
This year's Red Sea region has been plagued by constant disputes, which not only seriously disrupted normal maritime transportation, but also posed a threat to optical cables buried deep under the sea.
As the Red Sea crisis continues, as of early March, four Asia-Europe communication optical cables passing through the Red Sea seabed – Asia-Africa-Europe No. 1, East-South Africa submarine communication optical cable, Europe-India Channel and TGN connecting India-Saudi Arabia-France have all been damaged. The damage directly affects 25% of the data traffic between Asia and Europe.
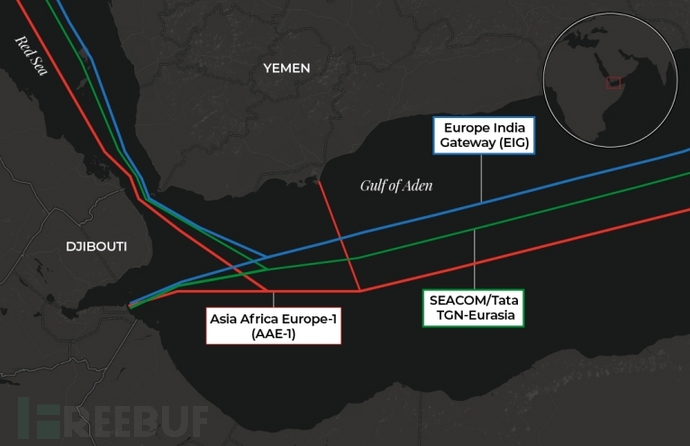 Affected Red Sea submarine cables
Affected Red Sea submarine cables
It can be seen that the Red Sea plays a very important role in intercontinental and even global network communications. Experts in related fields said that the Red Sea is “one of the three most important cable intersections” in the world. An estimated 17% of global internet traffic travels through underwater fiber optic cables in the Red Sea.
Who sabotaged such an important submarine optical cable? The Western media almost insisted that the Houthi armed forces, which have frequently caused troubles in the Red Sea region, were responsible. However, the other side firmly denied this accusation and claimed that the perpetrators were troops from the United States, Britain and other countries stationed in the area. So far, it has not been determined exactly what caused the damage to these four optical cables.
John Gower, a former submarine commander of the British Royal Navy, pointed out in an interview with the British media that to launch an attack on cables laid hundreds of meters underwater requires the use of submarines, and the Houthi armed forces do not have submarines; Head of Marketing Department of Seacom Claudia Ferro believes that the culprit causing damage to the cable may be the anchor of a merchant ship passing through the Red Sea. The exact situation can only be confirmed after maintenance personnel arrive at the scene.
This is another high-profile and confusing incident of submarine infrastructure damage since the Nord Stream natural gas pipeline explosion in 2022. Compared with regional infrastructure such as natural gas pipelines, submarine optical cables have their own cyberspace attributes and have a wider impact. Once an accident occurs, it will often affect the whole body.
Fragile submarine cables
Today's social activities have become increasingly deeply integrated with cyberspace. As of the end of 2021, the total length of 440 submarine optical cables in use around the world exceeds 1.3 million kilometers, carrying 99% of the world's international information and communication interactions. Although satellites can reach areas without optical fiber connections, their bandwidth provision capabilities are significantly insufficient compared to submarine optical cables. Although terrestrial optical cables have the advantage of lower construction and maintenance costs, they are mostly limited to communication scenarios between neighboring countries. It can be seen that submarine optical cables not only provide communication services necessary for the operation of international society, but their influence has penetrated into all aspects of national security on a global scale.
The security value of submarine optical cables
Under the trend of economic globalization, submarine optical cables are an important link to ensure the normal operation of economic and financial activities and large-scale Internet platform services. Once the submarine cable fails, global real-time financial transaction activities will inevitably be affected, and Internet platform services will also be interrupted. Downtime.
With big data and enterprises migrating to the cloud, large amounts of data are distributed and stored across national and regional boundaries. For global network security, submarine optical cables serve as the physical infrastructure of cyberspace, and their reliability also directly determines the network security. The ground floor security of the space. If the submarine optical cable system is damaged or interfered with, network access services in relevant areas will be severely affected, and it will also have secondary effects in other important areas involving national interests.
 Undersea optical cable being laid
Undersea optical cable being laid
In addition, modern military organizations rely extensively on submarine fiber optic cable systems for their operations. Since the network is not only an important enhancer of modern military combat capabilities, but also constitutes a key component of modern military power, with the development of advanced command and control and reconnaissance intelligence systems, the demand for network bandwidth is also increasing. , the submarine optical fiber system has the characteristics of small network delay, large capacity and low cost, and will play an important role in providing indispensable support and guarantee. Therefore, the security protection of submarine optical cable systems will become an essential consideration in future military action plans.
