
Introduction: The official fix plan has been released, and affected users are advised to update to a safe version.
Vulnerability overview
|
Vulnerability type |
Remote command execution |
|
Vulnerability level |
serious |
|
Vulnerability number |
CVE-2024-3400 |
|
Vulnerability score |
10 |
|
Exploiting complexity |
Low |
|
Affected version |
PAN-OS 11.1.* < 11.1.2-h3 PAN-OS 11.0.* < 11.0.4-h1 PAN-OS 10.2.* < 10.2.9-h1 |
|
Utilization method |
Remotely |
|
POC/EXP |
Undisclosed |
Palo Alto Networks' PAN-OS is an operating system that runs on Palo Alto Networks firewalls and enterprise VPN devices. A command injection vulnerability exists in the GlobalProtect function of Palo Alto Networks PAN-OS software. Targeting specific PAN-OS versions and different functional configurations, it may allow an unauthenticated attacker to execute arbitrary code with root privileges on the firewall. On April 10, 2024, Volexity discovered that one of its Network Security Monitoring (NSM) customers had implemented a zero-day exploit of a vulnerability discovered in the Palo Alto Networks PAN-OS GlobalProtect feature that allowed the attacker to create a reverse shell, download tools, steal Configure data and move it laterally within the network. The Palo Alto Networks PSIRT team identified the vulnerability as an operating system command injection issue and assigned it CVE-2024-3400.
Applies only to PAN-OS 10.2, PAN-OS 11.0 and PAN-OS 11.1 firewalls with GlobalProtect gateway (Network > GlobalProtect > Gateways) and device telemetry (Device > Setup > Telemetry) enabled.
Asset mapping
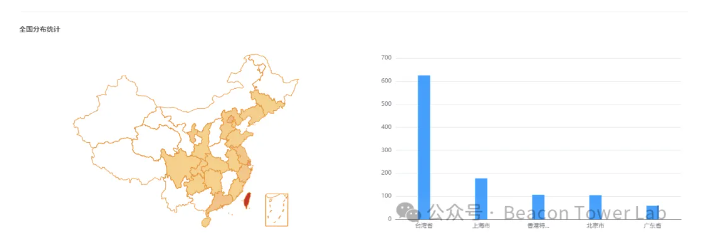
According to data from www.daydaymap.com, the distribution of domestic risk assets in the past six months is as follows, mainly in Taiwan Province.
solution
An official fix has been released, and affected users are advised to update to a safe version.
https://support.paloaltonetworks.com/support
If reprinted, please indicate the original address.


Thank you for your support, I will continue to work hard!
OpenWeChatScan and click on the upper right corner to share.
You may be interested
-

Vulnerability Warning丨Palo Alto Networks PAN-OS command injection vulnerability (CVE-2024-3400)
-

Stealth GTPDOOR Linux malware targets mobile operator networks
-

Incinerator – the ultimate tool for reverse engineering Android malware
-

StopCrypt: The most widely distributed ransomware evolves to evade detection
-

Analysis of recent attack activities of “Youshe” black product
-

Vulnerability warning丨XZ Utilѕ tool library malicious backdoor implantation vulnerability (CVE-2024-3094)[includes self-check method]











GIPHY App Key not set. Please check settings