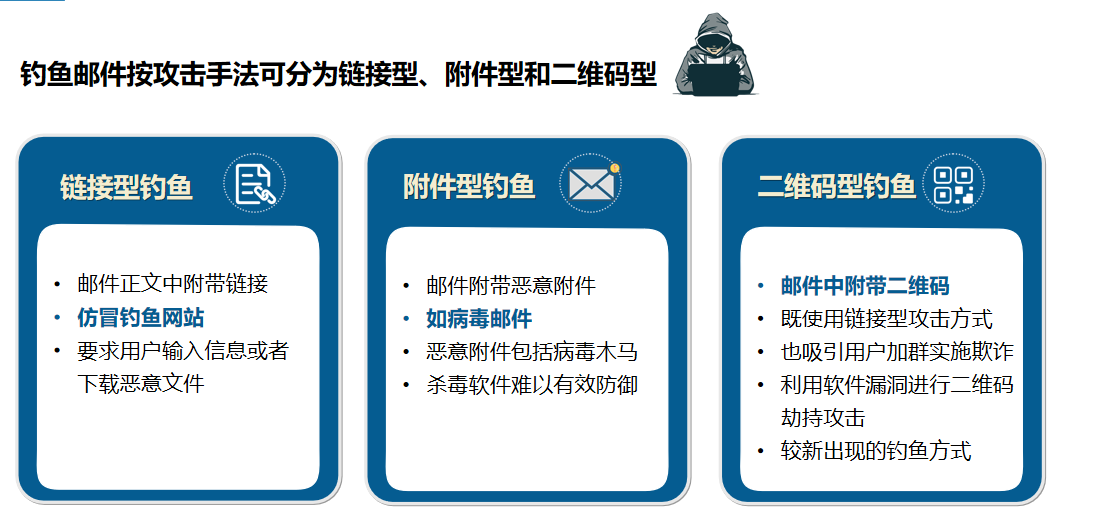
Introduction: Be wary of new subsidy scam emails, scanning the QR code to receive subsidies may be a phishing scam!
As life becomes more and more digital, it has never been easier to complete various businesses and services. With just a tap of the mobile phone screen, people can do things quickly and conveniently. However, while people are enjoying the convenience brought by this digitalization, some criminals are also waiting for the opportunity in secret, using various means to create fraud scams and trying to make profits from it.
Speaking of which, I wonder if you have ever received such an email, saying it is for usIssue social security subsidies and labor subsidiessome type of? Claiming to get money easily by just scanning the QR code? I feel so happy when I see that I can get money, but these days, pie does not fall in the sky, so I have to keep my eyes open to see clearly, so as not to fall into the trap accidentally.
“Chain phishing” is an emerging trend of subsidy fraud emails. This attack method usually involves account theft. The attacker first steals the email account of someone within an organization through various means, and then uses this account to send fraudulent emails to other email addresses under the same domain name.
These emails appear to come from trusted sources within the organization, and employees are relatively less vigilant about emails from the same domain name, which makes “chain phishing” attacks particularly dangerous.
In fact, since the beginning of 2021, subsidy fraud phishing has been the most harmful phishing email with the purpose of stealing funds. By 2023, the attack methods of this kind of subsidy fraud have begun to diversify, including large-scale phishing, and methods of sending within the stolen account domain; phishing texts and QR codes also include pictures, attachment documents, etc. form.
According to the monitoring of the Coremail Email Security Artificial Intelligence Laboratory, users use stolen accounts to send emails in the same domain. Because the credibility of emails in the same domain is high, users can easily believe them to be genuine. This makes it the phishing attack pattern with the largest number of financial loss incidents in 2023.
Your account*** anomaly alert!
Taking a specific case as an example, the attacker will first send a phishing email to the target. The email title is usually urgent, titled “Your account *** is abnormal!”
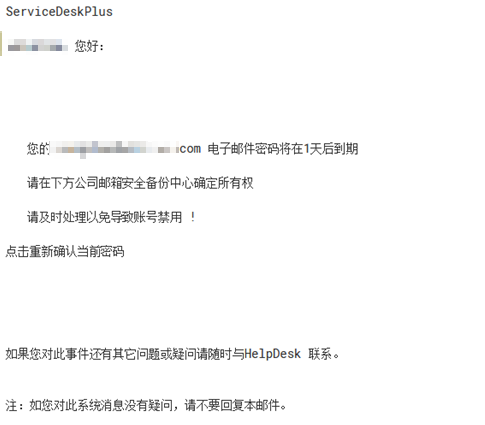
The link in the email body points to the phishing website https://www.nametopx.com/

