
Introduction: Han Yun, a security expert from iEncryption, explains de-identification and anonymization.

Personal information compliance and data export are core concerns of major regulatory authorities and enterprises. In order to assist major enterprises in strengthening their personal information compliance management capabilities and personal information protection capabilities, iEncryption security expert Han Yun discusses de-identification and anonymization. Interpret.At the legal level, the main differences between the two are whether it is necessary to comply with the “Personal Information Protection Law” (hereinafter referred to as the “Personal Protection Law”) and the relevant regulations on data export.. In response to reporters’ questions on the “Regulations on Promoting and Regulating Cross-border Data Flows” released on March 22,The relevant person in charge of the Cyberspace Administration of China once again emphasized the differences between the two.。Personal information after de-identification is still personal information stipulated in the “Personal Protection Law”, subject to regulations such as the Personal Protection Law and the Provisions on Promoting and Regulating Cross-Border Data Flows. Anonymization is through more thorough technical processing to ensure that the information cannot be used to re-identify individuals.Anonymized information does not constitute personal information as specified in the Personal Protection Law. “Information Security Technology Personal Information De-Identification Guide” (GB/T 37964-2019) lists commonly used de-identification technologies, including statistics, suppression, generalization, randomization, aggregation, etc., and compares the technical processing methods used for anonymization The overlap is very high.
However, anonymization technology is more secure, and the purpose of processing is to process personal information into non-personal information to protect personal privacy and data security to the greatest extent. The goal of de-identification technology is to reduce the correlation between the information in the data set and the subject of personal information. The de-identification technology emphasizes reducing the distinction of information, so that the information cannot be mapped to a specific individual, and lower distinction cannot determine the difference. Whether the information corresponds to the same person.
different concepts
De-identification is the processing of personal information so that it cannot be identified or linked to a specific individual without the use of additional information. This processing is usually reversible, meaning that the essential usability of the information is retained to a certain extent, while information that directly or indirectly identifies an individual is removed.
For example, through the use of techniques such as pseudonymization, encryption, or hash functions, the data cannot be re-identified to an individual without the use of specific keys or information. Anonymization is a more powerful process that uses technical processing of personal information to render the information unable to identify a specific individual and cannot be recovered. This means that anonymized information no longer contains sufficient data to re-identify an individual, even if additional information is used. Anonymization processing usually includes techniques such as generalization, compression, decomposition, and replacement to ensure irreversible de-identification of information.
Differences in security requirements
(1) Security requirements for anonymization
1. After the personal information storage period exceeds (including the minimum time necessary to achieve the purpose of use, legal time, or authorization period), the personal information controller should delete or anonymize the personal information.
