The four departments jointly issued the “Internet Government Application Security Management Regulations”, which will be implemented on July 1; more than 60% of network security equipment's own flaws can be exploited as zero-day vulnerabilities | Niu Lan
Date: May 23, 2024
Views: 57
News
dot Four departments jointly issued the “Internet Government Application Security Management Regulations”, which will come into effect on July 1
dotShaanxi police crack down on 5 typical cases of online violence and crimes
dotYouTube becomes new hotbed for cybercrime
dot70% of CISOs believe they will suffer a cyberattack within 12 months
dotBlackbasta claims to have stolen 730G data from the largest U.S. fuel distribution group
dotMore than 60% of network security equipment flaws can be exploited as zero-day vulnerabilities
dotSolarMarker malware evolves through multi-layered infrastructure to evade security detection
dotZscaler to add new capabilities to AI data protection platform
dotZoom video conferencing system enables post-quantum end-to-end encryption protection
dotGitLab is about to release Duo enterprise version AI plug-in
dotAsiaInfo Security announced that it will fully integrate into the Hongmeng ecosystem
Special attention
The four departments jointly issued the “Internet Government Application Security Management Regulations”, which will come into effect on July 1
Recently, the Office of the Central Cyberspace Security and Informatization Commission, the Office of the Central Organization and Establishment Commission, the Ministry of Industry and Information Technology, and the Ministry of Public Security jointly formulated and issued the “Internet Government Application Security Management Regulations”. Party and government agencies and public institutions at all levels (hereinafter referred to as agencies and public institutions) should strictly abide by the requirements of these regulations when building and operating Internet government applications to ensure the safe and stable operation of Internet government applications and data security.
The following is the specific content of the regulations:
Internet Government Application Security Management Regulations
(Developed on February 19, 2024 by the Office of the Central Cybersecurity and Information Technology Commission, the Office of the Central Institutional Establishment Committee, the Ministry of Industry and Information Technology, and the Ministry of Public Security and released on May 15, 2024)
Chapter I General Provisions
Article 1 In order to ensure the security of Internet government applications, this document is formulated in accordance with the “Cybersecurity Law of the People's Republic of China”, “Data Security Law of the People's Republic of China”, “Personal Information Protection Law of the People's Republic of China”, “Implementation Measures of the Party Committee (Party Group) Network Security Work Responsibility System”, etc. Regulation.
Article 2 Party and government agencies and public institutions at all levels (referred to as agencies and public institutions) must abide by these regulations when building and operating Internet government applications.
The Internet government affairs applications referred to in these regulations refer to portal websites established by government agencies and institutions on the Internet, mobile applications (including mini-programs) that provide public services through the Internet, public accounts, and Internet email systems.
Article 3 The construction and operation of Internet government affairs applications shall comply with the provisions of relevant laws, administrative regulations and the mandatory requirements of national standards, implement the principle of “synchronous planning, simultaneous construction, and simultaneous use” of network security and Internet government affairs applications, and adopt technical measures and other necessary measures to prevent Content tampering, attack paralysis, data theft and other risks ensure the safe and stable operation of Internet government applications and data security.
Chapter 2 Start-up and Construction
Article 4 Government agencies and public institutions should complete the review and filing of websites in accordance with procedures. A party and government agency can only open one portal website.
The central organization establishment management departments, the State Council’s telecommunications departments, and the State Council’s public security departments will strengthen data sharing, optimize work processes, reduce the amount of reporting materials, and shorten the start-up cycle.
When government agencies and public institutions set up websites, they should include funds for operation, maintenance and security in their budgets.
The fifth In principle, a party and government agency website can only register one Chinese domain name and one English domain name. The domain name should be suffixed with “.gov.cn” or “.governmental affairs”. Websites of non-party and government agencies are not allowed to register and use the domain name “.gov.cn” or “.governmental affairs”.
The domain name of the website of a public institution should be suffixed with “.cn” or “.philanthropy”.
Government agencies and institutions shall not transfer registered website domain names to other units or individuals for use without authorization.