This kind of title can easily arouse people's attention and nervousness. In the nervousness and anxiety, people ignore the steps to verify the authenticity of the email, and then follow the instructions in the email, and finally fall into the trap set by the scammer.
After defrauding the user's email account and password, the attacker logged into the victim's email address and sent batches of financial fraud emails to users in the domain through the organization's address book, titled “2023 Third Quarter Personal Labor Subsidy Application Notice.” The attacker will also change the name of the stolen account to the Finance Department to enhance the credibility of the phishing email.

As shown in the case, scammers will pretend to be the company's finance department and induce employees or the public to perform so-called “scan code authentication collection” by sending emails with QR codes. However, these QR codes often link to malicious websites.The goal is to steal your personal and financial information。
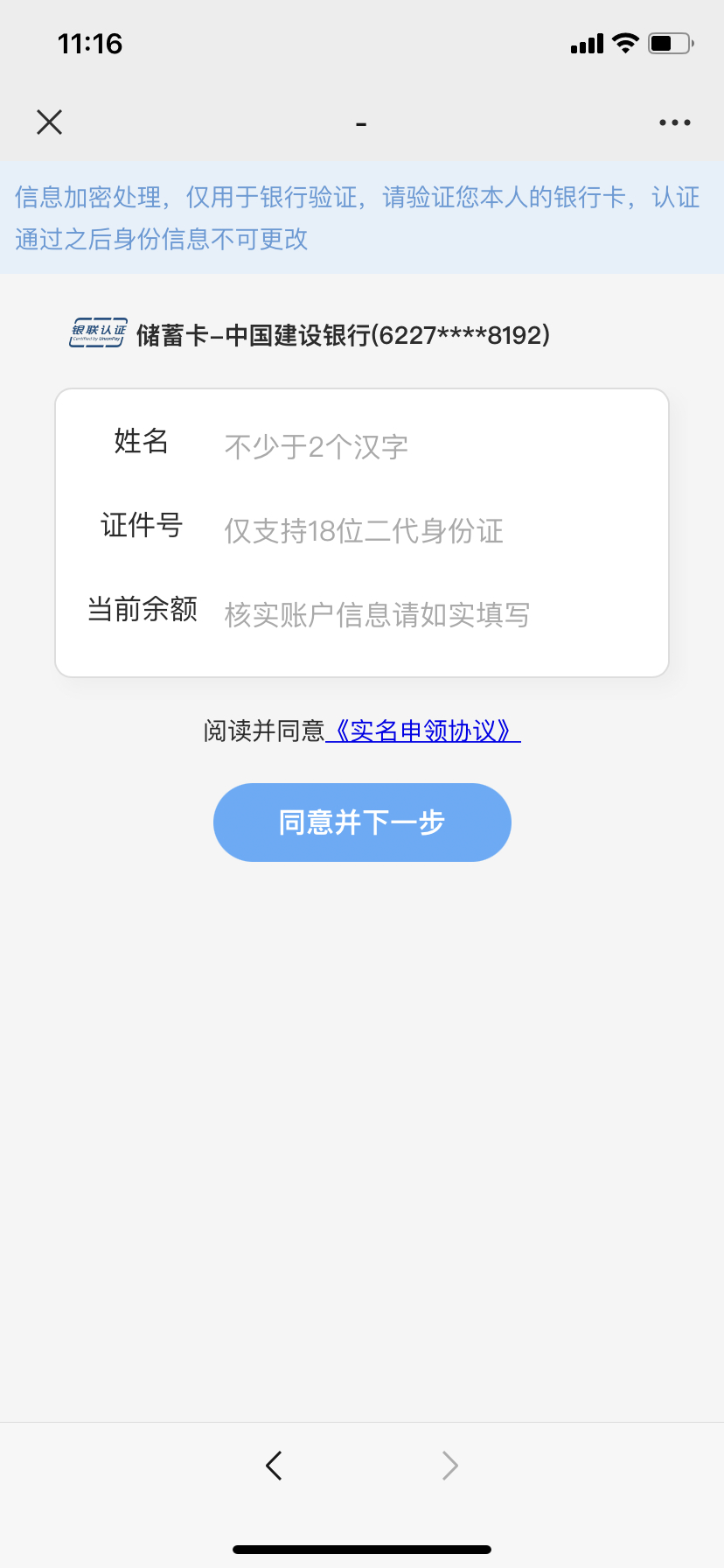
Once you follow the instructions in the email and scan the QR code, you will enter the fake Ministry of Human Resources and Social Security website. Enter your bank card number, ID number, mobile phone number, name and SMS verification code. Your bank account is likely to be compromised. With illegal access, your hard-earned money may evaporate in an instant.
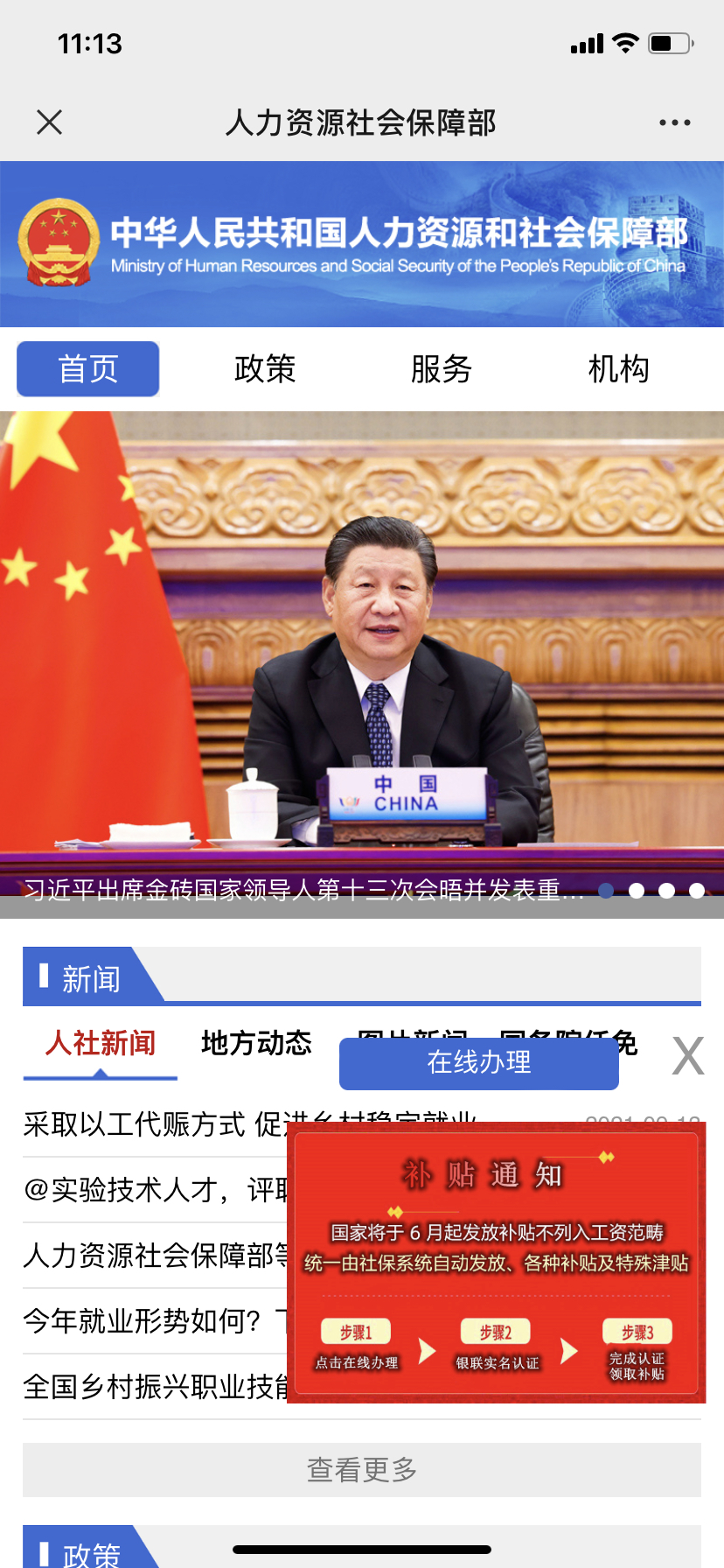
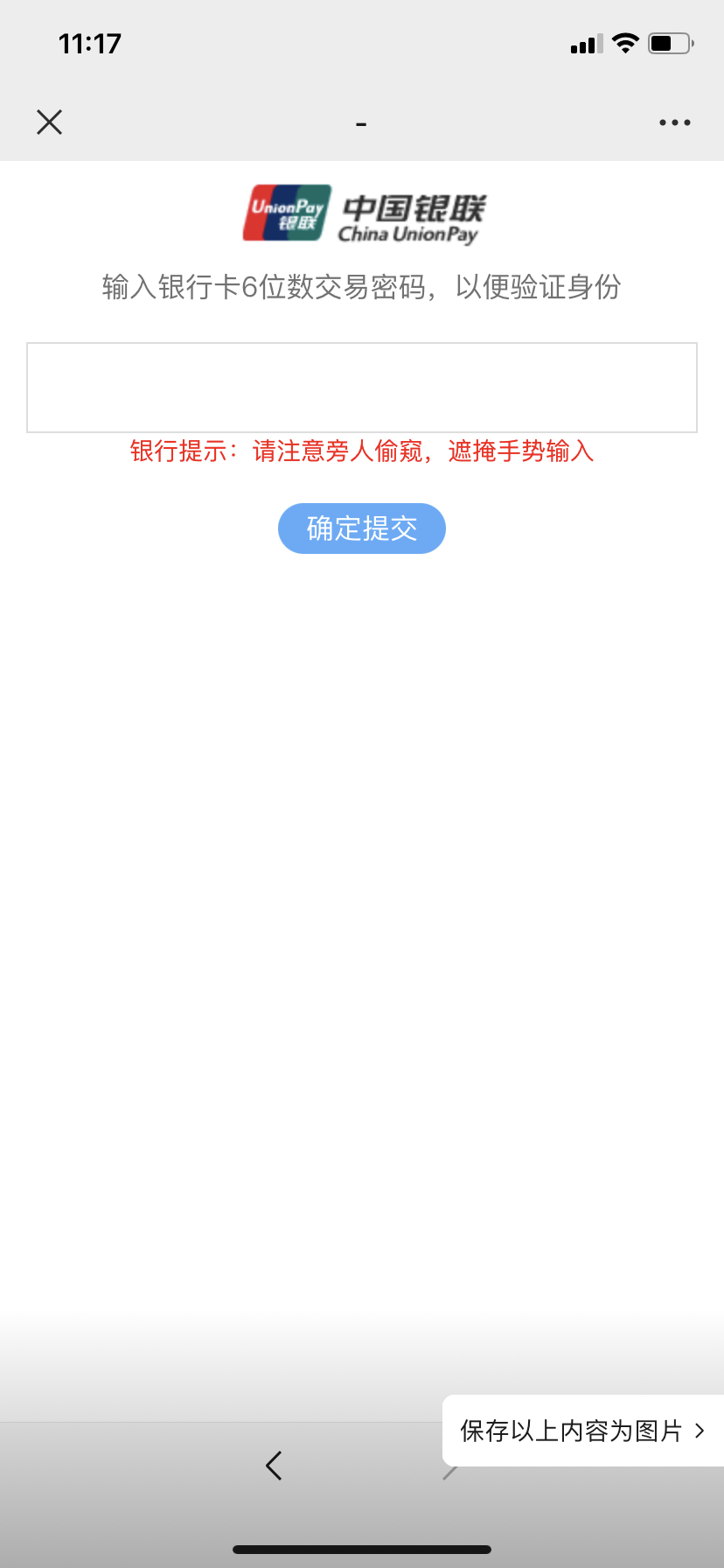
