
Introduction: Bangbang Security released the “2024 Q1 Mobile Application Security Risk Report”.
On March 22, China Internet Network Information Center (CNNIC) releasedThe 53rd “Statistical Report on China's Internet Development Status”.The report shows that as of December 2023, the number of Internet users in my country will reach1.092 billionof which the number of mobile Internet users reaches10.91100 millionaccounting for as much as99.9%。
Communication, consumption, shopping, travel, entertainment… APP has achieved full coverage of life scenes, and mobile Internet applications based on mobile smart devices such as mobile phones have become an indispensable key element in daily life. At the same time, malware is becoming increasingly rampant, and risk issues such as illegal collection of personal information and malicious misuse of data are emerging one after another, posing a serious threat to the data and property security of individuals and enterprises.

Recently, Bangbang Security released“2024 Q1 Mobile Application Security Risk Report”,Based on the mobile application security situation monitored and analyzed by Bangbang Security Mobile Application Supervision Platform in Q1 2024, we will continue to analyze the development of domestic mobile application attack technology and security trends for everyone.providing assistance and guidance for mobile application security construction.
1 Overview of mobile applications nationwide
Data from the Bangbang Security Mobile Application Supervision Platform’s real-time monitoring of 1,000+ active application markets at home and abroad show that among the applications released from January 1, 2024 to March 31, 2024, the total number of Android applications attributed to the country is 179386 modelsinvolving the total number of developers 54180 homes。
Judging from the area where APP is distributed,Beijing ranks first in the number of APPs, accounting for approximately 21.42% of the total APPs in the country., the second and third ranked regions are Guangdong Province and Shanghai City respectively, with the corresponding number of APPs being 34,349 and 17,140. The specific distribution is shown in Figure 1.
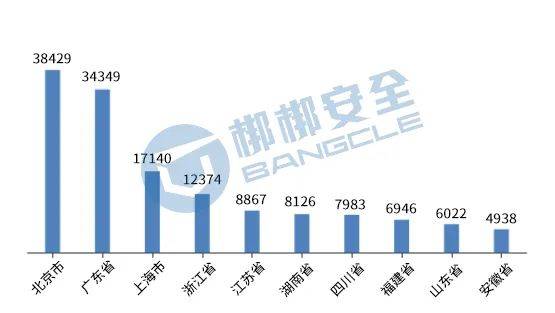
Figure 1 Top 10 national APP regional distribution map
Judging from the functions and types of uses of the APP,Utility tools The number of APPs ranks first, accounting for 17.75% of the total APPs in the country;Education and learning APP ranks second, accounting for 12.17% of the total number of APPs in the country;other APP ranks third, accounting for 9.39% of the country’s total APPs. The proportion of each type of APP is shown in Figure 2.
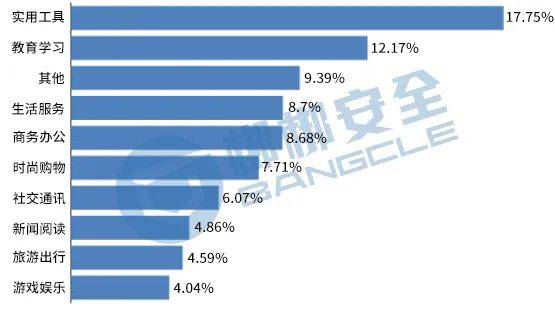
Figure 2 National APP type distribution TOP10
2 Overview of national mobile application security analysis
The Bangbang Security Mobile Application Supervision Platform conducts random inspections of Android applications across the country by calling different types of automated detection engines. Risk applications arePiracy (counterfeiting), overseas data transmission, high-risk vulnerabilities, personal privacy violationsComprehensive statistics from the 4 dimensions, and the number of risk applications are shown in Figure 3.
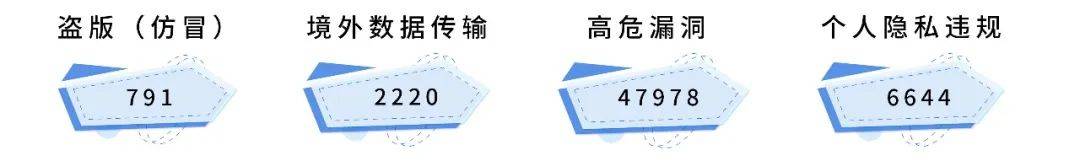