Article 6 Mobile applications of government agencies and public institutions should be distributed on registered application distribution platforms or government agency and public institution websites.
Article 7 The organization establishment management department shall issue exclusive electronic certificates or paper certificates for government agencies and public institutions. When government agencies and public institutions distribute mobile applications through application distribution platforms, they shall provide electronic certificates or paper certificates to the platform operators for identity verification; when opening public accounts such as Weibo, public accounts, video accounts, and live broadcast accounts, they shall provide electronic certificates or paper certificates to the platform operators for identity verification.
eighth The name of Internet government affairs applications shall preferably use the name of the entity organization and the standard abbreviation. If other names are used, in principle, the naming method of regional name plus responsibility name shall be adopted, and the name of the entity organization shall be marked in a prominent position. Specific naming standards are formulated by the central agency establishment management department.
Article 9 The central agency establishment management department sets exclusive online logos for government agencies and public institutions, and non-government and public institutions are not allowed to use them.
The websites of government agencies and institutions shall add an online logo in the middle position at the bottom of the homepage. The Office of the Central Cybersecurity and Information Technology Commission, in conjunction with the central agency establishment management department, coordinates the application distribution platform and the public account information service platform, and adds online logos in prominent positions on mobile application download pages and public accounts.
Article 10 All regions and departments should make overall plans for the construction of websites of party and government organs in their regions and departments and promote intensive construction.
In principle, the various departments of the county-level party and government organs and the township party and government organs do not build their own websites. They can use the website platform of the higher-level party and government organs to set up web pages, columns, and publish information.
Article 11 Internet government affairs applications should support open standards, fully consider compatibility with user terminals, and should not require users to use specific browsers, office software, or other user terminal hardware and software systems to access them.
Government agencies and public institutions providing public services through the Internet must not be bound to a single Internet platform, and users must not download, install, or register to use a specific Internet platform as a prerequisite for obtaining services.
Article 12 If an Internet government application needs to change its operating entity due to organizational adjustments, the domain name or registration filing information should be changed in a timely manner. If it is no longer used, the service should be closed in a timely manner, data archiving and deletion should be completed, and the domain name and registration filing information should be cancelled.
Chapter 3 Information Security
Article 13 Government agencies and public institutions that publish information through Internet government affairs applications should improve the information release review system, clarify review procedures, designate agencies and on-staff personnel to be responsible for review work, and establish review record files; they should ensure the authority, authenticity, and accuracy of the information released. , timeliness and seriousness, and it is strictly prohibited to publish illegal and harmful information.
Article 14 Government agencies and public institutions should reprint information through Internet government affairs applications related to government affairs and other activities to perform their functions, and evaluate the authenticity and objectivity of the content. The reprint page must be accurately and clearly marked with the reprint source website, reprint time, reprint link, etc., and fully consider intellectual property protection issues such as pictures and content.
Article 15 When government agencies and public institutions need to link to non-Internet government affairs applications when publishing information content, they should confirm that the linked resources are related to government affairs and other activities that perform their functions, or fall within the scope of public services; they should regularly check the validity and applicability of links and promptly handle abnormal links. Party and government portal websites should take technical measures to provide clear reminders when users click on links to jump to non-party and government website.
Article 16 Government agencies and public institutions should take security and confidentiality control measures, strictly prohibit the release of state secrets and work secrets, and prevent the risk of leaks caused by the aggregation and association of Internet government application data. The confidentiality management of the storage, processing, and transmission of work secrets in Internet government applications should be strengthened.
Chapter 4 Network and Data Security
Article 17 The construction of Internet government applications should implement the network security level protection system and national cryptographic application management requirements, carry out classification filing and level assessment work in accordance with relevant standards and specifications, implement security construction rectification and reinforcement measures, and prevent network and data security risks.
The portals of central and state agencies, local party and government agencies at or above the prefecture level, as well as the websites of government agencies and public institutions that carry important business applications, Internet email systems, etc., should meet the requirements for the third level of network security protection.
Article 18 Government agencies and public institutions should conduct security testing and assessment of Internet government application networks and data security at least once a year, either on their own or by entrusting a third-party network security service agency with relevant qualifications.
