
Introduction: GitHub automatically generates a download link after a user adds a file to an unsaved comment, rather than generating a URL after posting the comment.
Security research agency recently reported how threat actors abused GitHub flawsto push malware while making it appear to be hosted on an official source code repository from a trusted organization.
While most malware-related activity is based on Microsoft GitHub URLs, this “flaw” could be abused by any public repository on GitHub or GitLab, allowing threat actors to create very convincing lures.
GitLab comments can also be abused to push malware
For example, the following URLs used in the attack make it appear that these ZIPs reside in Microsoft's source code repository:
https://github(.)com/microsoft/vcpkg/files/14125503/Cheat.Lab.2.7.2.zip https://github(.)com/microsoft/STL/files/14432565/Cheater.Pro.1.6.0.zip
However, upon investigation, these files (which belong to the malware) were not found in Microsoft's code repository.
Instead, the content resides on GitHub's CDN and was likely uploaded by threat actors abusing the platform's “comments” feature.
When leaving a comment on a commit or pull request, GitHub users can attach a file (archive, document, etc.) which will be uploaded to GitHub's CDN and associated with the related project using a unique URL in the following format: ' https: // www.github.com/{project_user}/{repo_name}/files/{file_id}/{file_name}. '
For videos and images, the files will be stored under the /assets/ path.
GitHub automatically generates a download link after a user adds a file to an unsaved comment, rather than generating the URL after posting the comment, as shown below. This allows threat actors to attach their malware to any repository without the user's knowledge.
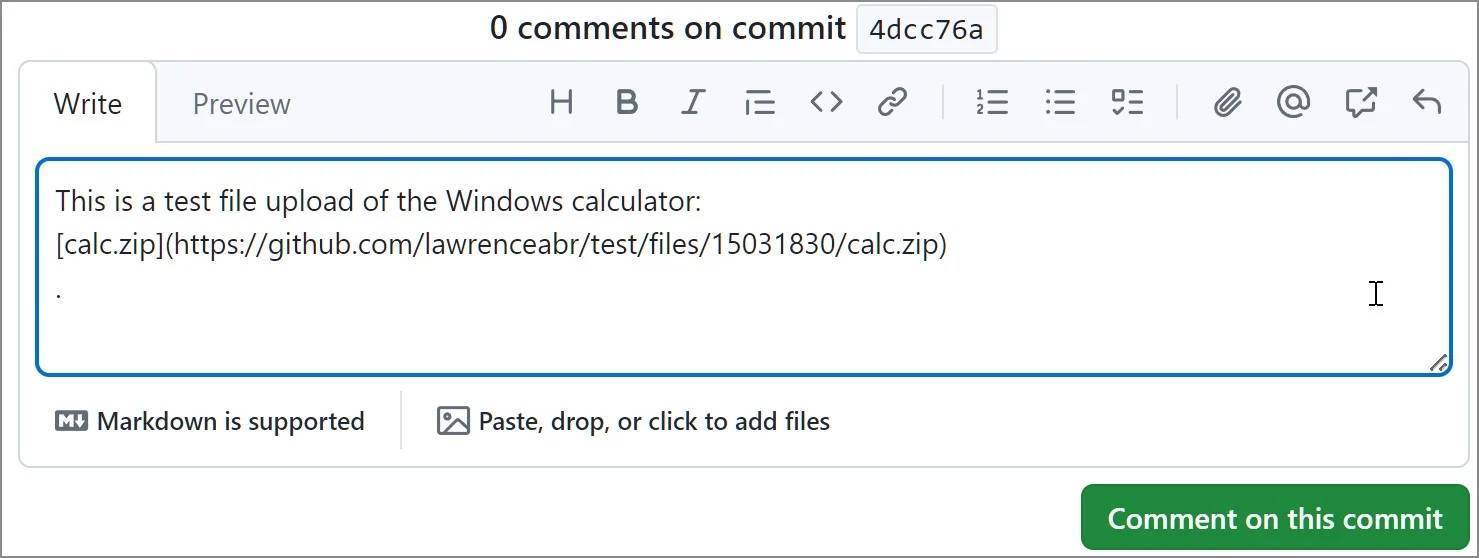
Automatically generated download link source when adding files to comments
Even if the comment is never actually posted or is later deleted by the user (or attacker), the link to the file will still work.
Sergei Frankoff of UNPACME, an automated malware analysis service, went live on the vulnerability last month and said that threat actors are actively abusing the vulnerability.
In addition, GitLab is not immune to this problem, and users can abuse the “comments” function on GitLab in a similar way.
In testing, users were able to upload files to GitLab's CDN, but it appeared that the files existed in the GitLab repositories of popular open source projects such as Inkscape and Wireshark:
