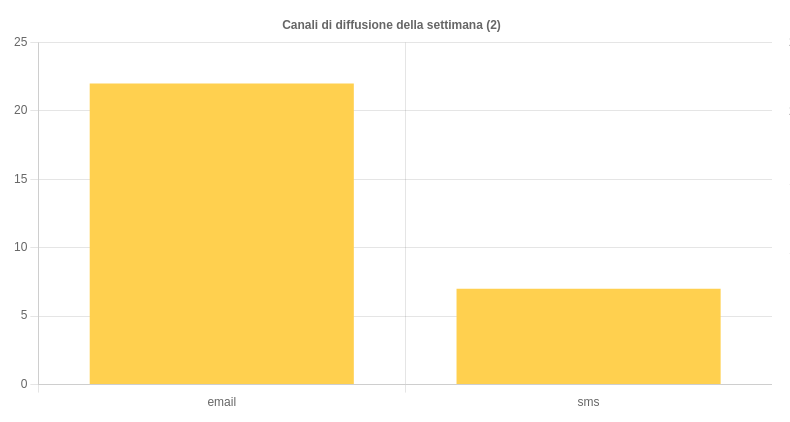
Distribution channels
Targeted and generic campaigns




GIPHY App Key not set. Please check settings