read: 7
May 6th
RSA Conference 2024
will officially open
As the “Oscar of Safety”
RSAC Innovation Sandbox (Innovation Sandbox)
Has become an innovation benchmark in the network security industry
under innovation
Together with Mr. Green Alliance
Focus on new hot spots in network security
Insight into new trends in security development
walk intoBedrock Security

*RSAC 2024 Top Ten Innovation Sandbox
1. Company introduction
In March 2024, Bedrock Security announced it had received $10 million in seed funding led by Greylock. Greylock has previously invested in network security companies such as Palo Alto Networks, Okta, Obsidian Security, and Opal.

Figure 1 Bedrock founders Pranava Adduri and Ganesha Shanmuganathan
2. Background introduction
- Rapidly growing and flowing data volumes make it difficult to discover and classify sensitive data, especially as data grows, moves, and replicates in a distributed environment.
- Structured and Unstructured Data Types Structured data is easier to analyze and classify quickly than unstructured data, but most companies have both types of data, and traditional data security solutions are very rigid when it comes to identifying data types. It is difficult to provide adequate protection.
- Processing Massive Data Analyzing massive amounts of data is often slow, inaccurate, and expensive. Frequent rescans are needed to maintain accuracy, but rapidly growing data volumes and slow analysis times hinder processing of massive amounts of data. Fixed sampling, which only looks at a small portion of all data, is much faster but far less accurate, leaving sensitive data unprotected.
Traditional data security cannot meet today’s challenges
Although data is exploding exponentially, the corresponding security response is indeed growing linearly—the size of the security team cannot grow according to the amount of data. According to IDC, the global data volume will reach 175 ZB by 2025. According to one survey(2), the amount of data processed by enterprises each month has increased by an average of 63%, with 12% of respondents reporting a 100% increase in data volume. At the same time, businesses are facing a growing number of cyber threats targeting this data.
Existing traditional security tools are not specifically designed to analyze and protect an enterprise's data usage. Attacks are occurring with increasing frequency, and the attack surface continues to expand with the increase in data. In response to these security risks, regulations regarding data security are increasing(3), requiring companies affected by cyber incidents to respond in a shorter time frame. Response may not be as prompt for a variety of reasons, including a lack of cybersecurity talent (4). Delays in identifying and classifying sensitive data result in longer recovery, repair, respond, or resolve (MTTR) times.
Security teams must quickly identify and classify data and harden it as much as possible to ensure compliance with regulations and no over-privileged data access or data exposure. At the same time, security teams need to continuously evaluate data security incidents that violate policies. Delays in data access will cause friction between security and other business lines. Different teams want to have priority access to data, which leads to various teams competing for resources and more investment in data security. Growing data demands pose new challenges for security teams and may reduce the ability of cybersecurity teams to respond to other cyber threats and security issues.
Traditional data security solutions, including data security posture management (DSPM), fail to meet modern business needs. Traditional data security solutions often rely on (inaccurate) rules-based data classification, cannot guarantee accuracy and speed, and cannot handle large-scale data. Security teams spend a lot of time updating rules in response to changing patterns. But the results are often unsatisfactory because dynamic data usage disrupts static rules.
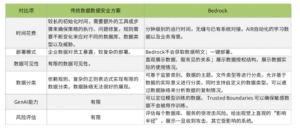
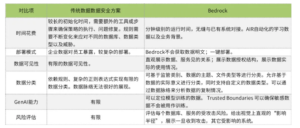
Traditional Data Security Solutions Versus Bedrock
3. “Frictionless” styleData Security

