
Introduction: iCrypto has been paying close attention to the dynamics of regulatory authorities for a long time. After studying this article, we summarized the overall structure of the document and extracted six key contents for your reference.

The Ministry of Industry and Information Technology issued a notice on April 7, requiring all relevant units to follow the deployment requirements of the three-year action to tackle the root causes of production safety, adhere to safety development, focus on prevention, and integrate technology and management, and combine the tasks of production safety and network operation safety. , measures, and responsibilities should be truly implemented, and the foundation of the information and communication network that guarantees the safety of people's lives and property and the stability of the overall social situation should be truly established. Efforts will be made to complete seven key tasks, including strengthening ideological and political guidance, improving institutional policy systems, enhancing safety prevention capabilities, strengthening rectification of key issues, keeping a close eye on key link scenarios, improving emergency response levels, and strict law enforcement supervision and assessment.
iCrypto has been paying close attention to the dynamics of regulatory authorities for a long time. After studying this article, we summarized the overall structure of the document and extracted six key contents for your reference.
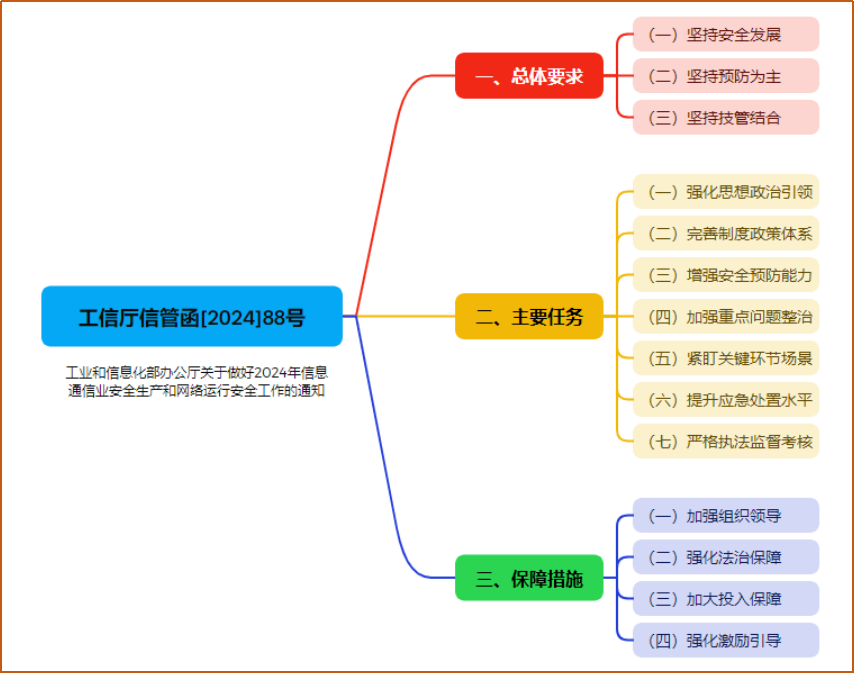
Highlights of the “General Requirements” section
1. Adhere to prevention first
We should firmly establish the concept of “hidden dangers are accidents”, strive to eliminate major accident hazards caused by lack of major risk management and control measures or inadequate implementation, and promote the transformation of the safety production governance model to prior prevention.
Suggestions for APP operating units: “Prevention first” should build APP-related security capabilities to prevent safety accidents. Technical means such as APP security detection, security reinforcement, phishing and counterfeiting monitoring, and security threat awareness are all effective preventive measures.
2. Adhere to the integration of technology and management
Strengthen scientific and technological support,Build a system of technical means for pre-event risk warning, mid-event research and judgment, and post-event traceability management, enhance network operation intelligent perception, rapid response, autonomous self-healing capabilities, and improve the level of intelligence. Suggestions for APP operating units: Ai Encryption mobile APP threat perception platform fully meets the requirements of this indicator. With the help of scientific and technological means, we can build pre-event risk warning, mid-event research and judgment, and post-event traceability management for APP security. It helps to enhance the intelligent level of intelligent perception and rapid response processing.
Highlights of the “Main Tasks” section
1. Improve the institutional policy system
First, strengthen the construction of institutional systems.Based on the actual situation of the region and the unit, we will continue to improve the safety management system for production safety and network operation, and organizePolicy and system publicity and implementation training to continuously improve the level of work institutionalization。
