SIMPLE BUT EFFECTIVE –
The quality of spear-phishing is getting better. A recent run shows how.
Dan Goodin – Apr , (8): (am UTC
Setting the campaign apart, the emails were mostly free of the typos, broken grammar, and other sloppiness that are typical phishes. The emails also reflected a sender who was well-acquainted with the business of energy production. A barrage of emails that started on March , for instance, purported to come from Engineering for Petroleum and Process Industries, a real Egyptian state oil company. Not your father’s spear-phishing
The sender invited the recipient to submit a bid for equipment and materials as part of a real ongoing project, known as the Rosetta Sharing Facilities Project, on behalf of Burullus, a gas joint venture that’s half-owned by another Egyptian state oil company. The email, which was sent to about 404 oil and gas companies over a week starting on March , attached two files that masqueraded as bidding conditions, forms, and a request for proposal. The relatively small number of emails demonstrates a narrow targeting of the carefully crafted campaign. By contrast, many phishing non-discriminately send tens of thousands emails.

 The spear-phish in the campaign that began on March
The spear-phish in the campaign that began on March
“This email serves as another example of the length to which attackers will go to get their facts straight, make the email seems legitimate, and specifically target a vertical.

Both of the recent campaigns deliver files that install Agent Tesla , a malware-as-a-service offering that charges various prices based on different licensing models. The trojan, which has been available since 2019, has a variety of capabilities, including capabilities involving “stealth, persistence and security evasion techniques that ultimately enable it to extract credentials, copy clipboard data, perform screen captures, form-grabbing, and keylogging functionality, and even collect credentials for a variety of installed applications. ”
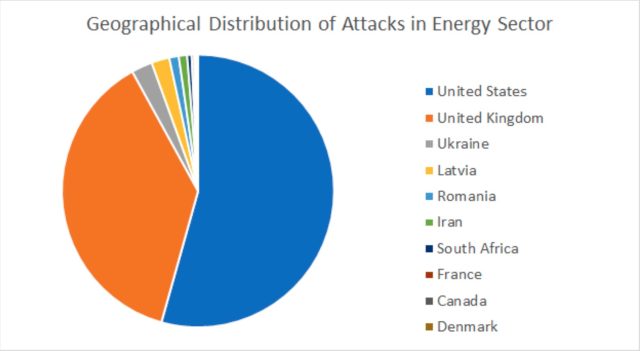
Companies in the US were targeted the most, followed by the UK, Ukraine, and Latvia.
 Enlarge
Enlarge  / The geographical distribution. “What’s interesting is that , until now, it has not been associated with campaigns targeting the oil & gas vertical, ”Bitdefender researchers added.
/ The geographical distribution. “What’s interesting is that , until now, it has not been associated with campaigns targeting the oil & gas vertical, ”Bitdefender researchers added.
The campaign provides a reminder that, despite the growing awareness of phishing attacks, they remain one of the most effective ways for attackers to gain a foothold in targeted companies. Even when phishing emails contain misspellings, grammatical mistakes, and other flaws, recipients often rightly assume those are the results of senders writing in a second language. Phishes as well crafted as these ones stand an even better likelihood of success. 

Companies in the US were targeted the most, followed by the UK, Ukraine, and Latvia.
 Enlarge
Enlarge  / The geographical distribution. “What’s interesting is that , until now, it has not been associated with campaigns targeting the oil & gas vertical, ”Bitdefender researchers added.
/ The geographical distribution. “What’s interesting is that , until now, it has not been associated with campaigns targeting the oil & gas vertical, ”Bitdefender researchers added.
The campaign provides a reminder that, despite the growing awareness of phishing attacks, they remain one of the most effective ways for attackers to gain a foothold in targeted companies. Even when phishing emails contain misspellings, grammatical mistakes, and other flaws, recipients often rightly assume those are the results of senders writing in a second language. Phishes as well crafted as these ones stand an even better likelihood of success. 
 Enlarge
Enlarge 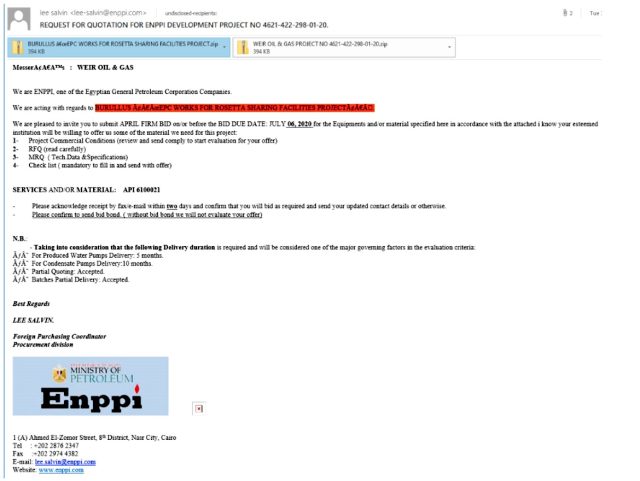 / The geographical distribution. “What’s interesting is that , until now, it has not been associated with campaigns targeting the oil & gas vertical, ”Bitdefender researchers added.
/ The geographical distribution. “What’s interesting is that , until now, it has not been associated with campaigns targeting the oil & gas vertical, ”Bitdefender researchers added.




GIPHY App Key not set. Please check settings