introduce
Currently 281 vulnerabilities are integrated, including nday, 1day (undisclosed POC)
java环境
java version “1.8.0_121”
Java(TM) SE Runtime Environment (build 1.8.0_121-b13)
Java HotSpot(TM) 64-Bit Server VM (build 25.121-b13, mixed mode)
Based on Apt-T00ls secondary development tool, I Wanna Get All security tool, all unauthorized vulnerability scanning attacks are strictly prohibited
When using tools or forwarding articles for other purposes, please note the author and source of the tool address.
It is recommended to determine the system fingerprint framework before using the tool. Some vulnerabilities are interface detection survival judgments. The actual utilization is subject to the execution situation.
Many false positives need to be improved. Welcome to raise issues.
renew
Updated functions: dnslog configuration, Jeecg token configuration
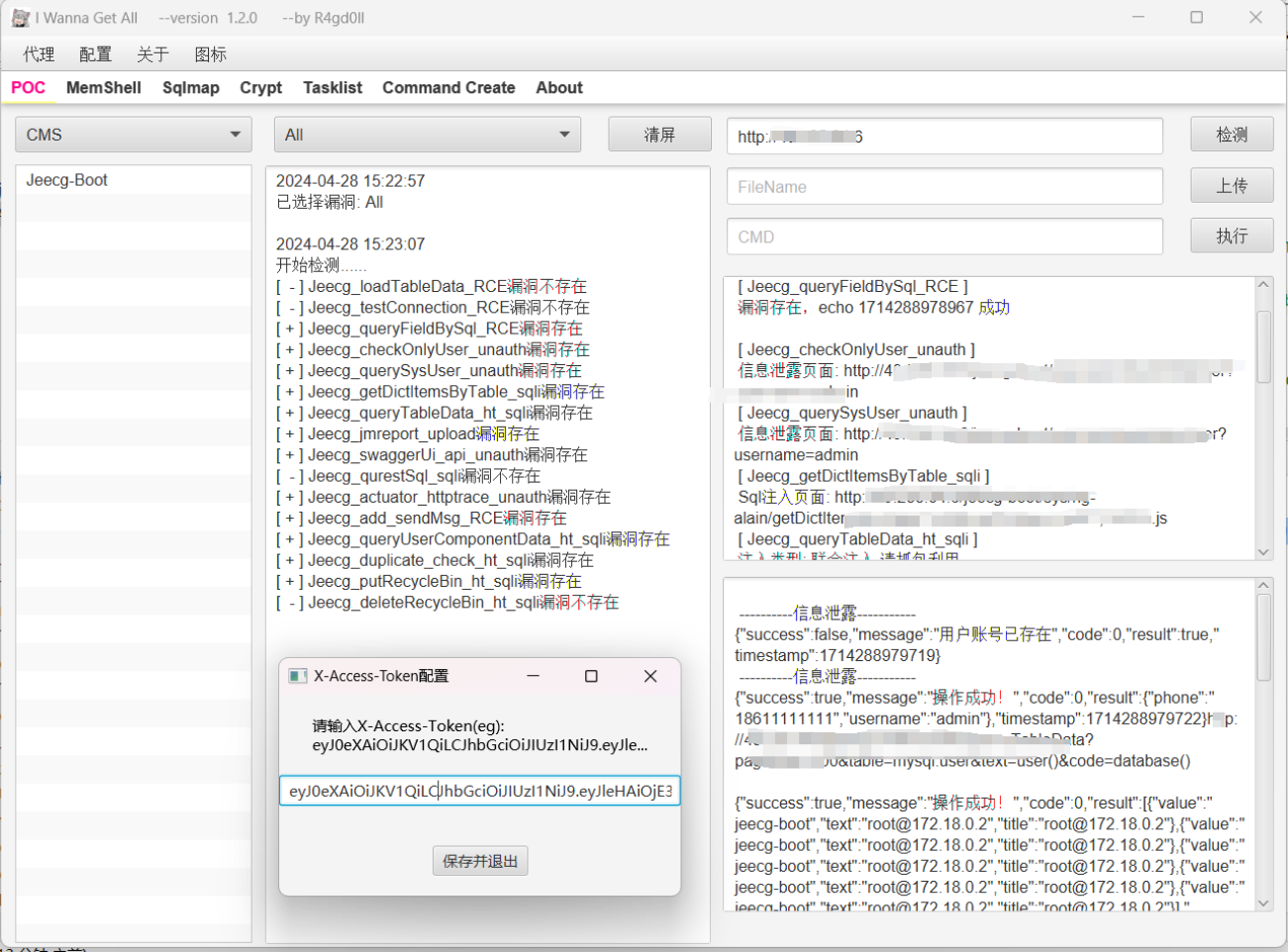
Updated Jeecg-Boot module with 16 built-in vulnerabilities
ATT Module
1. 用友serial漏洞大部分为接口探测,请ATT根据实际情况进行判断
2. 部分漏洞为确保准确性,请先进行检测,再进行点击执行利用
3. 使用ALL进行漏洞探测时,由于多线程等其他原因会产生误报
4. 文件上传漏洞,上传文件后执行进行上传,并使CMD栏为空,请先检测尝试上传后再利用
5. 命令执行漏洞利用CMD写入命令后进行执行。
6. 清屏按钮可清除除URL地址外所有信息
7. 根据执行结果提示并选择其他模块利用
8. POC模块目前集成poc情况共近230余个,包含至今HVV、goby纰漏漏洞(因poc集中管理可能出现误报,请配置代理抓包判断),如下:
(1).用友NC&反序列化接口----------------------------------fofa:title="YONYOU NC"
(2).用友GRP--------------------------------------------fofa:app="yonyou-GRP-U8"
(3).用友NCCloud----------------------------------------fofa:body="nccloud"
(4).用友tplus------------------------------------------fofa:app="畅捷通-TPlus"
(5).用友U8C--------------------------------------------fofa:app="用友-U8-Cloud"
(6).用友ufida------------------------------------------fofa:body="ufida.ico"
(7).泛微Ecology----------------------------------------fofa:app="泛微-协同办公OA"
(8).泛微Emobile----------------------------------------fofa:title="移动管理平台-企业管理"
(9).泛微Eoffice----------------------------------------fofa:app="泛微-EOffice"
(10).蓝凌OA--------------------------------------------fofa:app="Landray-OA系统"
(11).蓝凌EIS-------------------------------------------fofa:app="Landray-EIS智慧协同平台"
(12).万户OA--------------------------------------------fofa:body="/defaultroot/"
(13).致远A6A8------------------------------------------fofa:app="致远互联-OA"
(14).致远MServer---------------------------------------fofa:body="/mobile_portal/"
(15).致远yyoa------------------------------------------fofa:body="yyoa" && app="致远互联-OA"
(16).通达OA--------------------------------------------fofa:app="TDXK-通达OA"
(17).帆软组件-------------------------------------------fofa:"Powered by 帆软"
(18).金蝶Apusic----------------------------------------fofa:header="Apusic"
(19).金蝶EAS-------------------------------------------fofa:app="Kingdee-EAS"
(20).金蝶云OA------------------------------------------fofa:app="金蝶云星空-管理中心"
(21).金和OA--------------------------------------------fofa:app="金和网络-金和OA"
(22).红帆OA--------------------------------------------fofa:app="红帆-ioffice"
(23).宏景HCM--------------------------------------------fofa:app="HJSOFT-HCM"
(24).亿赛通---------------------------------------------fofa:app="亿赛通-电子文档安全管理系统"
(23).飞企互联-------------------------------------------fofa:app="FE-协作平台"
Example 1:
UFIDA NC Vulnerability Detection (Select OA type — Select vulnerability — Enter URL — Detection)