Internet government application system upgrades, new features, and the introduction of new technologies and applications should be subject to security testing and assessment before going online.
Article 19 Internet government applications should set up access control policies. For functions and Internet email systems used by staff of government agencies and public institutions, access restrictions should be implemented on the IP address segments or devices connected to them. If overseas access is indeed required, access rights for specific time periods, specific devices or accounts should be opened in a whitelist manner.
Article 20 Government agencies and public institutions shall retain operation logs of firewalls, hosts and other equipment related to Internet government applications, as well as application system access logs and database operation logs for no less than one year, and regularly back up the logs to ensure the integrity of the logs. sex, usability.
Article 21 Government agencies and institutions should conduct classified and hierarchical management of Internet government application data in accordance with national and industry requirements for data security and personal information protection, and focus on protecting important data, personal information, and business secrets.
Article 22 Personal information, business secrets and other undisclosed information collected by government agencies and institutions through Internet government applications shall not be provided or disclosed to third parties without the consent of the information provider, and shall not be used for purposes other than performing legal duties.
Article 23 Data centers, cloud computing service platforms, etc. that provide services for Internet government applications should be located within the territory.
Article 24 When party and government agencies purchase cloud computing services for building Internet government affairs applications, they should select cloud platforms that have passed the national cloud computing service security assessment and strengthen the management of the use of purchased cloud computing services.
Article 25 When government agencies and public institutions entrust outsourcing units to develop and operate Internet government applications, they should clarify the network and data security responsibilities of the outsourcing units through contracts and other means, strengthen daily supervision and management, and assessment and accountability; and urge the outsourcing units to use, store, and process data strictly in accordance with the agreement. Without the consent of the entrusting government agencies and public institutions, outsourcing units shall not subcontract or sub-contract contract tasks, and shall not access, modify, disclose, use, transfer, or destroy data.
Government agencies and public institutions should establish a strict authorization access mechanism. The highest administrator authority of operating systems, databases, computer rooms, etc. must be managed by a dedicated staff member of the unit, and the management and use of the authority must not be entrusted to outsourced personnel without authorization. The authorization of outsourced personnel should be refined in accordance with the principle of minimum necessity, and the authority should be promptly revoked after the expiration of the authorization period.
Article 26 Government agencies and public institutions should reasonably build or use social professional disaster recovery facilities to carry out disaster recovery backup of important data and information systems of Internet government applications.
Number twenty sevenstrip Government agencies and public institutions should strengthen the security management of Internet government application development, and the use of external codes should be subject to security testing. Establish a business continuity plan to prevent risks brought about by changes in supplier services, such as upgrades, renovations, and operation and maintenance guarantees.
Article 28 If Internet government applications use content distribution network (CDN) services, they should require service providers to point the domain name resolution addresses of domestic users to their domestic nodes, and not to overseas nodes.
Article 29 Internet government applications should be accessed using a secure connection, and the electronic certification services involved should be provided by e-government electronic certification service agencies established in accordance with the law.
Article 30 Internet government applications should authenticate the real identity information of registered users. The state encourages Internet government applications to support users to use the national network identity authentication public service to register real identity information.
For Internet government applications and email systems related to personal and property safety, social and public interests, etc., multi-factor authentication should be adopted to improve security, and technical means such as timeout exit, limiting the number of failed logins, and binding accounts to terminals should be adopted to prevent account theft. risks, the use of identity authentication measures such as electronic certificates is encouraged.
Chapter 5 Email Security
Article 31 Encourage all regions and departments to build dedicated Internet e-mail systems for government agencies and institutions through a unified construction and shared use model as work mailboxes to provide e-mail services for agencies and institutions in the region and industry. The domain names of Internet e-mail systems self-built by party and government agencies should be suffixed with “.gov.cn” or “.governmental affairs”, and the domain names of Internet e-mail systems self-built by public institutions should be suffixed with “.cn” or “.public welfare” as suffix.
Staff members of government agencies and institutions are not allowed to use work email addresses to store, process, transmit, or forward state secrets in violation of regulations.
