This week is going to be a short retro, unfortunately I was exposed to Covid on Tuesday and have been getting progressively sicker throughout the week, so I had a difficult time doing much of anything. I did, however, manage to deploy a privacy-conscious analytics platform to my blog this week, which is covered in more detail below.
3 Years a Security Engineer
If my job was a child, it would now know how to draw a circle and know not to touch a hot stove. It would also know how to use a fork and string items together. It’s definitely got those last two down, I feel like that’s my whole job.
Today marks my 3 year anniversary at my current job, which also means that I recently passed the 3 year anniversary since switching from full time red team work to full time security engineering work. I’ve previously written on my thoughts around this transition back in 2021and it is probably due for a longer form update. Short of that, I wanted to capture a couple notes here.
In the three years I’ve been at my current company, we’ve gone through some wild market conditions. We were in a rapid growth stage around when I joined, and we’ve since had two layoffs in the past two years. My boss is the only person on my team who has been here longer than me, and there are only a few engineers left who were here before me. The product and design teams have seen complete turnover, as has a lot of the go to market side of the business.
It’s been interesting being in this position, especially compared to how it felt when Intel did layoffs while I was working there. Intel laid off something like ten thousand people in one sweep while I was there and I think barely anyone I knew was impacted. But in a much smaller startup, everyone impacted is someone I know.
At Intel, there were people who had been working there since before I was born. At my current job, 3 years is a milestone not seen by many. Not just because of the layoffs, but because in the world of startups, people seem to be more keen to move on to things that are more interesting to them, or are better opportunities for them.
In my time as a security engineer, I’ve also become quite proficient in performance engineering, observability and monitoring, optimizing CI/CD pipelines, optimizing developer experience, and python type annotations. Basically all of these fall outside the realm of traditional security engineering roles, but I see myself as an engineer with security expertise, rather than an engineer who just builds security things. I’ve taken on probably a dozen big hairy projects that everyone wanted done but nobody had time to do. If something’s the thing to do, you do it.
I’m looking forward to seeing what the coming years bring, as the company shifts its focus towards sustainable, profitable business.
Now with 100% more analytics
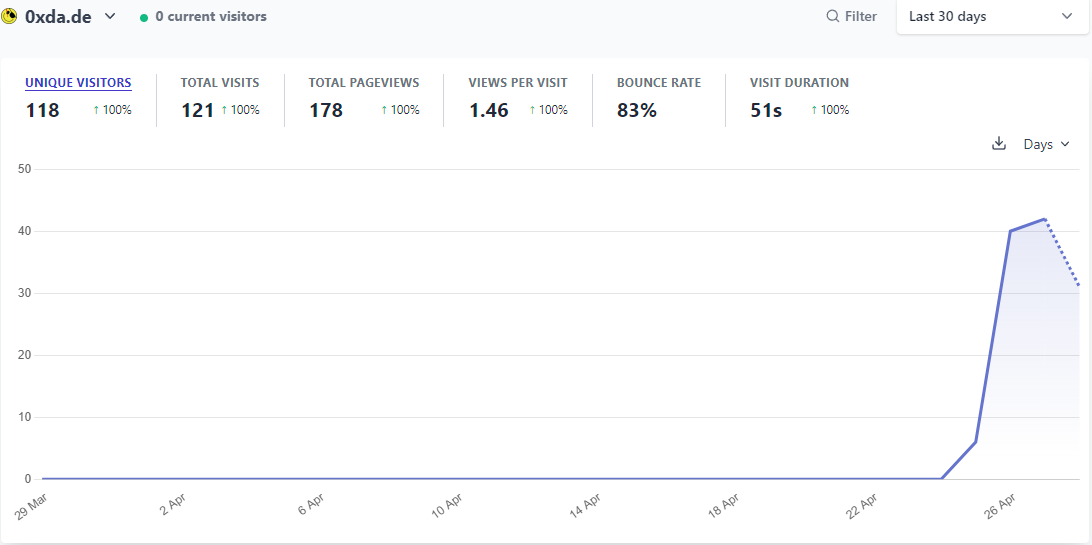
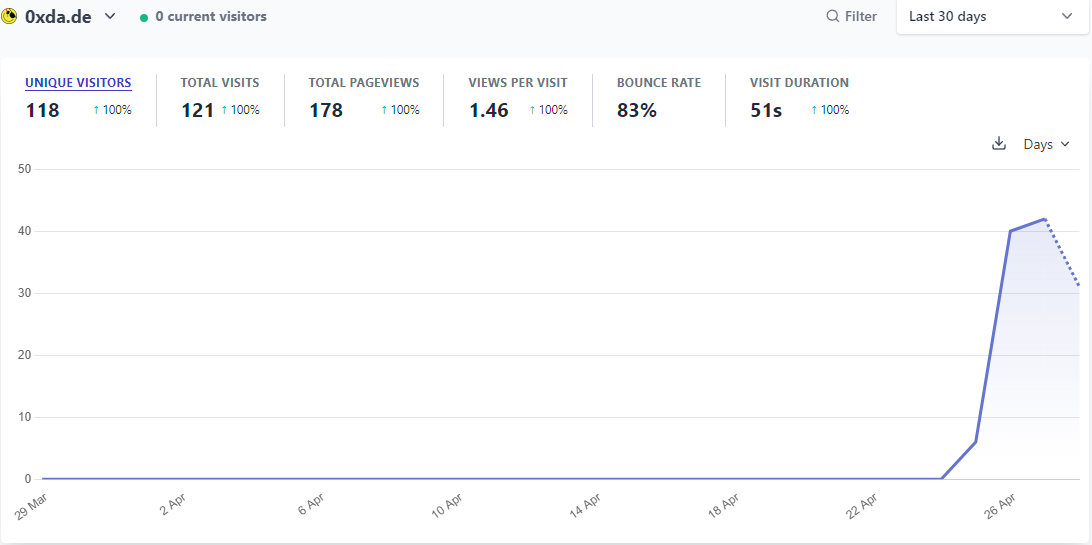
I have been on the fence about deploying analytics to my site. I don’t really feel like I need numerical feedback on my writing, and I didn’t want to introduce any sort of tracking or privacy-compromising javascript into my site. It’s a simple blog, it doesn’t need to know if you’re signed into Facebook or Google.
