
Introduction: TP-Link Archer AX21 (AX1800) router users are advised to follow the vendor's firmware upgrade instructions for security updates.
At least six different botnet malware have been found to be exploiting TP-Link Archer AX21 (AX1800) routers affected by last year's command injection security issue. The flaw, tracked as CVE-2023-1389, is a high-severity unauthenticated command injection issue in the Locale API accessible through the TP-Link Archer AX21 web management interface.
Researchers discovered the issue in January 2023 and reported it to the vendor through the Zero-Day Initiative (ZDI). TP-Link addressed the issue in March 2023 by releasing a firmware security update, and proof-of-concept exploit code emerged shortly after the security advisory was made public.
Cybersecurity teams subsequently issued warnings about multiple botnets, including three Mirai variants (1, 2, 3) and a botnet called “Condi” that targets unpatched devices.
This week, Fortinet issued another warning, saying it was observing a surge in malicious activity exploiting the vulnerability, noting that it originated from six botnet operations.
Telemetry data from Fortinet shows that starting in March 2024, daily infection attempts utilizing CVE-2023-1389 typically exceeded 40,000 and could reach as high as 50,000.
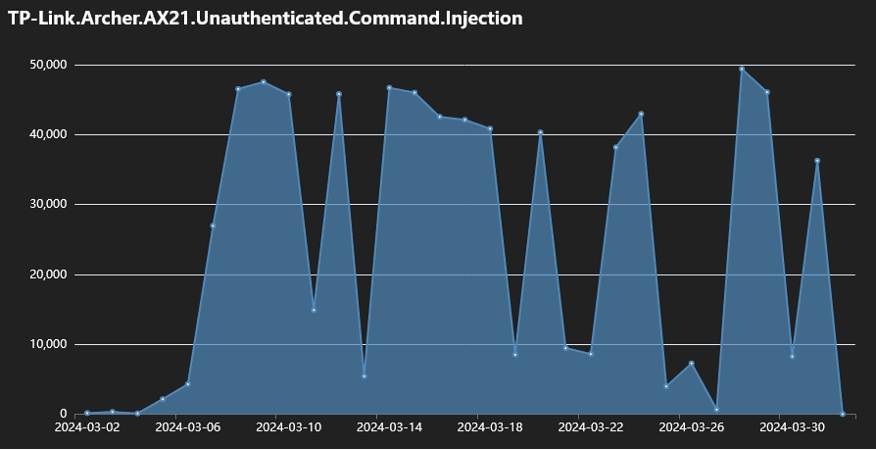
Activity diagram regarding CVE-2023-1389
Multiple attacks targeting this vulnerability focused on botnets such as Moobot, Miori, Golang-based proxy AGoent, and Gafgyt variants. Each botnet utilizes different methods and scripts to exploit vulnerabilities, establish control over infected devices, and command them to engage in malicious activities such as distributed denial-of-service (DDoS) attacks.
They are going: Download and execute a script that fetches and runs an ELF file from a remote server, then wipes the file to hide traces.
Gafgyt variants: Specializes in DDoS attacks by downloading scripts to execute Linux binaries and maintain persistent connections to C&C servers.