Security risks faced by submarine optical cables
Due to the large geographical span and the specific environment of the deep seabed, the security risks faced by submarine optical cables have their own particularities and are deeply affected by the environment. In terms of natural damage, the bites of large fish and seismic activities will cause varying degrees of damage to submarine optical cables. For example, the strong earthquake that occurred in Taiwan, China, in 2006 caused damage and interruption to many international submarine optical cables; the “3·11” earthquake that Japan suffered in 2011 also caused some Asian users to lose almost all Internet services.
In addition to natural disasters, damage from human factors is still the main factor causing damage to submarine optical cables, which is divided into unintentional or intentional damage. Common unintentional damage mainly comes from ship equipment such as fishing nets and drag anchors. According to statistics, more than 200 optical cable damage accidents occur around the world every year, and about 60% of them are the result of ship operation errors.
 Submarine optical cables located in shallow sea areas
Submarine optical cables located in shallow sea areas
Man-made vandalism is mostly caused by local militants and pirates for economic purposes or political revenge. In 2007, the Asia-American Gateway (AAG) optical cable connecting China, Southeast Asia and the United States was stolen and cut by Vietnamese fishing boats for the sole purpose of obtaining the limited metal materials contained in the optical cable; in 2008 January In August, two submarine optical cables near Alexandria, Egypt, were cut off by unidentified persons at multiple locations, resulting in almost complete disruption of Internet services in large areas of Europe, the Middle East, North Africa and India. Once such sabotage activities are successfully implemented, it will be difficult for communication network operation and maintenance organizations to quickly restore communication capabilities by re-planning paths.
As network communication service infrastructure, submarine optical cables cannot escape cyberattacks from hackers and espionage activities by some national intelligence agencies. For example, the inherent vulnerability threats of optical cables. Since the core functions of optical fiber network management systems are monitoring, control and data collection, and a large number of general operating systems such as Windows and applications based on WEB technology are used, network attackers are fully capable of taking advantage of their inherent vulnerabilities to carry out attacks. , thereby affecting the normal operation of the optical cable system.
It is precisely because of the data transmission characteristics of optical cables that intelligence agencies in some countries also regard optical cables as treasures and monitor them. For example, in 2013, the Washington Post published a confidential NSA slide provided by Snowden, which revealed another program called “Upstream” in addition to the “Prism” program, exposing the U.S. The National Security Agency began its large-scale undersea optical cable eavesdropping activities in the 1970s. It leveraged its advantages in data transmission infrastructure and collaborated with allies such as the United Kingdom to conduct data eavesdropping on at least 200 optical cable systems around the world. Although such monitoring activities did not damage the physical structure and normal functions of the submarine optical cable system, they seriously weakened the reliability of cyberspace communication infrastructure and protocols, making the global information security situation face more severe challenges.
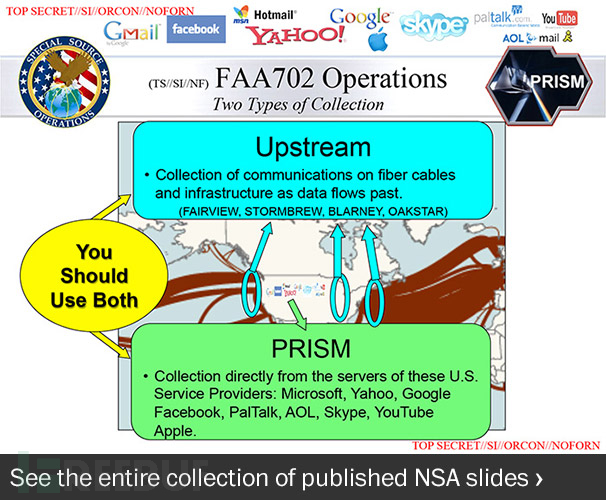 Exposed slides reveal U.S. “upstream” surveillance program targeting global submarine optical cables
Exposed slides reveal U.S. “upstream” surveillance program targeting global submarine optical cables
Network infrastructure security challenges
Just a few days before the interruption of the Red Sea submarine optical cable, the European Union issued the “White Paper on European Digital Critical Infrastructure Needs”, which mentioned the need to build a secure and resilient digital infrastructure, including strengthening the security and resilience of submarine optical cable infrastructure. . Undoubtedly, the interruption of submarine optical cables in the Red Sea highlights the urgency of safe construction of these infrastructures.
In addition to submarine optical cables, any network-related infrastructure is vulnerable to damage caused by accidents, self-vulnerabilities or malicious damage. Especially as more and more services move to the cloud, the security of infrastructure becomes a key factor for various network services to function properly. The most important guarantee for operation, but the facts are often not what people want.
