FIN7 targeted a large U.S. carmaker phishing attacks

BlackBerry reported that the financially motivated group FIN7 targeted the IT department of a large U.S. carmaker with spear-phishing attacks.
In late 2023, BlackBerry researchers spotted the threat actor FIN7 targeting a large US automotive manufacturer with a spear-phishing campaign. FIN7 targeted employees who worked in the company’s IT department and had higher levels of administrative rights.
The attackers employed the lure of a free IP scanning tool to infect the systems with the Anunak backdoor and gain an initial foothold using living-off-the-land binaries, scripts, and libraries (lolbas).
FIN7 is a Russian criminal group (aka carbanak) that has been active since mid-2015, it focuses on restaurants, gambling, and hospitality industries in the US to harvest financial information that was used in attacks or sold in cybercrime marketplaces.
Fin7 was observed using the PowerShell script POWERTRASH, which is a custom obfuscation of the shellcode invoker in PowerSploit.
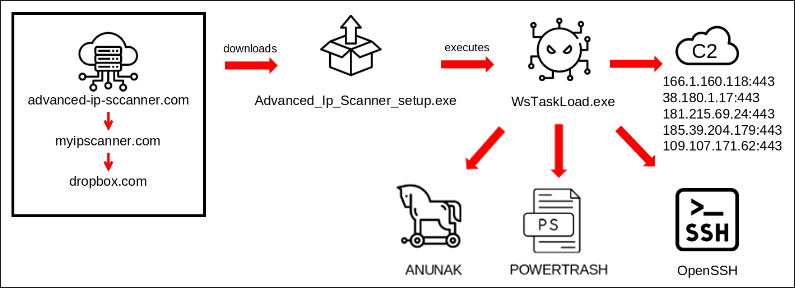
In the attacks analyzed by BlackBarry, threat actors used a typosquatting technique, they used a malicious URL “advanced-ip-sccanner(.)com” masquerading as the legitimate website “advanced-ip-scanner(.)com”, which is a free online scanner.
Upon visiting the rogue site, visitors are redirected to “myipscanner(.)com”, which in turn redirected them to an attacker-owned Dropbox that downloaded the malicious executable WsTaskLoad.exe onto their systems.

Upon execution, the executable initiates a complex multi-stage process comprising DLLs, WAV files, and shellcode execution. This process culminates in the loading and decryption of a file called ‘dmxl.bin,’ which contains the Anunak payload.
The threat actors used WsTaskLoad.exe to install OpenSSH to maintain persistence, they used scheduled task to persist OpenSSH on the victim’s machine.
While historical data demonstrate that FIN7 often employs OpenSSH for lateral movement, no such activity was detected in this particular campaign. OpenSSH is also used for external access.
“While the tactics, techniques, and procedures (TTPs) involved in this campaign have been well documented over the past year, the OpenSSH proxy servers utilized by the attackers have not been disseminated.” concludes the report that also includes recommendations for Mitigation and IoCs (Indicators of Compromise). “BlackBerry thinks it prudent to enable individuals and entities to also identify these hosts and protect themselves.”




GIPHY App Key not set. Please check settings