The second is to strengthen the construction of the standard system.Formulate basic specifications for safety production and network operation safety standardization, 5G network operation safety risk assessment series standards, etc., promote the construction and evaluation of safety production and network operation safety standardization management system, and continue to deepenPromote the implementation of standards and give full play to the role of standards in guiding and standardizing。
2. Improve the level of emergency response
The first is to improve the emergency plan system. Improve the network failure emergency plan system, fully consider various extreme scenarios, improve the enterprise emergency response plan library, and strengthen the practicality of on-site emergency response plans for key positions and key locations.
The second is to improve the rapid response mechanism. Carry out network operation security scenario-based and scripted drills to improve existing network switching and cross-regional, cross-department and cross-professional collaborative processing capabilities.
The third is to strengthen the guarantee of scientific and technological strength. Build a communication network operation extreme accident scenario test and verification platform, simulate extreme network operation scenarios, and carry out test verification and simulation drills.
Suggestions for APP operating units: A complete emergency plan system, test verification and simulation drills must include the following three major services:
1.APP security emergency response service. Including emergency testing, problem analysis, etc., providing emergency support services during major events every year.
2. APP channel monitoring service. Incorporate channel monitoring into the emergency plan system and regularly monitor whether there are abnormal applications such as phishing and counterfeiting.
3. APP penetration testing services. Regularly conduct APP penetration testing to deeply explore, analyze and verify its security from the perspective of intrusion. Coupled with complete mobile application security knowledge, product knowledge training, and interpretation of relevant standards and normative documents, it is possible to improve the level of work institutionalization and improve the safety production and network operation safety management system. iCrypto has long-term follow-up on the dynamics of regulatory authorities and interprets corresponding regulations, documents, and standards.
3. Strict law enforcement supervision and assessment
First, improve the assessment and evaluation mechanism. Each enterprise must formulate its own assessment and evaluation regulations and include relevant work conditions into performance evaluation indicators.
The second is to strengthen daily inspections. Comprehensively use the “four no's and two straights”, overt and covert inspections and other methods to carry out in-depth inspections, increase the intensity of interviews and notifications, and maintain a high-pressure posture of “cracking down on illegal activities and treating violations” at all times.
The third is to strictly investigate responsibility for accidents.Improve the accident liability investigation mechanism, strictly enforce law enforcement supervision, and investigate and deal with the local information and communication industry safety production andNetwork operation security violations; If safety accidents in production safety and network operation occur, resulting in adverse consequences, relevant units and individuals will be strictly held accountable in accordance with regulations.