No.Article 32 Government agencies and public institutions should establish processes for the application, issuance, change, and cancellation of work email accounts, strictly review and register accounts, and conduct regular account cleanups.
Article 33 Internet email systems of government agencies and institutions should turn off the automatic forwarding of emails and automatic downloading of attachments.
Article 34 The Internet email system of government agencies and public institutions shall have the function of detecting and intercepting malicious emails (including emails sent internally by the institution), and detect and intercept malicious email accounts, malicious email server IPs, and malicious email subjects, texts, links, attachments, etc. It shall support the sharing of phishing email threat intelligence, report the discovered phishing email information to the competent department and the local cybersecurity and informatization department, and configure the corresponding protection strategy to preset the interception of phishing emails according to the phishing email threat intelligence issued by the relevant departments.
Thirty-fifthstrip Government agencies and institutions are encouraged to securely protect the storage of email data based on commercial cryptography technology.
Chapter Six Monitoring, Early Warning and Emergency Response
Article 36 The Office of the Central Cybersecurity and Information Technology Commission, in conjunction with the State Council’s telecommunications department, the public security department and other relevant departments, organizes security monitoring of Internet government applications of party and government agencies at the prefectural and municipal levels and above.
All regions and departments should carry out daily monitoring and security inspections of the Internet government applications of agencies and institutions in their respective regions and industries.
Government agencies and public institutions should establish and improve Internet government affairs application security monitoring capabilities, and monitor the operating status of Internet government affairs applications and network security incidents in real time.
Article 37 When network security incidents occur in Internet government applications, government agencies and institutions should report to relevant departments in accordance with relevant regulations.
Article 38 The Office of the Central Cyberspace Affairs Commission coordinates emergency response to major cybersecurity incidents.
When a network security incident occurs or is likely to occur in an Internet government application, government agencies and public institutions should immediately activate their own network security emergency plans, promptly handle network security incidents, eliminate security risks, and prevent the harm from expanding.
Article 39 The institutional establishment management department, together with the cybersecurity and informatization department, conducts scanning and monitoring of counterfeit Internet government applications and accepts relevant complaints and reports. The cybersecurity and informatization department, in conjunction with the telecommunications authorities, promptly takes measures such as stopping domain name resolution, blocking Internet connections, and taking offline processing of counterfeit and counterfeit Internet government applications discovered through monitoring or reported by netizens. The public security department is responsible for cracking down on illegal and criminal activities related to counterfeit and counterfeit Internet government applications.
Chapter VII Supervision and Management
Article 40 The Office of the Central Cyberspace Affairs Commission is responsible for coordinating the security management of Internet government applications. The central organization establishment management department is responsible for the identity verification, name management and logo management of Internet government applications. The State Council's telecommunications department is responsible for the supervision and management of Internet government application domain names and Internet information service (ICP) filing. The State Council's public security department is responsible for supervising, inspecting and guiding the Internet government application network security level protection and related security management work.
All regions and departments shall assume the responsibility for the security management of Internet government affairs applications in government agencies and institutions in their regions and industries, designate a person in charge to be in charge of related work, and strengthen the organizational leadership of Internet government affairs application security work.
Article 41 Those who violate or fail to properly perform the relevant requirements of these regulations will be held accountable in accordance with the “Implementation Measures for the Party Committee (Party Group) Network Security Work Responsibility System” and other documents, in accordance with regulations and disciplines.
Chapter 8 Supplementary Provisions
Article 42 The security management of Internet portals, mobile applications, public accounts, and email systems included in critical information infrastructure shall be implemented with reference to the relevant contents of these regulations.
Article 43 The Office of the Central Cyberspace Affairs Commission, the Office of the Central Organization and Establishment Commission, the Ministry of Industry and Information Technology, and the Ministry of Public Security are responsible for interpreting these regulations.
Article 44 These regulations will come into effect on July 1, 2024.
