In May, Luna began to prepare for the second SRC Vulnerability Exploration Practice Class. He said: “The new course is amazing, it may change the current situation of network security!”
At the beginning of the year, Yue Shen decided to share his experience in digging holes through training. Almost all white hats who have achieved some results will consider doing training, no matter what the considerations are. Yue Shen did not shy away from revealing that he did training to make money. However, whenever a student hesitated to buy a course, he would persuade the student to think it over again, or even give up.
“Because I hope that those who can enter this industry are people who truly love this industry.”
Everyone involved in this industry clearly feels that there is an endless supply of training in this industry. Fame can be converted into traffic and wealth, but it can also lead to suspicion of “scamming”. For a while, a Tencent document about the evaluation of network security training institutions circulated online, and the words used were very straightforward and even rude. Yue Shen likes to participate in this kind of “excitement”. He happily marked his name and wrote, “It's okay, I am Yue Shen, everyone can speak freely.” At the end, he seemed to be unsatisfied and continued to add, “If no one criticizes me, I will do it myself. I can only point out business logic loopholes and show off everywhere.”

Below is what Yue Shen shared about his experience after his first training session.
Part 1
When I first started this training, you were always worried that my price was too high and not many people would sign up. You see, the facts slapped you in the face. Haha~
I am quite confident in myself. Let's not talk about my achievements and reputation here. Just talking about the content of this course, I can guarantee that this is absolutely not available outside. Anyway, when someone asks me which course is better between mine and other teachers, I always recommend other teachers' courses to them. I think those who ask me such questions have no vision and are not suitable to be my students~
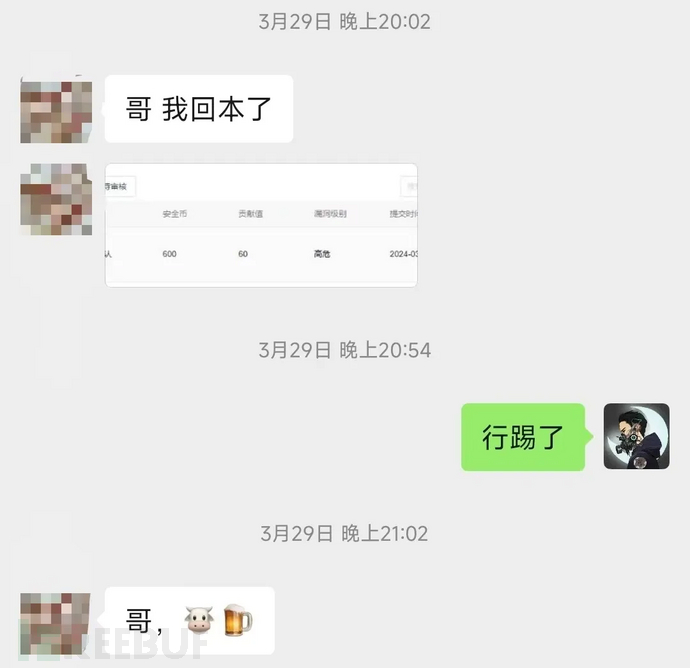
The first training session went very well and I was very happy. Each class was originally scheduled to last for 1 hour, but no one wanted to leave, so our course progressed much faster.Students with absolutely no foundation also made their money backSome students found the src ranking, and some students said that they can also apply code auditing and AI after learning, because the logic is universal.Really benefit from this courseI think it's worth it.
Part 2
In the second phase, our course has been upgraded on the basis of the original one. The core content of the first phase will be retained, and three parts of content will be added.
The long-awaited “Gaming Safety” course is here
Game vulnerability discovery is a new track. Someone asked me if I have discovered all the vulnerabilities in games so I came out to talk about mobile game vulnerability discovery?
 White hats who know me well know that I am a lazy person. I usually like to lie down and watch movie commentaries when I have nothing to do. I find game vulnerabilities just to exercise my thinking. I like the process of playing and digging holes at the same time, which is not boring. So after getting the TSRC year-end bonus to prove that I am still “sharp-sworded”, I stopped finding game vulnerabilities and continued to lie down.