Figure 3 Comprehensive statistics of four dimensions of risk application
01 Vulnerability risk analysis
We randomly selected 76,551 Android APPs across the country for vulnerability testing and found that 61,291 APPs were vulnerable to vulnerabilities.That is, 80.89% of APPs have medium to high risk of vulnerabilities.. Among the 61,921 vulnerable apps, 77.48% were apps with high-risk level vulnerabilities, and 97.61% were medium-risk apps (the same app may have multiple levels of vulnerabilities).
Statistics on different types of vulnerabilities show that most security vulnerabilities can be solved through application hardening solutions.The top three types of application vulnerabilities are: JAVA code decompilation risk, HTTPS unverified host name vulnerability and dynamic registration Receiver risk。
From the perspective of APP type,other APP has the highest vulnerability risk, accounting for 20.01% of the total number of vulnerable APPs; followed byUtility tools APP, accounting for 15.52%;Education and learning APP ranks third, accounting for 9.88%. The top 10 types of vulnerabilities are shown in Figure 4.
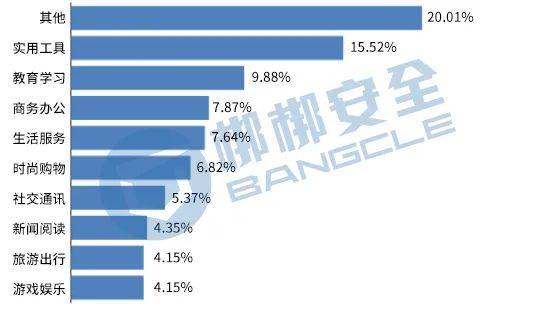
Figure 4 Top 10 APP types with vulnerabilities
02 Piracy (counterfeiting) risk analysis
Pirated APPs refer to APPs that use illegal means to add malicious code to the original APP without the consent or authorization of the copyright owner, and then publish it again, causing user information to be leaked, mobile phones to be infected with viruses, or other security hazards. 791 Android APPs across the country were randomly selected for piracy (counterfeiting) engine analysis, and 791 pirated (counterfeiting) APPs were detected, among which,Practical tools, life services, and news reading apps are the hardest hit areas for copycat apps.the proportion of each type is shown in Figure 5.
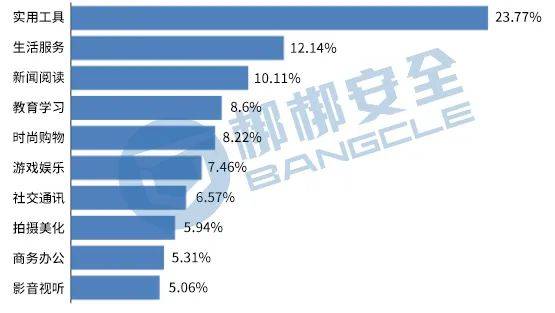
Figure 5 Top 10 pirated (counterfeit) APP types
03 Overseas transmission data analysis
On March 22, 2024, the Office of the Central Cybersecurity and Information Technology Commission officially released“Regulations on Promoting and Regulating Cross-Border Data Flows”released at the same time“Guidelines for the Declaration of Data Transfer Security Assessment (Second Edition)” and “Guidelines for the Registration of Standard Contracts for the Transfer of Personal Information (Second Edition)”To guide enterprises to implement their compliance obligations for data export, it fully embodies my country's regulatory thinking of safeguarding national security by strengthening cross-border supervision of data.
10,621 Android APPs were randomly selected from the country's Android APPs for overseas data transmission engine analysis, and it was found that 2,220 of them were transmitting data to overseas IPs. From the statistical data, the largest number were sent to Australia, accounting for the highest proportion.70.36% ; followed by those sent to the United States, accounting for25% the ranking of the proportion of data transferred to overseas countries is shown in Figure 6.Whether it is data outflow for the mobile application's own program code or overseas data outflow for third-party SDKs, it is recommended that regulatory authorities strengthen the supervision of data outbound behavior.。