Original link:
https://www.cac.gov.cn/2024-05/22/c_1718054910848581.htm
Shaanxi police crack down on 5 typical cases of online violence and crimes
In response to illegal and criminal acts of online violence such as spreading rumors, defamation, insults, and invasion of privacy, the Shaanxi Public Security Network Security Department recently cracked down on and dealt with five typical cases of online violence in accordance with the law.
1. Wang Moumou’s case of insult and defamation
Because of a dispute with Li from the same village, Wang Moumou sent a large number of abusive messages to the victim through a WeChat group chat. There were more than 300 WeChat users in the group. Seriously interfere with the normal life of the victim and cause negative social impact. Currently, the police in Xi'an, Shaanxi Province impose a 15-day administrative detention penalty on Wang Moumou in accordance with the law.
2. Case of Wang insulting others
Today, in order to vent his personal anger over trivial matters, Wang randomly insulted Cao in a WeChat group of more than 400 people, causing a bad social impact and seriously affecting Cao's normal life. Currently, the police in Xianyang, Shaanxi Province impose administrative penalties on Wang in accordance with the law.
3. Case of Wu Mou insulting others
Wu posted a video insulting Wang on a certain online platform due to emotional and financial disputes, which seriously affected Wang's normal work and life. At present, the Tongchuan police in Shaanxi Province have imposed administrative penalties on Wu in accordance with the law.
4. Case of Yang fabricating insulting information to violently abuse others online
Yang was dissatisfied with his girlfriend breaking up with him, so he fabricated facts on WeChat groups many times, posted private videos of his ex-girlfriend, and insulted and attacked her, which attracted the attention of netizens and had a bad influence, greatly affecting his ex-girlfriend's work and life. At present, the Hanzhong police in Shaanxi Province has punished Yang with 10 days of administrative detention in accordance with the law.
5. Case of Wang Moumou leaking other people’s privacy
Wang and Li had a dispute over shearing sheep. To vent his anger, Wang posted Li's personal information, home address and other private information on the Internet platform, which had a negative social impact on Li. Currently, the Yulin police in Shaanxi Province have imposed administrative penalties on Wang in accordance with the law.
Original link:
https://mp.weixin.qq.com/s/sZSRAyzc_kE9rnoNxpvFcQ
Hot spots to watch
YouTube becomes a new hotbed for cybercrime

According to a new report from security firm Avast, YouTube has become a new “hotbed” for malicious actors to deploy various criminal activities such as phishing, malware, and fake investment schemes. The company specifically mentioned two malware strains, Lumma and RedLine, which are operating on a large scale on YouTube.
Avast pointed out that YouTube acts as a traffic distribution channel, directing users to various malicious websites and pages, which promotes cybercrime of varying severity. Attackers use YouTube's huge influence to trick users into visiting deceptive websites and downloading malware. In addition, the increasing number of deep fake videos on YouTube has become a major problem. These fake videos mislead viewers and spread false information by imitating real people or events. Avast found that multiple accounts with more than 50 million subscribers have been hacked and used to spread cryptocurrency scams that rely on deep fake videos.
Original link:
70% of CISOs believe they will suffer a cyberattack within 12 months
According to the latest “Data Breach Environment” report released by Proofpoint, 70% of chief information security officers (CISOs) are worried that their companies will suffer cyber attacks in the next 12 months, and this proportion has increased compared with previous years. The report points out that remote and hybrid working models have expanded the attack surface of enterprises, coupled with record high employee turnover rates and the popularity of generative AI and off-the-shelf hacking tools, making enterprise network security management more complex.
The survey found that while 70% of CISOs believe their organizations are at risk of cyberattacks in the next 12 months, only 43% feel unprepared for targeted attacks, a significant decrease from previously, indicating that CISOs are Corporate defenses are becoming increasingly assertive. However, human error is still the cybersecurity risk that CISOs are most concerned about, with 74% of CISOs viewing it as the biggest cybersecurity vulnerability. In addition, 80% of respondents expect human risks and employee negligence to become major cybersecurity issues in the next two years, highlighting the disconnect between employee security awareness and actual response effects. In addition, the report also found that more than half of the CISOs surveyed said they had experienced or witnessed professional burnout in the past year, and 66% believed that expectations for them were too high, which may also affect their ability to deal with cybersecurity challenges. .