2. When the personal information subject cancels the account, when the personal information controller needs to collect sensitive personal information to verify the identity, the personal information controller should clarify the processing measures after collecting the sensitive personal information, such as deleting or anonymizing it immediately after the purpose is achieved, etc.
3. After the personal information subject cancels the account, the personal information controller should delete or anonymize the personal information in a timely manner.
4. When the personal information controller stops operating its products or services, it should delete or anonymize the personal information it holds.
5. Personal information controllers that use personalized display in the process of pushing news information services to personal information subjects should: provide deletion or anonymization orientation to the personal information subject when the personal information subject chooses to exit or close the personalized display mode. Option to push personal information on which activity is based.
6. Personal information controllers should conduct a personal information security impact assessment on the risk of re-identifying personal information subjects from anonymized data sets or re-identifying personal information subjects after aggregation with other data sets.
(2) Security requirements for de-identification
1. The controller of personal information is an academic research institution. It is necessary to carry out statistical or academic research for the public interest. When it provides the results of academic research or description to external parties, the collection and use of personal information does not require the authorization and consent of the personal information subject. However, the personal information controller must de-identify the personal information contained in the results. 2. The personal information controller uses the collected personal information for academic research or to derive a description of the overall state of natural, scientific, social, economic and other phenomena, within the scope that is reasonably related to the purpose of collection, and does not require additional solicitation. Obtain the express consent of the personal information subject. However, when the results of academic research or description are provided to the outside world, the personal information contained in the results needs to be de-identified.
3. After collecting personal information, personal information controllers should immediately carry out de-identification processing and take technical and management measures to store information that can be used to recover personal identification and de-identified information separately and enhance access and use. permission management. Personal information controllers should do their best to avoid association of de-identified information with other additional information that can be used to recover the identification of individuals, or the risk of re-identification.
4. When it comes to displaying personal information through interfaces (such as display screens and paper), personal information controllers should take measures such as de-identification of the personal information to be displayed to reduce the risk of leakage of personal information during the display process. For example, when displaying personal information, prevent unauthorized internal personnel and other persons other than the subject of personal information from obtaining personal information without authorization.
5. If the personal information controller shares or transfers de-identified personal information and ensures that the data recipient cannot re-identify or associate the personal information subject, it does not need to inform the personal information subject of the purpose of sharing or transferring the personal information and the data reception. The types of parties and possible consequences do not require prior authorization and consent from the personal information subject.