White hats who know me well know that I am a lazy person. I usually like to lie down and watch movie commentaries when I have nothing to do. I find game vulnerabilities just to exercise my thinking. I like the process of playing and digging holes at the same time, which is not boring. So after getting the TSRC year-end bonus to prove that I am still “sharp-sworded”, I stopped finding game vulnerabilities and continued to lie down.
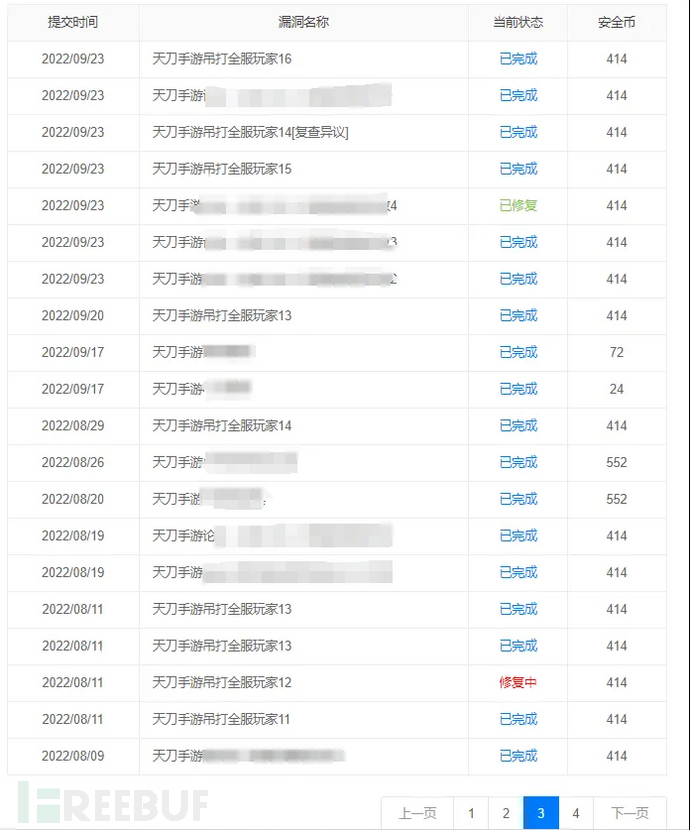
Game vulnerabilities are a huge gap for SRC vulnerability mining. Currently, many manufacturers have game businesses, but there are only a few people who can mine game vulnerabilities, not to mention being able to mine many vulnerabilities. Therefore, the competition for game vulnerabilities in the market is not that fierce. At the end of the first training session, I gave the trainees two lessons. The first lesson was how to use the tool, and the second lesson was the idea of mining vulnerabilities.
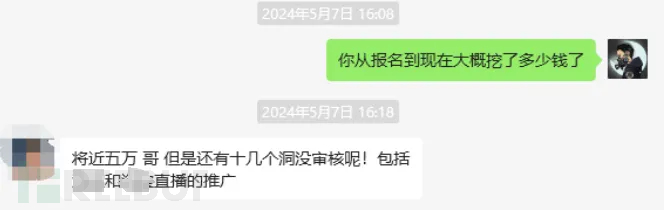
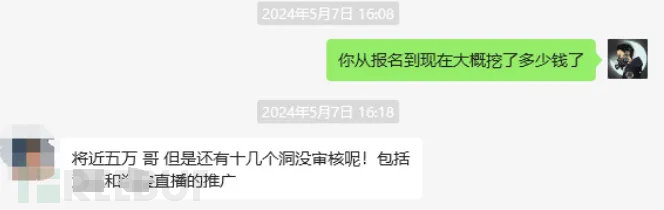
This is a small part of the screenshots of students digging for tsrc game vulnerabilities, so I plan to post them in the second issue.An in-depth explanation of the game part。
Moreover, finding game vulnerabilities does not require deep basic knowledge, and the tools are very simple. What we are finding are business logic vulnerabilities, and we mainly rely on ideas to find errors and harm points in his business logic.
You don’t need to know reverse engineering or binary basics, because I don’t know either, but I can still beat all the major domestic mobile game manufacturers. As I said, ideas are the most important.
New trick – “memory safety”
Last year, I discovered that chat records of many chat software can be forged. On this basis, I found that many chat software can send messages without authorization (changing one's identity to anyone else's identity). With continuous in-depth testing, I found that there are so many ridiculously simple vulnerabilities in protocols other than http.