https://gitlab(.)com/inkscape/inkscape/uploads/edfdbc997689255568a7c81db3f3dc51/InkScape-2024-Latest.exe https://gitlab(.)com/wireshark/wireshark/uploads/b4162053fbb4dc6ee4f673c532009e16/WireShark-v4.2.4-stable-release.exe
The file used in the test is a benign JPG image that has been renamed to .exe to demonstrate how threat actors can abuse this feature to mislead users into downloading fake versions of software with malware.
Such files uploaded to GitLab CDN follow the format:
https://gitlab.com/{project_group_namr}/{repo_name}/uploads/{file_id}/{file_name}
The file_id here looks like an MD4 or MD5 hash, rather than a simpler numeric identifier.
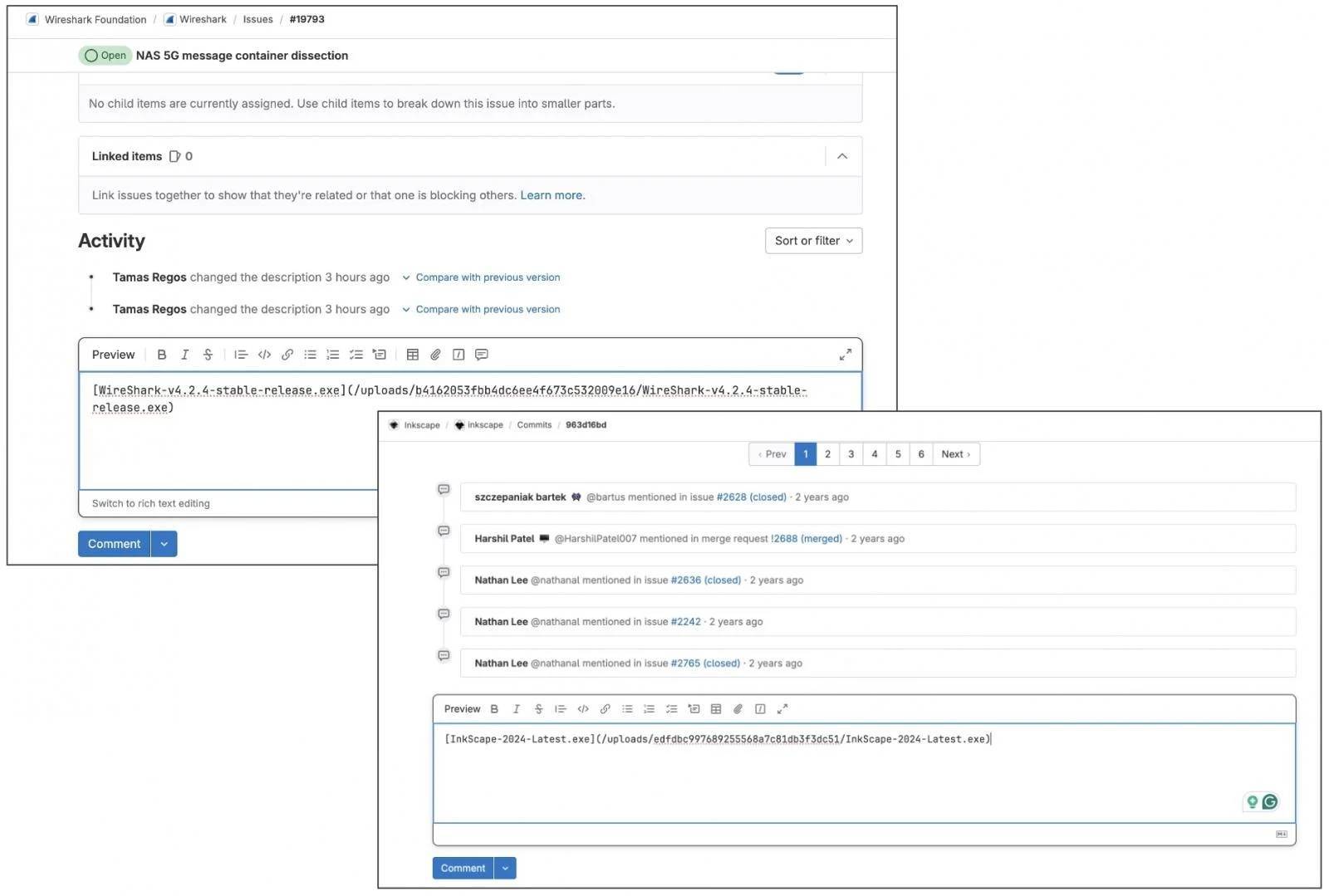
Automatically generated download link when adding files to GitLab comments
Much like GitHub, the resulting GitLab file link will remain active even if the attacker never posts the comment or later deletes the comment.
GitLab does prompt users to log in before they can upload or download these files, but that doesn't stop threat actors from uploading these files.
Since almost every software company uses GitHub or GitLab, this flaw allows threat actors to develop extremely sophisticated and seemingly trustworthy decoys.
For example, a threat actor could upload a malware executable to NVIDIA's driver installer repository that pretends to be a new driver that fixes an issue in a popular game. Alternatively, a threat actor could upload a file in a comment on the Google Chromium source code and pretend it is a new beta version of the web browser.
These URLs also appear to belong to the company's repositories, which makes them appear more authentic. Even if companies learn that their repositories are being abused to spread malware, they can't find any settings that allow them to manage or delete files attached to their projects.
Article translated from: https://www.bleepingcomputer.com/news/security/gitlab-affected-by-github-style-cdn-flaw-allowing-malware-hosting/ If reprinted, please indicate the original address


Thank you for your support, I will continue to work hard!
OpenWeChatScan and click on the upper right corner to share.
You may be interested
-

GitLab affected by GitHub-style CDN flaw that allowed malware to be hosted
-

Avoid reusing passwords for multiple accounts
-

Free VPN app turns user devices into criminal agents
-

Hackers abuse QEMU to launch network attacks on enterprises
-

Security Trends Review | “National Cybersecurity Standardization Technical Committee 2024 Work Points” released that cybercriminals impersonated LastPass employees to invade the password library
-

Cisco Duo third-party data breach exposes SMS MFA logs










GIPHY App Key not set. Please check settings