Original link:
https://www.infosecurity-magazine.com/news/70-cisos-expect-cyberattacks-next/
Network attacks
Blackbasta claims to have stolen 730GB of data from the largest fuel distribution group in the United States
Recently, the ransomware group Blackbasta claimed to have hacked into Atlas, one of the largest national fuel distributors in the United States, and added it to the list of victims on the group's Tor leak website, indicating that they had successfully infiltrated the company's network.
The group claimed to have stolen 730GB of data from Atlas, including company accounts, human resources, finance, executives, and user and employee personal information. As evidence of the attack, they released a series of documents such as employee ID cards, data sheets, and payroll payment requests. Although Atlas has not yet disclosed the incident, the intrusion has undoubtedly dealt a serious blow to the energy company.

Blackbasta is an active ransomware group that has been carrying out double extortion attacks since April 2022. Cybereason experts have observed that in the ongoing QakBot malware attack against the United States, QakBot infection eventually led to the deployment of Blackbasta ransomware. This attack chain starts with spam/phishing, and once access is gained, the attackers act extremely fast, sometimes gaining domain administrator privileges in less than 2 hours and completing the deployment of ransomware within 12 hours. This rapid attack speed makes it difficult for enterprises to detect and respond in time.
Original link:
More than 60% of network security equipment flaws can be exploited as zero-day vulnerabilities
According to a new report from Rapid7, more than 60% of network and security device flaws discovered in 2023 can be exploited as zero-day vulnerabilities, reflecting that attackers are becoming increasingly adept at exploiting system security flaws before patches are released.
Since 2023, the attack methods of many large-scale intrusions have changed significantly. Nearly a quarter (23%) of widespread, threatening public vulnerabilities and exposures (CVEs) result from highly coordinated zero-day attacks, with a single attacker able to impact hundreds of organizations. This “single attacker, multiple targets” model replaces the previously common “multiple attackers, multiple targets” model.
Researchers noted that starting in 2023, more than one-third (36%) of widely exploited vulnerabilities originated from network perimeter technologies, almost double the number from the previous year. Most widely exploited CVEs originate from easily exploitable root causes, such as command injection and improper authentication issues, and away from memory corruption exploits. Additionally, 41% of incidents in 2023 were caused by multi-factor authentication (MFA) not being enabled or enforced.
Original link:
https://www.infosecurity-magazine.com/news/network-security-flaws-exploited/
SolarMarker malware evades security detection through multi-layered infrastructure evolution
Recorded Future, a security company that has long been monitoring the SolarMarker information-stealing malware, pointed out in its latest report that the threat actors behind the malware have established a multi-layered infrastructure to increase the difficulty of detection and investigation by law enforcement agencies. The core of the malware is its layered C2 server architecture, which includes at least two clusters: a primary cluster for active operations and a secondary cluster that may be used to test new strategies or attacks against specific regions and industries. This layered design not only enhances the malware's ability to adapt and respond to countermeasures, but also greatly increases the difficulty of its eradication.
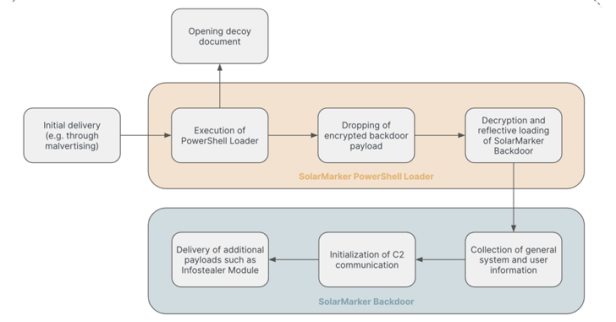
SolarMarker has continued to evolve since it first appeared in September 2020 and has grown into a fairly sophisticated threat. Not only does it have the ability to steal data from multiple web browsers and cryptocurrency wallets, it can also target VPN and RDP configurations. Although the initial infection vector is usually malware hosted on fake download sites or spread via malicious emails, malware authors continue to improve it by increasing payload size, using valid Authenticode certificates, Windows New changes to the registry, and running directly from memory instead of disk.
