IoT Security Market Guide 2024
Date: May 24, 2024
Views: 88

Table of contents
IoT Security Market Trends
1.1. Overview of IoT Security
1.2. Overview of IoT Security Market
1.3. Development Trends of IoT Security Market
Opportunities and challenges facing the IoT security market
2.1. Development trend of IoT technology
2.2. Macro factors support and requirements for IoT security
2.3. Technological innovation supports and demands IoT security
1. IoT security market situation
1.1. Overview of IoT Security
1.1.1. IoT security concept
The Internet of Things is a network of narrowband IoT, local area networks, Internet-connected physical devices, vehicles, cameras, and other items that can collect and exchange data, transmit data, and promote it to a wide range of application scenarios. IoT security refers to a series of measures and practices to protect the IoT system from attacks, data leaks, service interruptions, and other security threats. Since IoT devices are often deployed in critical infrastructure and daily life, their security vulnerabilities may have serious impacts on personal privacy, corporate data, and public safety.
The challenges facing IoT security include device diversity, resource limitations, update and maintenance difficulties, authentication and access control issues, data protection requirements, and privacy protection. To ensure IoT security, comprehensive measures need to be taken in terms of device design, network security, data protection, identity and access management, privacy protection, and security monitoring and response.
Therefore, IoT security requires manufacturers, service providers, users, and policymakers to work together to reduce risks and protect IoT systems through practices such as risk assessment, secure design, secure configuration, regular updates, security training, and emergency response plans.
1.1.2. Main technologies and products of the Internet of Things
Security Cow classifies IoT security as a first-level category, which is in line with the definition of cloud, big data, and mobile Internet scenarios in Information Security Protection 2.0. In the overall IoT scenario, based on the current mainstream market revenue division, IoT security is further divided into: video surveillance security, Internet of Vehicles security, and other IoT security.

Based on security protection technology, IoT security products can be divided into the following categories:
- Security Gateway:Filter the network access of the terminal devices of the perception layer and the platform layer to reduce network layer attacks, application layer attacks, business continuity attacks, etc., including access control of terminal devices and access control of the platform.
- Safety certification:Access is controlled through identity authentication, including operation and maintenance control of IoT terminals, access authentication of private networks, and operation audit of IoT platforms.
- Data protection: For data leakage prevention of IoT terminals, security management of data applications on IoT platforms, especially in scenarios where video surveillance systems and Internet of Vehicles systems have high requirements for personal privacy protection and have strong compliance policies, there are usually special data leakage prevention products.
- Encryption: Encryption products are formed to meet the requirements of data transmission. In the field of video surveillance security, they are usually encrypted directly on the gateway side by specialized manufacturers, while in the field of Internet of Vehicles, they are usually carried out by cryptographic manufacturers.
- Reinforcement:Mainly strengthen the software and hardware of IoT terminals and reduce the vulnerabilities of embedded systems. It is mainly carried out by supply chain security vendors and mobile security vendors.
- Scanning Evaluation:Scan, detect and manage terminals in the IoT system, scan for vulnerabilities, and also evaluate and consult on security compliance issues in IoT scenarios.
1.2. Overview of IoT Security Market
1.2.1. Cybersecurity market situation
2023 is a challenging year for the cybersecurity industry. With the adjustment of the macro-economy, the cybersecurity industry has also faced challenges. In 2023, the growth rate of my country's cybersecurity market slowed down significantly, and the cybersecurity industry faced great pressure. Judging from the data in Q1 2024, the pressure faced by the cybersecurity industry is still continuing, and it is expected that the growth rate of the cybersecurity market size will slow down further in 2024.

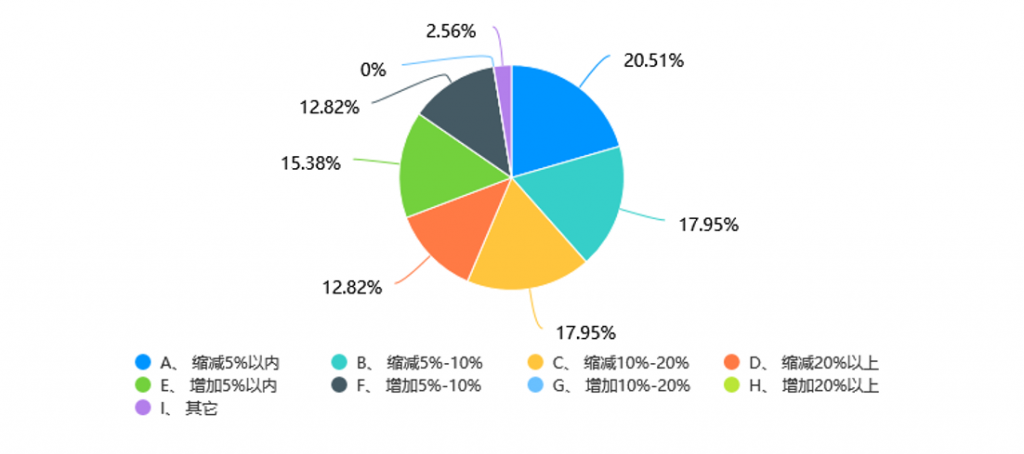
This is also proven from the user side. The survey shows that 69.23% of companies will reduce their security budgets, and 12.82% of them will reduce their budgets by more than 20%.