Ultimately I decided to deploy analytics because I wanted to understand where my readers are located and what people are mostly reading. I chose a self-hosted Plausible.io instance, and I made the dashboard available for public consumption via plausible.0xda.de/0xda.de in the interest of transparency. You can see what I can see.
It was easy to deploy via docker, but reminded me that it’s important to be aware that docker will hijack your firewall rules if they are defined and managed by ufw. I’ve typically resolved this by following the readme in ufw-docker. I don’t want my docker containers to ever accidentally expose a public service if I didn’t mean for it to be public.
I don’t currently have it setup, but I will also be adding a toggle to let people opt out of analytics without disabling javascript, following guidance provided by plausible. I want to get an idea of how my site is doing, but more importantly I want folks to be able to control their experience on my site.
I’ve also automatically excluded the javascript for plausible from my onion site. Both because if you’re using tor, you are probably making a choice to not be tracked, and because I have no idea how well Plausible would handle the unique visitor identification via Tor.
I was also curious approximately how many people were reading my posts from RSS readers and found this post by Darek Kay about estimating the number of RSS subscribers you have. From what I saw, I have 93 subscribers using Inoreader and 78 using Feedly. This is neat, I didn’t expect there to be so many.
What I’m Reading

The Bezzle
By Cory Doctorow
ISBN: 978-1-250-86587-8
Learn More
I’ve just passed the halfway point and I’ve been enjoying it a great deal. Cory always manages a good blend of fictional storytelling with real facts and history. I was somewhat surprised to see the story shift from a fast food fueled ponzi scheme towards the prison industrial complex, but overall it’s been interesting and I’ve learned quite a lot.
Interesting Links
- Nemesis 1.0 released – I’m not really super active in the world of offensive security anymore, but it’s always interesting to see what the folks at SpecterOps are up to, and this blog post talks about some really interesting engineering challenges in offensive platform engineering.
- miami analytics – A fork of umami that adds some nice improved features. I didn’t end up using this, but I like it as another privacy-focused Google Analytics alternative.
- So you want to scrape like the big boys – A post from 2021 that talks about approaches to scraping and avoiding bot detection, as well as highlights many techniques used to fingerprint browsers and detect bots.
- Pirate Radio Station Operators Facing $850,000 in Fines – I saw this on Twitter and after reading through it, I couldn’t help but wonder if pirate radio stations were a more common occurence than I realized. Were these people just doing it for the love of sharing their playlists? Or was there some financial incentive at play? Were they making money from these pirate stations?
- Passkeys: A Shattered Dream – I am still a big advocate of Webauthn based security keys, but I’ve never been sold on the passwordless future, and I’ve certainly never willingly called them marketing fluff like “Passkeys.” This post covers the steady decline in UX that has plagued Webauthn over the past few years, which I’ve also noticed first hand as we rolled out security keys to everyone at our company. The experience has changed a dozen times and now everyone is vying to be your passkey provider, to lock you in to their platform, to capture market share. Disgusting.
- github.com/:user.atom – This is an example link but something I found and thought was cool – you can subscribe to a user’s github activity as an atom feed. This joins github.com/:user.keys as a neat feature that may not be well known.
Upcoming Projects
- BSides Las Vegas Talk – Pending feedback on CFP submission. (Due: N/A – Done)
- OWASP Global AppSec Training – I’ve drafted out the outline for a 1-day hands-on training on Docker. It’s targeted at developers who may be familiar with what docker is but not familiar with using it themselves. (Due: 2024-05-06)
- Defcon 32 Call for Artists – I think I need to record a set list, or maybe put together a soundcloud playlist that I can share. I also need to pick a promo photo. (Due: 2024-06-01)
- Defcon 32 Call For Soundtrack – My new song, “Oh Dade”, produced by Michael Hillis pending mixing before submission. If it’s accepted, it will debut on the Defcon soundtrack. If it’s not accepted, I will release it the same day I find out it’s not accepted. (Due: 2024-06-01)




GIPHY App Key not set. Please check settings