Original link:
https://thehackernews.com/2024/05/solarmarker-malware-evolves-to-resist.html
Industry trends
Zscaler will add new features to AI data protection platform
According to SiliconAngle, recently, cloud security company Zscaler announced the addition of new AI capabilities to its AI data protection platform, designed to improve data security and simplify management across diverse environments. These innovations are designed to help users protect intellectual property and customer data from a variety of threats and risks, including malicious insiders, accidental data loss, ransomware, and the growing popularity of cloud services. One of the key new features is natively integrated data security posture management for discovering, classifying and protecting sensitive data on platforms such as AWS and Azure. The GenAI App Security feature detects risky AI application usage and provides fine-grained policy control. In addition, Zscaler has launched email data loss protection to help companies deal with internal threats.
Original link:
https://www.scmagazine.com/brief/ai-features-added-to-zscalers-ai-data-protection-platform
Zoom video conferencing system enables post-quantum end-to-end encryption protection

Recently, Zoom announced a major security upgrade for its video communication platform, a new post-quantum end-to-end encryption (E2EE) feature that makes it impossible for advanced quantum computers to decipher all data transmitted between its servers and clients.The company has added this new feature to Zoom meetings and plans to expand it to Zoom phones and Zoom rooms in the near future
The move addresses Zoom’s early criticism for its lack of end-to-end encryption. Zoom, which has seen tremendous success during the COVID-19 pandemic and has become the dominant platform for remote work and online learning, had previously been subject to questions about its security until the company added E2EE functionality to Zoom meetings in 2020. Now, by introducing the latest quantum-safe cryptography, Zoom is further improving the security of its platform, giving users the confidence to continue using the software without compromising security. This is consistent with the proactive approach recently taken by other communications platforms such as Signal, Apple iMessage, Tuta Mail, and Google Chrome, which have all adopted the same NIST-recommended Kyber key encapsulation algorithm.
Original link:
GitLab is about to release Duo enterprise version AI plug-in

According to DevOps, GitLab plans to launch an enterprise-level AI plug-in version of its continuous integration/continuous delivery platform, called “Duo Enterprise Edition”. This new version will have some new features, including detecting and resolving security vulnerabilities, summarizing problem discussions and merge requests, eliminating bottlenecks in workflows, and improving team collaboration. It will also enhance existing code suggestions and privacy controls. In addition, Duo Enterprise Edition will also be equipped with a value stream prediction dashboard and support self-hosted model deployment in a secure environment.
Meanwhile, GitLab is preparing an update for GitLab 17, which introduces observability tools, project planning capabilities, a local secrets manager, and integration with static application security testing tools. What’s more noteworthy is that this update will also include a registry of data scientists, allowing them to develop AI models on the same platform as engineers. This cross-functional collaboration helps further enhance the visibility and automation of the software development process, thereby improving overall R&D efficiency.
Original link:
https://www.scmagazine.com/brief/gitlab-duo-enterprises-set-to-be-released
AsiaInfo Security announces that it will fully integrate into the Hongmeng ecosystem
On May 18, 2024, the signing ceremony for the cooperation between AsiaInfo and Huawei Terminal was held at the C3 Security Conference. AsiaInfo CEO Ma Hongjun and Huawei Terminal Cloud Developer Services and Platform President Wang Yue jointly signed the contract.

As a domestically developed operating system, Hongmeng system has achieved remarkable development results in recent years, and its open and intelligent features have been widely recognized by the industry. AsiaInfo Security has always had deep technical strength and rich industry experience in the field of terminal security. This time, AsiaInfo Security has deeply invested in the construction of Hongmeng ecosystem and combined with industry-leading terminal security capabilities to provide users with a more secure and reliable terminal environment and protect user information. Safety. The two parties will jointly explore new opportunities in the field of smart ecology and bring users a more convenient, smart and secure experience.
Original link:




GIPHY App Key not set. Please check settings