The Internet giant that failed
Last year alone, many domestic Internet giants experienced multiple service outages of varying degrees. In the early morning of March 29, 2023, Tencent WeChat and QQ services crashed. Many functions including WeChat voice conversations, Moments, WeChat payment, as well as QQ file transfer, QQ space and QQ mailbox were unavailable. Related content topics quickly Rushed to the top of Weibo’s trending searches. Afterwards, it was found that the accident was caused by a failure of the cooling system in Guangzhou Telecom's computer room. Tencent believed that the accident exposed the hidden dangers of imperfect disaster recovery design and emergency plans, and that the relevant business departments did not have adequate risk prevention awareness, and designated it as a Category 1 company. Accident, many people were punished.
On November 12, 2023, the Alibaba Cloud service owned by Alibaba suffered a large-scale failure. Many Alibaba products such as Taobao, Xianyu, DingTalk, and Alibaba Cloud Disk were inaccessible or had service abnormalities. Related topics were all hotly searched, and it was embarrassing. It is said that Alibaba is “organizing a group to compete in the rankings”. Not only that, the failure also affected many Alibaba overseas service networks and technology platforms provided by Alibaba Cloud. Such a large-scale failure is very rare in the history of Alibaba. According to Alibaba officials, the failure was related to an underlying service component.

Alibaba Cloud's large-scale service failure affects products and scope
In addition to domestic giants, well-known foreign companies involved in Internet services, including Amazon, Google, Apple, etc., have also experienced varying degrees of service outages recently. On March 11, 2023, Apple's iTunes store, AppStore application store and multiple Internet online services suffered a global large-scale outage. The outage lasted for 11 hours and directly caused Apple's stock price to fall by 1.82%, the highest level in more than a month. the lowest point.
Faced with a large number of hardware devices and complex software applications, network infrastructure must not only resist external intrusions, but also be alert to internal disasters. Once a security incident occurs, the intricate internal correlation attributes often shorten the repair time. The costs are difficult to estimate, and these are the crux of current network infrastructure security.
Strengthen network resilience to protect network infrastructure
As mentioned in the previous “White Paper on Digital Critical Infrastructure Requirements in Europe” – to build a secure and resilient digital infrastructure, although the term “Cyber Resilience” is no longer the latest cyber security buzzword, it is very important to the basics. In terms of facility protection, security flexibility still has a lot of room for development.
According to U.S. Presidential Policy Directive 21 (PPD-21), Security and Resiliency of Critical Infrastructure, issued in 2013, resilience includes “the ability to withstand and recover from intentional attacks, accidents, or naturally occurring threats or events.” , which includes three major security elements: physical space, cyberspace, and personnel. Whether it is submarine optical cables or the equipment rooms of large Internet companies, although the specific surrounding environments are very different, they may be threatened by these three elements at all times.
Resilience, the core of cyber resilience, requires focusing on the primary mission or core functions of the infrastructure and recognizing environmental changes that may affect its core functions.
Due to the complexity of these infrastructures, it is difficult to increase the security level of all systems, components and parties involved to a high level. Therefore, cybersecurity experts suggest that attention should be focused on core functions, and various environmental changes that may affect its core functions should be carefully examined, including external and internal environments, system environments, stakeholder environments, and data flow paths, etc., and focused analysis The ways, conditions, pathways and potential harm levels of security incidents on core functions. Through the strategy of sticking to the bottom line and preventing risks, establish and improve the defense system of critical information infrastructure, strengthen the system's ability to withstand and resist attacks, and enhance the system's recovery and reconstruction capabilities to improve system flexibility and security.
postscript
As today's international geopolitics remains complex and regional conflicts occur from time to time, the scale and frequency of cyber attacks are almost only increasing. Countries may use cyber attacks to conduct espionage, destroy opponents' infrastructure, or carry out cyber operations. War, if things go on like this, any natural or unnatural, intentional or unintentional damage to network infrastructure may be subject to intense scrutiny by all parties, and may even be politicized or attacked.
As a result, some countries may introduce more stringent cybersecurity regulations and supervisory measures to strengthen the control and monitoring of network infrastructure, which may affect transnational network service providers and data flows. This will also cause international network security cooperation to be hindered. In particular, long-span network infrastructure such as submarine optical cables may not be properly maintained. Even when problems arise, all parties will blame each other and blame each other, and refer to incidents or conflicts. Expand itself.
Network infrastructure connects not only thousands of ordinary users, but also an important guarantee for the normal operation of many enterprise organizations and the orderly security of national cyberspace. Its inherent connection and data circulation attributes also emphasize the need for cooperation and shared responsibility for security. , rather than confrontation and separatism. Mutual assistance and win-win cooperation are the sustainable development paths for long-term protection of network infrastructure and continuous improvement of security defense levels.
References:
https://www.secrss.com/articles/444
https://www.secrss.com/articles/48174





GIPHY App Key not set. Please check settings