UFIDA NC vulnerability exploit (select OA type — select vulnerability — enter URL — enter command — execute)
UFIDA NC file upload (select OA type — select vulnerability — enter URL — upload file — execute)
MemShell Module
1. 支持冰蝎3.0、哥斯拉、蚁剑、suo5、cmdecho、neoReGeorg、自定义内存马
2. 支持输出源码、Base64、hex、gzip格式payload
3. 用友NC反序列化 集成接口反序列化(测试环境)
4. 用友U8C反序列化 集接口反序列化(测试环境)
5. 亿赛通XStream反序列化 集接口反序列化(测试环境)
6. 用友NC内存马支持bypass脏数据传入,默认为100字节
Example 2:
(*ActionHandlerSevlet and other interfaces are injected using CC6NC chain)
UFIDA NC Ice Scorpion Memory Horse
UF NC Godzilla Memory Horse Injection
UFIDA NC cmdEcho memory horse injection
UFIDA NC custom memory horse injection (using Ant Sword ClassByte bytecode), enter the class name, Base64 encoded bytecode, dirty data (optional)
The remaining functions are all available and will not be demonstrated.
Example 3:
U8Cloud Ice Scorpion memory horse injection (other memory horses can be injected)
U8Cloud cmdEcho memory horse injection
Example 4:
Ice Scorpion Memory Horse Payload Source Code, Base64 Payload, etc. Generated Display (UFIDA NC Example)
Sqlmap module
Enter the content according to the prompts and execute it, integrating the call to sqlmap
Example 5:
Fanwei CheckServer-Sql injection, after detecting the vulnerability, save the content under the payload field as a req file, and use the sqlmap module to construct parameters
Crypt Module
1. 各类OA加解密
2. 各类编码解码
3. Class类反编译、class字节码生成(base64格式、gzip-base64格式)
4. class反编译仅文件读取、base64格式(yv66)、gzip-base64格式(H4sI)可反编译
Example 6
UFIDA NC database password encryption and decryption
Example 7
classbyte bytecode decoding (class file import and decoding, base64 bytecode encoding and decoding)
Common encryption and decoding methods for malicious types: Base64-Gzip, Hex-Gzip, etc.
TaskList Module
Keep the original function of Apt-T00ls: antivirus software identification
Example 8
Command Create Module
Keep the original functions of Apt-T00ls: common command creation
Example 9
other
Some sql injection vulnerability tamper scripts are placed in the tamper path
Disclaimer
This tool is only for legally authorized enterprise security construction activities. If you need to test the usability of this tool, please build the target machine environment yourself.
When using this tool for detection, you should ensure that the behavior complies with local laws and regulations and that you have obtained sufficient authorization. Do not scan unauthorized targets.
If you engage in any illegal behavior while using this tool, you must bear the corresponding consequences yourself, and I will not bear any legal and joint liability.
Before installing and using this tool, please read carefully and fully understand the terms and conditions. Restrictions, disclaimers or other terms involving your major rights and interests may be highlighted in bold or underlined to remind you to pay special attention. Unless you have fully read, understood and accepted all the terms of this Agreement, please do not install and use this tool. Your use of this tool or any other explicit or implicit expression of your acceptance of this Agreement shall be deemed as your reading and agreement to the constraints of this Agreement.





























GIPHY App Key not set. Please check settings