
Organizing events that gather cybersecurity leaders requires significant effort and sponsorships. Unfortunately, some events and communities exclude CISOs who work for security vendors. This stance, though well-meaning, harms the industry and allows hidden conflicts of interest to go unchecked. Here’s why and how we can address this issue to improve such events and the community at large.
CISOs of All Types
Industry veteran Andrew Hay once posted a tongue-in-cheek “CISO hierarchy of industry respect.” At the top were security leaders of Fortune 500 companies. Further down were CISOs at financial services or insurance firms. Lower, the CISOs at hardware vendors. Closer to the bottom were the CISOs working for a cybersecurity vendor; hi, that’s me!
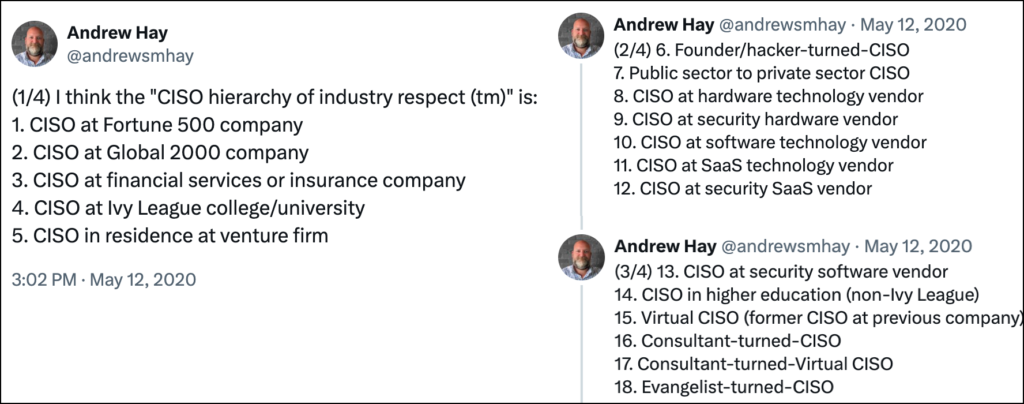
The respect hierarchy was meant as a joke, and CISOs took it as such. It was funny because there was something truthful about it. Some executives command more respect among their peers than others. CISOs who work at large organizations have to deal with more complexities and command larger budgets than those who work for smaller firms. Yet, no matter the type or size of the organization, CISOs are dealing with many challenges and have much to contribute to the community.
Sponsorship of CISO Events
Hosting events incurs costs for the venue, food, and organizer salaries. Typically, these costs are covered by vendor sponsorships, which allow vendors to present, advertise, and otherwise expand their brand equity.
Therefore, CISO gatherings sometimes include designated sessions where the sponsors discuss their commercial products. Sometimes, the organizers ask the sponsors to present “thought leadership” content that doesn’t overtly pitch products. For such presentations, the organizers often require that the speaker not be in sales or marketing. If the vendor has a CISO, that person is often a good candidate.
When well-orchestrated, this approach to covering event costs benefits all stakeholders: the organizers, attendees, and vendors.
Excluding Security Vendors’ CISOs from Events
Some events restrict CISOs from security vendors to only attend sessions sponsored by their employer. In doing this, the organizers aim to:
- Maintain a revenue source whereby the only way for security vendors to access attendees is through sponsorship.
- Allow open discussions about security vendors without their representatives.
- Ensure that the attendees are practicing CISOs, not sales or marketing people with “CISO” in their titles.
These are reasonable objectives; however, banning security vendors’ CISOs from events is a poor way of achieving them.
This jackhammer, all-or-nothing approach creates the appearance of an environment that facilitates an unbridled exchange of ideas and opinions. Yet it doesn’t address overt conflicts of interest and vendor relationships of attendees who might:
- Be affiliated with security vendors as investors or advisers, which is not unusual for CISOs.
- Work for non-security vendors that offer products or services to the event’s attendees.
- Be non-practitioners even if they have “CISO” in the title without working for a security vendor.
When events ban CISOs of cybersecurity vendors but allow the possible issues above unchecked, they merely create the appearance of establishing an environment free of vendors’ involvement or other undesirable interference.
Moreover, all of us who work for commercial companies are somebody’s vendors. And we want our vendors to have strong security programs with knowledgeable leaders. We often want to meet these leaders, establish relationships with them, and perhaps even learn from them. By failing to create an environment that allows CISOs of all organizations, even security vendors, to participate, organizers get in the way of our industry’s growth.
How to Organize Events for All CISOs
There is another way. Many CISO communities successfully include all types of security leaders. How do they facilitate fruitful discussions while allowing security vendors’ CISOs, such as me, to participate? They enforce transparent rules of conduct, which require attendees to:
- Avoid selling or promoting their employer’s products outside designated forums.
- Disclose conflicts of interest or abstain from related discussions.
- Exit discussions if their presence causes discomfort due to conflicts of interest.
- Engage respectfully and professionally, acknowledging diverse opinions and affiliations.
Establishing these rules requires intentionality, but it is possible and effective. I’ve seen it create thriving communities that benefit all stakeholders and advance our industry. If you’re a CISO attending a security event, ask whether security vendors’ CISOs are allowed to participate in the entire event. If not, encourage organizers to adopt these rules or refer them to this article.
Updated June 21, 2024
About the Author
I transform ideas into successful outcomes, building on my 25 years of experience in cybersecurity. As the CISO at Axonius, I lead the security program to earn customers’ trust. I’m also a Faculty Fellow at SANS Institute, where I author and deliver training for incident responders. The diversity of cybersecurity roles I’ve held over the years and the accumulated expertise, allow me to create practical solutions that drive business growth.





GIPHY App Key not set. Please check settings