Nowadays, scammers are becoming more and more sophisticated. They do more than just send an email or a text message. Some have really worked hard to make the scam look more real, even pretending to be an official website, such as the website of the Ministry of Human Resources and Social Security.
Imagine you open a website that looks extremely official. The page design, font usage, and even the layout of each button are exactly the same. Then, suddenly, a bay window pops up, looking like an official notification to induce you to click in.
Once you click on the picture and click on the bay window, you can probably guess what happens next – the page will ask you to fill in some personal information, such as your name, ID number, bank account information, etc. At this time, you may still be thinking: “Wow, this official website is quite user-friendly. You can even apply for subsidies online.” However, stop for a moment and think about it. Really, official organizations would do this so easily. Are you asked to fill in such sensitive information online? Can you accept the risks hidden behind this?
1. Fraudulent techniques:
1. Email subject Re: Personal labor subsidy application notice for the third quarter of 2023
2. Attachment: Supplementary materials related to the third quarter personal labor subsidy registration statistics of the Ministry of Human Resources and Social Security in 2023.docx
3. Linked phishing – a new trend in subsidy fraud emails: usually combined with stolen accounts, sent to other mailboxes with the same domain name; guided through the QR code to enter the fake Ministry of Human Resources and Social Security website to defraud bank card information
2. Protection suggestions:
Facing the increasingly rampant subsidy fraud phishing emails, it is crucial to take effective protective measures.