Will arrive: Known for launching DDoS attacks, it obtains and executes scripts to download ELF files, execute them according to the schema, and then delete traces.
Miori: Utilizes HTTP and TFTP to download ELF files, execute them, and perform brute force attacks using hardcoded credentials.
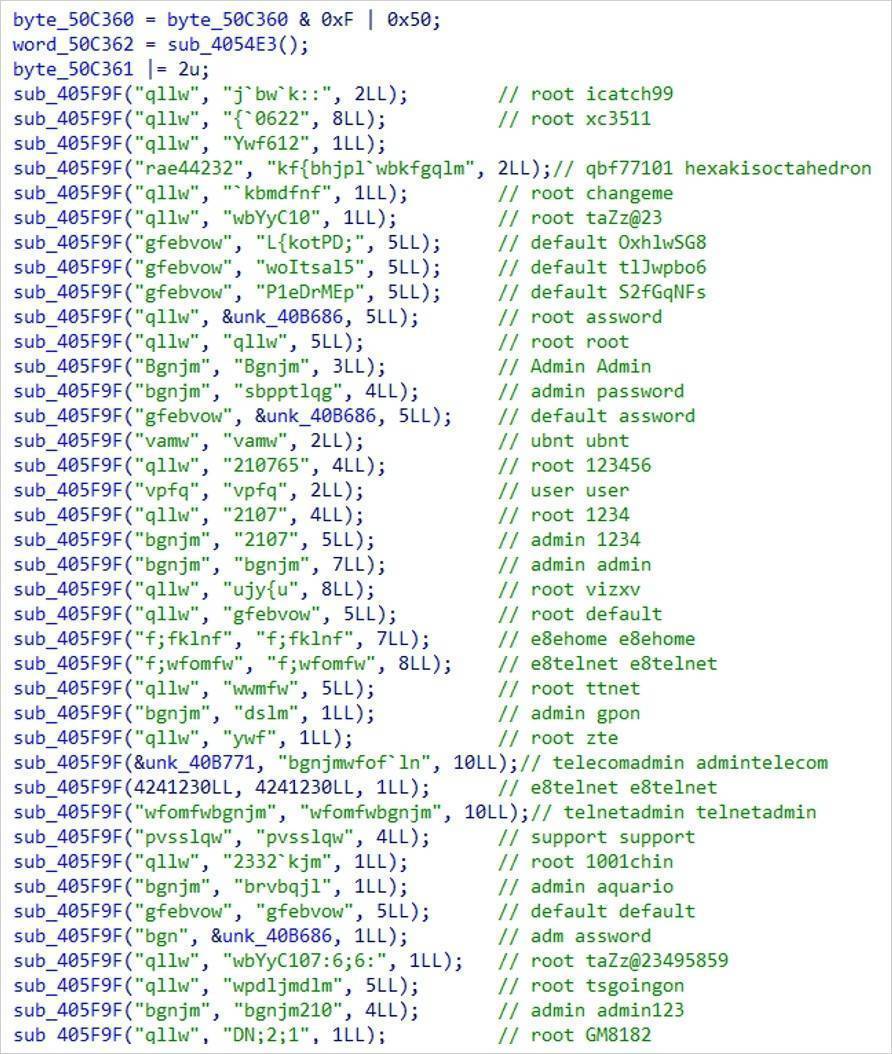
List of credentials used by Miori to brute force accounts
Mirai variants: Downloads a script that then fetches ELF files compressed using UPX, monitors and kills packet analysis tools to avoid detection.
Condi: Uses downloader scripts to increase infection rates, prevent device reboots for persistence, and scan and kill specific processes to avoid detection.
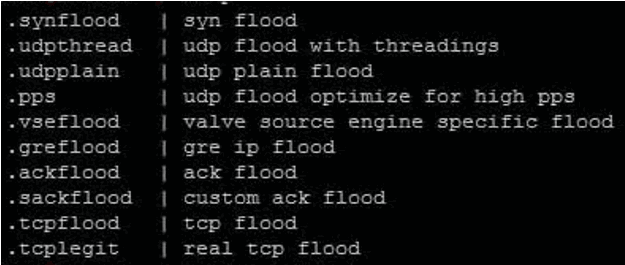 Condi DDoS attack mode
Condi DDoS attack mode
Fortinet said that despite security updates released by the vendor last year, a large number of users continue to use outdated firmware. TP-Link Archer AX21 (AX1800) router users are advised to follow the vendor's firmware upgrade instructions for secure updates and to change the default administrator password to a longer one and disable network access to the admin panel when not needed.
Article translated from: https://www.bleepingcomputer.com/news/security/multiple-botnets-exploiting-one-year-old-tp-link-flaw-to-hack-routers/ If reprinted, please indicate the original address


Thank you for your support, I will continue to work hard!
OpenWeChatScan and click on the upper right corner to share.
You may be interested
-

Multiple botnets exploit year-old TP-Link vulnerability to conduct router attacks
-

Hackers exploit Windows SmartScreen vulnerability to deliver DarkGate malware
-

More than 12 million authentication secrets and keys leaked on GitHub
-

ConnectWise urges ScreenConnect administrators to patch critical RCE vulnerabilities
-

More than 28,500 Exchange servers vulnerable to vulnerability
-

Malware on the rise using PikaBot: How businesses can protect against it












GIPHY App Key not set. Please check settings