Why has such a simple vulnerability been around for so long? I thought about it and it was probably because traditional testing uses packet capture tools, and the packets that can be captured are nothing more than two types, HTTP and websocket packets. For functions that cannot be captured, it seems that no one has a way to test them. Based on this idea, I decided to retest the apps of various manufacturers. After the test, I was shocked. They were all the simplest vulnerabilities, such as unauthorized use of other people's wallets, unauthorized live broadcasting, unauthorized message sending, and unauthorized kicking of people.
These vulnerabilities really shocked me. It turns out that these companies only conduct security tests on HTTP interfaces, and have never tested interfaces of other protocols. So I think,Maybe this will really usher in a new era of network security, where network security practitioners will no longer need to capture packets and modify parameters for testing!!!
Some people may think that they can learn the technology for free after it is made public. Of course, it is possible, but it may take a year for the technology to be made public, and by then the vulnerabilities will have been cleaned up by the students who have registered for the course. For those who do not want to exploit SRC vulnerabilities, they can wait until the day when the technology is made public, and it will not have any impact.
Second Course Easter Egg Release
I will invite7 top white hat experts share their insights on different topicsas an Easter egg for our students. You should know how difficult it is to listen to their special topic sharing, but students of our course can also interact with these experts to answer questions. Let me reveal a simple one. This course will invite a big guy to share with you the application of AI and bypass ideas. I believe it will help you broaden your horizons and open up your thinking.
Our courses can be studied repeatedly throughout one’s life, so the students who signed up for the first period really made a lot of money. Not only can they learn early and dig their holes early, but it is also equivalent to me helping them update their “bullet library” for free.
The second course, Mobile Game Security, was originally priced at 5888. The content of memory security is actually my “secret weapon”, which is unique in the market.Learn to earnthe value is hard to estimate. But we finally decided to package the first vulnerability mining course and give it to everyone.The package price of the four major courses (Vulnerability Mining Practice Course & Mobile Game Security & Memory Security & Top White Hat Special Topic Sharing) is 8888, and the early bird price before the course starts is 7888, and the group price of three people is 7288It is strongly recommended that you register in advance and receive the pre-class information package in advance to prepare for the course. You may be able to dig a few holes in advance, and then you can also participate in our pre-class sharing session before the course starts.
Recently, I have heard a lot of negative comments about the cybersecurity industry. My personal feeling is that more and more people are entering the industry, but the industry is indeed in a downturn. There are few new apps, and the update progress has slowed down, resulting in fewer and fewer vulnerabilities. I think you still need to have your own unique technology. Although everyone says that digging holes has become more difficult, you can see that the income of the big guys has not been affected. The ones who are affected are always those who do not meet the technical standards, so improving your own strength can avoid being eliminated.
So, let’s witness this new era together. Just like when we first learned how to capture packets, we will work together to discover new vulnerabilities little by little. I believe that in the future, there will be many special ideas for discovering vulnerabilities in new technologies.
Course Instructor
Lecturer – Luna
● Once worked in a listed company and was responsible for the security of mobile games. With millions of options, the risk of external plug-ins was zero for two consecutive years.
● Mining SRC to obtain a total of RMB 1 million in vulnerability bonuses
● 15 years of experience in mobile game vulnerability discovery, 7 years of experience in business logic vulnerability discovery
● Ranked first in Momo SRC annual ranking for 6 consecutive years
● Ranked first in the 2019-2020 Ele.me SRC annual ranking
● Ranked fourth in Meituan SRC annual ranking in 2019
● No. 1 in Mafengwo SRC overall ranking
● 2020 i Spring and Autumn Tour First Place
● Commander of the Double Eleven Defense War in 2020
● Ranked second in Ctrip SRC annual ranking in 2021
● 2022 Tencent SRC Sniper Elite
Course Introduction
1. This course is aimed at all groups who are interested in network security, with no basic knowledge, or working in a company, who understand technology but do not know how to exploit SRC vulnerabilities, or who have ideas but do not understand business logic.
2. This course focuses on business logic vulnerability discovery and is supplemented by game security. The course will start from scratch and proceed step by step, so that everyone who wants to enter this industry can do so easily.