01. Gateway identification and interception
First of all, tools like Coremail Email Security Gateway already have powerful interception capabilities and can effectively identify and block subsidized phishing scam emails. The email security gateway's intra-domain email detection function can provide an additional layer of protection against fraudulent emails from within the same organization, which is particularly effective in preventing internal phishing attacks that use stolen accounts.
02. Strengthen account security
Secondly, account security can be greatly enhanced by implementing two-factor authentication and using client-specific passwords. These measures provide double protection for account security and can effectively prevent unauthorized access even when account information is stolen.
03. Improve security awareness
Finally, strengthening security awareness training is key to preventing phishing attacks. By regularly showing and explaining typical phishing email cases to employees, we can help employees establish basic security awareness. In addition, utilizing a threat intelligence subscription service like CACTER CAC2.0 can keep organizations and employees informed of the latest phishing attack techniques and prevention strategies, thereby better protecting themselves from online scams.
If you encounter such a phishing scam email in the future, please delete the email immediately and do not try to scan any QR codes in it. If you receive information that appears to come from your workplace or other trusted institution, but you have doubts about its authenticity, the best course of action is to contact your employer directly to confirm the authenticity of the information, remain vigilant, and protect it with wisdom and caution. Your digital life does not leave any opportunities for scammers.
Typical cases of the year
The above cases are derived from the “2023 China Enterprise Email Security Research Report”. The report records 6 annual typical cases. For more annual typical cases, please go to the website to download the “2023 China Enterprise Email Security Research Report” to view.
If reprinted, please indicate the original address.


Thank you for your support, I will continue to work hard!
OpenWeChatScan and click on the upper right corner to share.
You may be interested
-

[Typical Case of the Year]Can you receive subsidies by scanning the QR code? Notify social security to process online?Beware of phishing scam
-

360 reveals the truth about “Volt Typhoon” and launches secure cloud anti-ransomware solution
-

Mobile application security compliance trends: The Cyberspace Administration of China and the Hong Kong Monetary Authority issued a document emphasizing data security. The results of spot inspections for personal information violations in March are released (fifth issue)
-

Leading the “security + AI” education revolution, 360 and Tangshan Vocational College jointly built the Digital Security Industry College
-

Secret Service Handbook | New threats emerge, overseas ultra-micro pinhole camera equipment
-

The 6th Beijing Cybersecurity Conference BCS2024 will be held on June 5. The theme of the conference is “AI-driven security”












GIPHY App Key not set. Please check settings