6. Personal information controllers should conduct a personal information security impact assessment on the risk of re-identifying personal information subjects in de-identified data sets or re-identifying personal information subjects after aggregation with other data sets.
Technical focus
Anonymization technology is currently an important data security measure and has developed many mature technical solutions, such as generalization, compression, decomposition, replacement, interference, etc. According to the provisions of the “Personal Information Security Specifications”, anonymization technology is used to process The resulting information must be impossible to recover as personal information and cannot be identified or linked to a specific individual. De-identification is based on individuals, retains individual granularity, and uses pseudonyms, encryption, hash functions and other technical means to replace the identification of personal information. Although de-identification technology can make personal information unable to be easily identified, if an unauthorized third party has the assistance of other external information, it is still possible to re-identify the personal information processed by de-identification technology.
iEncryption has long been paying attention to the field of personal information compliance, continues to interpret regulatory department documents, and provides services in the field of personal information compliance! In the personal information collection process, iCrypto provides professional mobile application personal information security testing and mobile application personal information security compliance assessment services to assist companies in complying with laws and regulations and comprehensively reduce the risk of violations. It also has special testing for core documents such as the Ministry of Industry and Information Technology[Document No. 164]the four ministries and commissions[DocumentNo191]automatic detection items, GB/T 35273, GB/T 41391 and other core documents, which can more deeply detect whether applications violate special regulations.
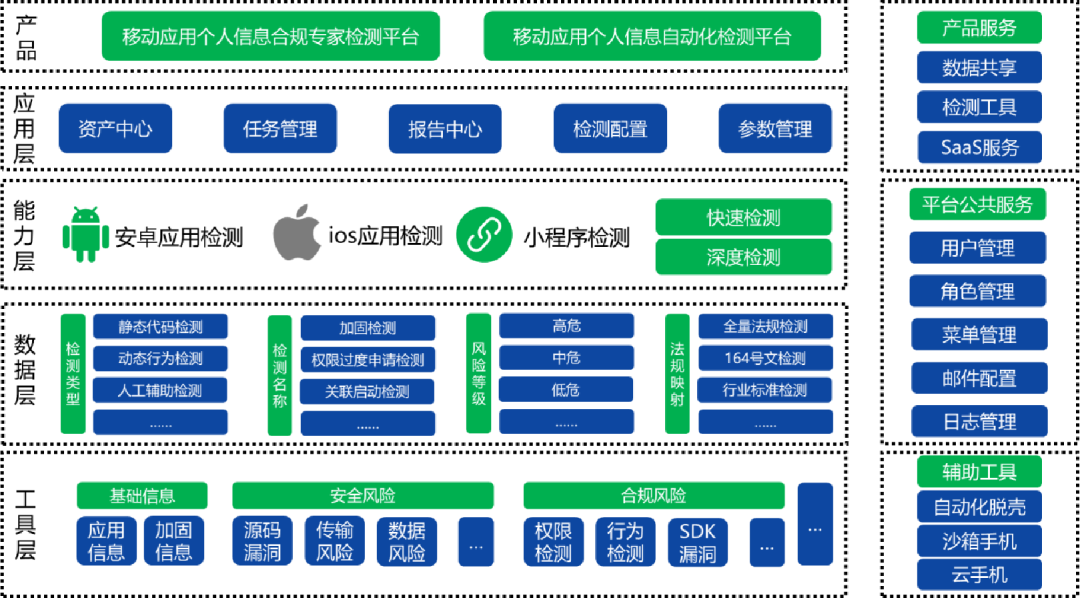
In the data flow link, we have launched a data flow security solution to reduce security risks in the data flow link through products such as a data outbound compliance management platform, data security evaluation system, data security classification and grading asset map, and API security monitoring system.
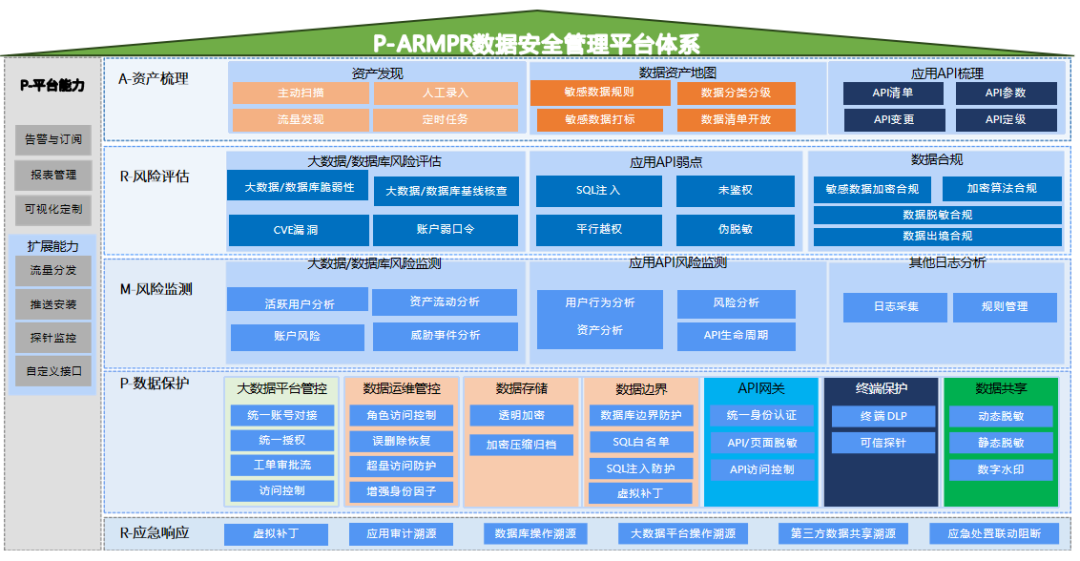
As a comprehensive service provider for mobile information security, iCrypto continues to focus on the field of personal information compliance, and will actively provide technical support to regulatory authorities, continue to improve enterprise data compliance development solutions, and safeguard the construction of Digital China.
If reprinted, please indicate the original address.


Thank you for your support, I will continue to work hard!
OpenWeChatScan and click on the upper right corner to share.
You may be interested
-

Document Interpretation | The difference between de-identification and anonymization in personal information data processing
-

360 joins hands with Jiangxi Software Vocational and Technical University to promote the construction and development of the Digital Security Industry College
-

Fortinet Named a “Challenger” in the 2024 Gartner Magic Quadrant for Security Services Edge (SSE)
-
Innovation does not stop, and many achievements of the National Cyber Security Industrial Park (Tongzhou Park) enterprises have been recognized by the industry again
-

2024 Q1 Enterprise Email Security Research Report: Phishing emails increased by 59.9% year-on-year
-

Personal Information | Analysis of Q1 violation notifications is released, the number of notifications increased by 180% month-on-month, and the Ministry of Industry and Information Technology’s key directions are clear











GIPHY App Key not set. Please check settings