3. In addition to traditional testing, this session will introduce memory testing methods, which may change the current state of network security and overturn cognition. There is still no requirement for the basics. (Let future security practitioners test not limited to HTTP protocol)
course features
Leading network security practitioners into the next era of vulnerability discovery, a large number of vulnerabilities can be easily discovered for software that we were previously helpless against. In addition, we will explain mobile game security and take everyone to a deeper understanding of mobile game vulnerabilities.
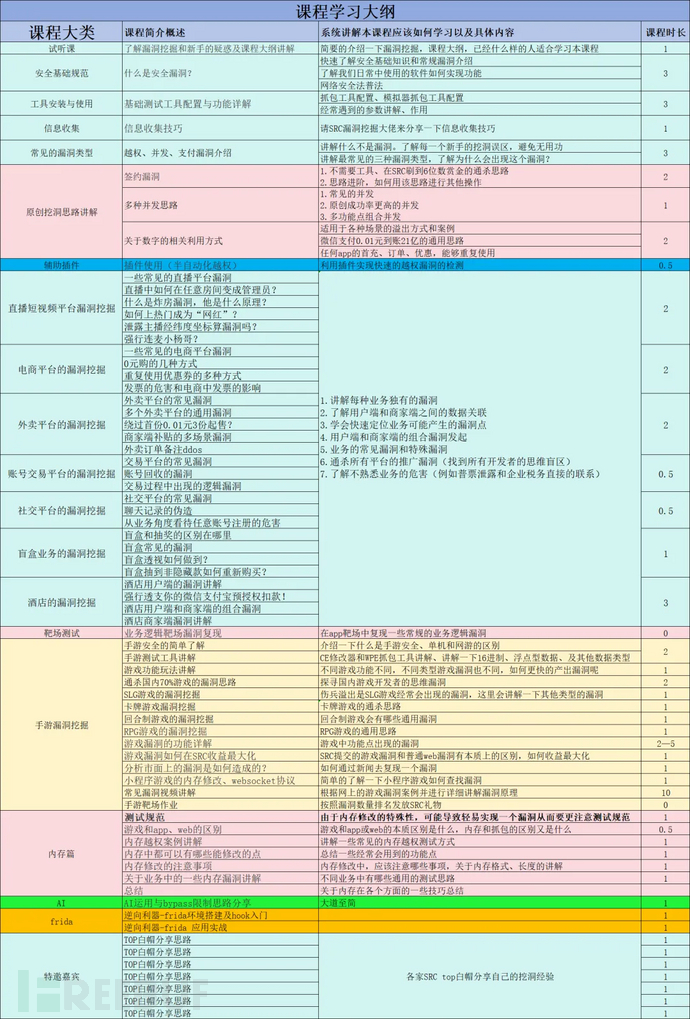
Course Outline
Course Benefits
- Pay once and take classes for life; (You can take new SRC courses for free after this registration)
- The test account of some merchant platforms and the privileged account make it easier for you to find vulnerabilities;
- Mobile game vulnerability shooting range, reproduce game vulnerabilities;
- 1V1 individual Q&A: Every student’s question will be answered from the moment they register;
- SRC peripheral gifts are given according to the completion of homework: after-class homework, some courses will assign homework;
- Game character memory ID sharing: knowing the ID can help locate game vulnerabilities more quickly;
- Job recommendation: You can get internal referral qualification when the company recruits, which will make you one step ahead of others.
Course start time
The expected start date is July 20, but it is possible to start classes earlier;
1. There are three online live classes every week, from 8 to 10 p.m. If you miss them, you can watch the recorded classes.
2. Recordings can be replayed permanently.
Registration consultation
The original price of the course is 8888
July 20thLimited time offer price 7888
Three people form a group 7288
Registration link: https://live.freebuf.com/detail/b6fb228de219f6abab0082ddaa0df244
Course details can be consulted by teaching assistants
And receive a trial class, note: Luna Course
· FreeBuf Knowledge Continent APP ·
Apple users can download from the App Store
Android users can download it from all major app stores
If you have any questions, please contact Vivi WeChat:
Erfubreef121






GIPHY App Key not set. Please check settings