Suggestions for APP operating units: It is recommended to use various automated tool platforms to strengthen daily inspection work and quickly conduct inspections or self-examinations.
1. Mobile application security detection platform. From the perspective of APP security, detect whether there are vulnerability risks, discover problems in a timely manner and rectify them.
2. Mobile application personal information detection platform. From the perspective of APP privacy compliance, we can quickly detect whether there are violations of the regulations and requirements of Ministry of Industry and Information Technology Document No. 164, State Secretariat Office Document No. 191 and other documents.
3. Source code audit platform. Use white-box testing to test and analyze the source code of the target application to fundamentally discover potential vulnerabilities in the business system.
Highlights of the “Safeguard Measures” section
Strengthen motivation and guidance. Each unit must improve the positive incentive mechanism, select outstanding achievements and typical cases, and summarize and promote experience; link safety production and network operation safety performance with duty performance evaluation, job promotion, rewards and punishments;
Encourage the continuous improvement of the safety quality of employees in the communications construction field and the enhancement of corporate safety culture through safety skills training, safety production knowledge competitions and other activities. iEncryption can provide a comprehensive, one-stop mobile security lifecycle solution. iEncryption mobile application security detection platform uses static detection technology and dynamic detection technology to detect security risks and vulnerabilities in Android applications, Hongmeng applications, iOS applications, Android SDK, WeChat public accounts, WeChat applets, and IoT firmware, helping companies discover them in advance Existing security risks and vulnerabilities, establish a security development baseline,Implement the “prevention first” idea proposed in No. 88 and practice the “strengthening daily inspections” proposed in the document. The detailed list of corresponding capabilities can be seen in the figure below.
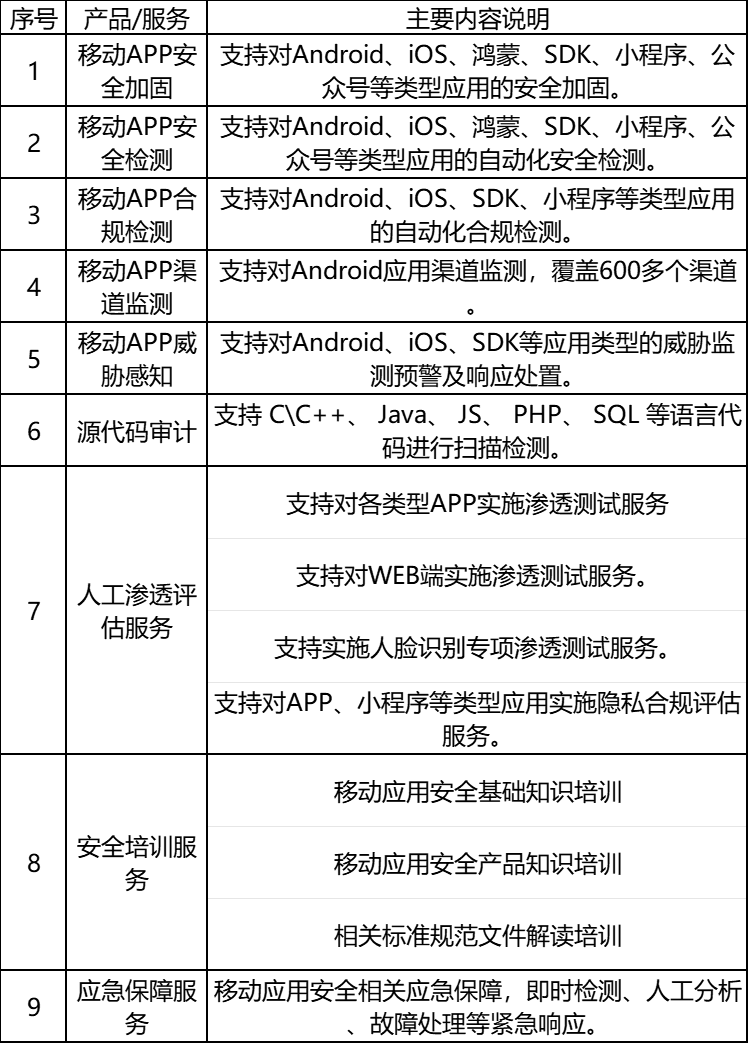
As a comprehensive service provider for mobile information security, iCrypto will continue to strengthen technological innovation and research, continue to pay attention to the latest regulatory requirements and enterprise pain points, help enterprises effectively prevent and resolve risks, and safeguard the high-quality development of enterprises.
If reprinted, please indicate the original address.


Thank you for your support, I will continue to work hard!
OpenWeChatScan and click on the upper right corner to share.
You may be interested
-

CACTER AI Laboratory: Application of large AI models in the field of email security
-

Document Interpretation | Document No. 88 of the Ministry of Industry and Information Technology was released, emphasizing 7 major tasks and 6 key points
-

Security Update Review | UnitedHealth Group pays ransom to ransomware gang to stop data breach, Microsoft fixes Outlook security alert bug
-

[Alliance News]The 8th China Internet Information Industry Pioneer Forum was successfully held
-

The first “Matrix Cup” official announcement, spreading 20 million to detonate the network security circle
-

Xuanjing Security Random: The number one hacker who decrypts supply chain security intelligence











GIPHY App Key not set. Please check settings