Figure 6 Top 10 data transmission rates to overseas countries
From the perspective of APP type,other APPs most frequently transmit data to overseas IP addresses, accounting for 25.54% of the total number of APPs transferring overseas; followed byUtility tools APP, accounting for 15. 72%;Games and entertainment APP accounts for 7.93% of the total number of overseas data transmission APPs, ranking third. The proportion of each type is shown in Figure 7.
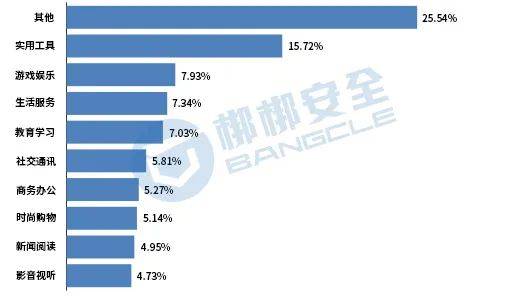
Figure 7 Top 10 rankings of various types of overseas data transmission APPs
04 Analysis of personal privacy violations
As a mobile application that can work properly only when connected to the Internet, it is normal to collect network permissions, system permissions and WiFi permissions, butWhether mobile applications should collect “dangerous permissions” such as user text messages, phone calls, and locations needs to be analyzed based on the legitimate business needs of the application itself. .Based on the national “Information Security Technology Personal Information Security Specifications”, “Methods for Identification of Illegal Collection and Use of Personal Information by APPs”, “Regulations on the Scope of Necessary Personal Information for Common Types of Mobile Internet Applications” and other relevant requirements, 10,621 Android APPs were randomly selected from across the country. Compliance engine analysis detects62.56% of APPs involve privacy violations, such as illegal collection of personal information, APPs forcing, frequent, and excessive requests for permissions, APPs frequently self-starting and associated startups, etc.. The proportion of each violation type is shown in Figure 8.
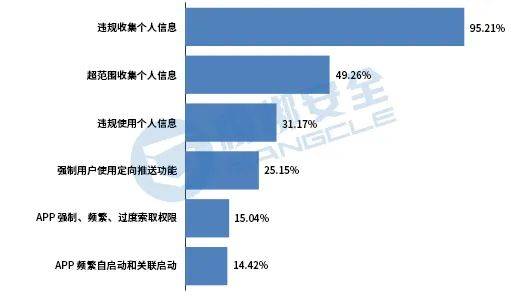
Figure 8 Proportion of types of personal privacy violations
From the perspective of APP type,other APPs have the largest number of personal privacy violations, accounting for 22.4% of the total detections, of which more than 50% of other types of APPs involve frequent permission applications;Utility tools Privacy violations in APP accounted for 14.89% of the total number of detections, ranking second;Education and learning Privacy violations in APP accounted for 9.3% of the total number of detections, ranking third. Figure 9 shows the proportion of various types of apps involving personal privacy violations.
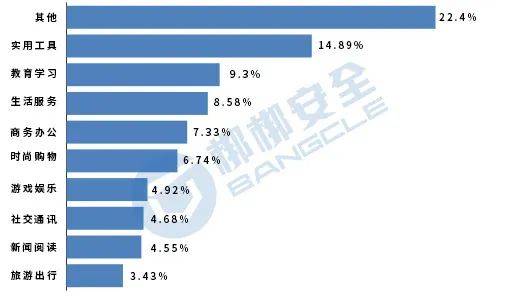
Figure 9 Top 10 APP types that violate personal privacy
05 Third-party SDK risk analysis
Third-party SDK is a toolkit developed by third-party service companies such as advertising platforms, data providers, social networks, and map service providers. APP developers and operators generally consider the development cost and operating efficiency during the APP development and design process. Use third-party software development kits (SDKs) to simplify the development process. 71,165 Android APPs across the country were randomly selected for third-party SDK engine analysis, and it was detected that 95.88% of the applications had built-in third-party SDKs.If an SDK has security vulnerabilities, applications containing the SDK may be vulnerable to attacks。
From the perspective of APP type,other APP has the largest number of built-in third-party SDKs, accounting for 19.56%; followed byUtility tools APP, accounting for 15.63%;Education and learning APP ranks third, accounting for 10.62%. The proportion of various types of third-party SDK applications is shown in Figure 10.
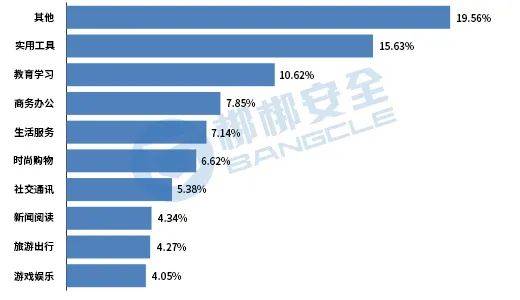
Figure 10 Top 10 third-party SDK applications by type
06 Analysis of current situation of application reinforcement
