read: 12
1. Vulnerability Overview
Recently, NSFOCUS CERT detected that Atlassian released a security bulletin to fix the remote code execution vulnerability (CVE-2024-21683) in Confluence Data Center and Server, with a CVSS score of 8.3. An authenticated attacker can achieve remote code execution by constructing malicious requests, which has a significant impact on the confidentiality, integrity, and availability of the target system. Relevant users are requested to take protective measures as soon as possible.
Atlassian Confluence is an enterprise-level content collaboration tool developed by Atlassian that provides a central hub for team members to create, share and collaborate on documents in a shared workspace. This tool can be integrated into other Atlassian products, including Jira, Trello, Stride, etc.
Reference links:
https://jira.atlassian.com/browse/CONFSERVER-95832
2. Scope of influence
Affected versions
- Confluence Data Center = 8.9.0
- 8.0 <= Confluence Data Center <= 8.8.1
- 7.1 <= Confluence Data Center <= 8.7.2
- 6.0 <= Confluence Data Center <= 8.6.2
- 5.0 <= Confluence Data Center and Server <= 8.5.8 (LTS)
- 4.0 <= Confluence Data Center and Server <= 8.4.5
- 3.0 <= Confluence Data Center and Server <= 8.3.4
- 2.0 <= Confluence Data Center and Server <= 8.2.4
- 1.0 <= Confluence Data Center and Server <= 8.1.4
- 0.0 <= Confluence Data Center and Server <= 8.0.4
- 20.0 <= Confluence Data Center and Server <= 7.20.3
- 19.0 <= Confluence Data Center and Server <= 7.19.21 (LTS)
- 18.0 <= Confluence Data Center and Server <= 7.18.3
- 17.0 <= Confluence Data Center and Server <= 7.17.5
Note: Other older versions that no longer support maintenance are also affected
Not affected version
- Confluence Data Center >= 8.9.1
- Confluence Data Center and Server >= 8.5.9 (LTS)
- Confluence Data Center and Server >= 7.19.22 (LTS)
3. Vulnerability Detection
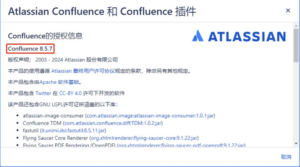
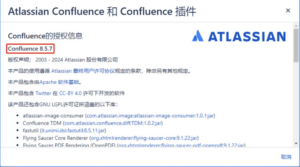
- Manual inspection
Users can check whether the current service is affected by this vulnerability by checking whether the current Confluence version is within the affected range. Click and select “About Confluence” to view the current version:
4. Vulnerability protection
- Official upgrade
At present, the official has released a new version to fix this vulnerability. Affected users are requested to upgrade the version in time for protection. The official download link is: https://www.atlassian.com/software/confluence/download-archives
statement
This security bulletin is only used to describe possible security issues. NSFOCUS Technology does not provide any guarantee or commitment for this security bulletin. Any direct or indirect consequences and losses caused by the dissemination and use of the information provided in this security bulletin are the responsibility of the user himself. NSFOCUS Technology and the author of the security bulletin do not assume any responsibility for this.
NSFOCUS reserves the right to modify and interpret this security announcement. If you wish to reprint or disseminate this security announcement, you must ensure the integrity of this security announcement, including all contents such as the copyright statement. Without the permission of NSFOCUS, you may not arbitrarily modify or add or subtract the contents of this security announcement, and you may not use it for commercial purposes in any way.





GIPHY App Key not set. Please check settings