Figure 2 “Friction” between data scale and security resources
4. How does Bedrock do it?
The Bedrock platform uses existing APIs to discover structured and unstructured data sets, providing comprehensive data insights including data classification, context and data mapping, data type and context. Bedrock dynamically adjusts sampling up and down based on the characteristics of each specific file and data storage. For example, for structured data sets such as databases, Bedrock can analyze smaller samples and determine the type of data stored in the database with a very high probability, thereby classifying the data accurately and quickly. For unstructured data, Bedrock uses a larger sample to understand it. If the AIR engine identifies sensitive data in a specific folder, the sample size is increased to ensure that all sensitive data is identified and classified. The ability to adjust scans based on data type and content discovered accelerates the data discovery process, ensuring the accuracy and visibility of all data.
In addition to finding data, classifying it, and determining how the data flows, Bedrock uses large language models (LLM) and other artificial intelligence (AI) and machine learning (ML) methods to analyze the data and determine the data type of the file, what it contains content and the owner of the file. For example, a bank uses a customer's Social Security number in account information, but also stores the Social Security number of its employees. Although these data types are the same, the purpose and ownership of the data are completely different. The AIR engine helps classify data appropriately and coordinates the permissions you want to set based on the business purpose of the data.
Bedrock's Trust Boundaries allow policies to be written in natural language, providing an easy and flexible way to manage secure data access. The AIR engine's dynamic understanding of data eliminates the need for users to worry about how to define each data group, but only to focus on how the data is used and who can access it.
- Data reduction identifies all the data you have, determines which data is unnecessary, and deletes or moves it to cold storage, making it extremely difficult to access.
- Minimize Access Access controls are an important way to minimize data risk. Once you understand your data, how it flows, and who has access to it, you can determine who needs the data and limit access to those who truly need it.
- Hardening data encryption is a way to make data harder to steal, but doing that requires continuous discovery of what data is present throughout your environment.
Bedrock's AIR engine eliminates data risk by minimizing it by locating stale or ghost data; it also assesses the impact of identity access to set permissions based on the principle of least privilege and harden data so that it can be The impact of a data breach is minimized. The more users who have access to a sensitive data set, the more avenues an attacker has to compromise the account, ultimately compromising the data itself. The Bedrock platform minimizes this risk by reducing data, minimizing access and hardening it, allowing for easy remediation if any issues arise.
Discover and classify data on the customer's data side, and only send metadata to the Bedrock SaaS Platform. This means that Bedrock will not obtain customer data, protecting customer privacy. For example, if a field in the database is named “Passport Number”, Bedrock will only get the name of the field but not the actual value.
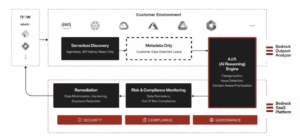
Figure 3 Bedrock product architecture
AIR (Artificial Intelligence Inference Engine)
AIR is the core of Bedrock, which understands the true meaning of data and the business value of data. AIR processes the metadata information of the customer environment, classifies it, analyzes security risks from multiple dimensions, and determines the priority of processing based on risk factors.
Remediation
For security incidents and risks discovered by AIR, Bedrock provides corresponding suggestions and remedial measures. Using the API integration tool provided by Bedrock, users can apply these remedial measures with one click, and can also generate corresponding work orders, which contain detailed instructions on how to solve these security issues.
Risk & Compliance Monitoring
Bedrock can detect hundreds of security violations, including unreasonable configurations, excessive permission configurations, etc. Bedrock's Trust Boundary (Bedrock Trust Boundary) can help customers quickly discover which data is important, and the Bedrock system ensures data security. For generative AI, Trust Boundary can be used to protect sensitive information of sources and results, core intellectual property information, etc.
“frictionless” security team collaboration
Bedrock helps different teams collaborate efficiently and securely. The security team can obtain security risk events; the compliance team can obtain compliance analysis reports and create new policies to respond to assessments and audits; the governance team can create data access policies based on users, data types, data sources and other factors.
5. Summary
references
(1) Bedrock Security Unveils the Industry’s First Frictionless Data Security Platform, Announces $10 Million in Seed Funding https://www.businesswire.com/news/home/20240326144629/en/Bedrock-Security-Unveils-the-Industry%E2%80%99s-First-Frictionless-Data-Security-Platform-Announces-10-Million-in-Seed-Funding
(2) The Impact of Data Growth on Enterprises https://www.dataversity.net/the-impact-of-data-growth-on-enterprises/
(3) Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure https://www.sec.gov/files/rules/final/2023/33-11216
(4) Amanda Steinman (2023) ISC2 Reveals Growth in Global Cybersecurity Workforce, But Record-Breaking Gap of 4 Million Cybersecurity Professionals Looms https://www.isc2.org/Insights/2023/10/ISC2-Reveals-Workforce-Growth-But-Record-Breaking-Gap-4-Million-Cybersecurity-Professionals




GIPHY App Key not set. Please check settings