As mobile APPs penetrate into all aspects of people's lives, the black and gray industry has also grown. If the application is not protected, it is tantamount to “running naked”. Security reinforcement of the APP can effectively prevent it from being reversely analyzed, decompiled, and reused. Packaging, malicious tampering, etc.Randomly selected 119,057 Android APPs across the country for hardening engine testing, and found that hardened apps accounted for only 35.44% of the total number of apps.。
From the perspective of application type,Financial management APP has the highest reinforcement rate, accounting for 69.93% of the total financial management APPs; followed byParty and government agencies APP, accounting for 69.53% of the total APP for party and government agencies; the third place is photography and beautification APP, accounting for 69.53% of the total APP for party and government agencies.Photography and beautification 48.02% of the total APP. The top 10 application types with a proportion of hardened APPs are shown in Figure 11.
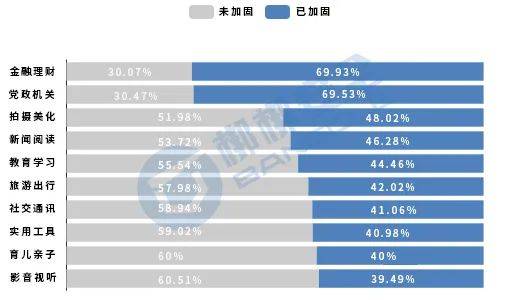
Figure 11 Ranking of top 10 reinforced APP types
Under the general trend of innovative development of information technology applications, Bangbang Security has always been customer-centric, with continuous R&D investment and product innovation, to establish a comprehensive mobile application security and IoT security protection ecosystem from both the technology and service levels.Established an APP full life cycle security solution including application design and development, application testing, application release, and application operation and maintenance.forming full-stack product and service capabilities from protection, reinforcement, detection to supervision, evaluation, and response, in-depth management of application chaos such as APPs, mini programs, and quick applications, and has become a trustworthy partner for manufacturers in various industries.
In the digital age, mobile Internet continues to penetrate, promoting digitalization and informatization to penetrate into all aspects of social life development. The business importance and security requirements of mobile channels are getting higher and higher. At a time when the number of mobile applications and business richness are growing explosively, Bangbang Security has the corporate mission of “protecting your software” and is committed to the contention of a hundred schools of thought in application technology and the flourishing of application experiences, so that Internet users can have a better, safer and more secure life. Compliant digital intelligence life.
If reprinted, please indicate the original address.


Thank you for your support, I will continue to work hard!
OpenWeChatScan and click on the upper right corner to share.
You may be interested
-

Prescribe a “digital prescription” for the APP! Bangbang Security releases “2024 Q1 Mobile Application Security Risk Report”
-

Assembly order! The 2024 Data Security Competition is officially launched (scan the QR code in the article to register)
-

Check Point revolutionizes email security again: Patented unified management helps increase efficiency and productivity
-

Interpretation of Tianrongxin’s annual report: products, operations, innovation, the foundation of development under long-termism
-

Tianrongxin Li Xueying was elected as the deputy director of the Cyberspace Security Professional Committee of the Chinese Command and Control Society
-

Live broadcast preview: Embracing AI—Exploring the application of large AI models in email anti-phishing detection












GIPHY App Key not set. Please check settings