From the perspective of the cybersecurity market, this year, Party A users are more concerned about purchasing products that can actually solve their own problems rather than conceptual products. Therefore, even if the scale of the cybersecurity market is facing greater pressure, cybersecurity companies with specialized cybersecurity fields and core capabilities still have strong competitive advantages.
1.2.2. IoT security market situation
According to the survey data of “Panorama of China's Cybersecurity Industry (Eleventh Edition)”, my country's Internet of Things industry security market in 2023 will be approximately RMB 2.102 billion, accounting for approximately 2.0% of the cybersecurity industry.

According to statistics, the industrial scale of the IoT security field in 2022 is about 3.8532 billion yuan. In the 2022 panorama of the IoT field, we have included some IoT platform construction projects, such as video surveillance network construction projects, IoT monitoring platform construction projects, vehicle monitoring platform projects, etc. In the 2023 panorama, we focus more on the security of the IoT itself, so we will no longer include this type of product. In addition to the construction of the IoT platform, the industrial scale of the IoT security field in 2022 is about20.600 million yuan. In subsequent calculations, we will also calculate at 2.06 billion yuan. The growth rate of the IoT security market size in 2023 is 2.04%. The intensity of competition in the IoT security market is relatively low. According to the declaration data of the eleventh edition of the panoramic view of the cybersecurity industry, a total of 128 products or solutions were declared for IoT security. Compared with the overall 4,941 declarations, the declaration rate is about 2.59%. The IoT security field has a certain layout threshold. Compared with other cybersecurity fields, the competitive pressure between manufacturers in the IoT security field is relatively small.
1.2.3. IoT security market segments and trends
Security Cow has always divided IoT security into three sub-categories:
- Internet of Vehicles Security: Security solutions for Internet of Vehicles terminals, transmission protocols and management systems;
- Video surveillance security: It has overall security protection capabilities for video surveillance, including but not limited to ensuring that the surveillance network is not breached, video data is not damaged, important content is not leaked, security incidents can be traced, and circulating data is not tampered with.
- Other IoT security: products (solutions) that do not belong to the above two types of IoT security devices and platforms.
According to the survey data of “Panorama of China's Cybersecurity Industry (Eleventh Edition)”, in terms of revenue scale, in 2023, the growth rate of video surveillance security will be relatively fast at 4.3%, the growth rate of other IoT security will be 1.2%, and the revenue of Internet of Vehicles security will drop by 4.4%.

The proportion of different secondary classification sub-sectors has changed slightly, but the ranking of each category remains unchanged, and the overall trend is stable. The proportion of video surveillance security in the overall IoT security field increased from 50.72% to 51.84%, while the proportion of Internet of Vehicles security decreased from 12.48% to 11.68%, and other IoT security decreased slightly from 36.80% to 36.48%.

1.3. Development Trends of IoT Security Market
Judging from the overall scale of IoT security, my country's IoT security market is in a state of stable development. Although my country's network security market is facing great pressure, since IoT devices are directly related to natural persons, IoT device suppliers will inevitably pay more attention to security issues in business development, the core of which includes natural persons' personal safety and privacy security.
- Development Trends of Internet of Vehicles Security Market
From 2022 to 2023, the overall revenue scale of Internet of Vehicles security will show a downward trend. The main reason for the decline in revenue is the rapid decline in revenue of Internet of Vehicles security situation platform products, namely security platforms for integrated vehicle management, vehicle data management platforms for car companies, etc. Compared with platform products, security analysis products for IoT components in the Internet of Vehicles, firmware reinforcement products, and vehicle-mounted intrusion detection products have remained almost unchanged, or have only declined slightly. Internet of Vehicles platform products are the main part of Internet of Vehicles security revenue, so changes in the revenue of Internet of Vehicles platform products also have an important impact on the entire Internet of Vehicles security market.
In 2024, the core growth point in Internet of Vehicles security will focus on data security. From security issues in vehicle-side data collection, to data transmission issues, to data security issues in data storage, they will be gradually promoted to car companies this year. With the increase in car sales, the security protection revenue of traditional vehicle terminals will maintain steady development and maintain the current share in 2024. Considering the current deployment volume of Internet of Vehicles security platform products, Internet of Vehicles security situation platform products will maintain the current share this year, or will decline slightly.
- Video surveillance security market development trends
Video surveillance security will grow rapidly in 2023, and the main market share of video surveillance security is concentrated in video access gateways. According to the continuous tracking of manufacturers in this field by Anquanniu, video surveillance security has shown a strong market share stability pattern, and leading companies continue to maintain a strong market share in this field. With the country's advancement of the construction of a comprehensive monitoring and early warning platform, in the short term, the video surveillance security field will continue to grow, and its share will continue to be the largest.
- Other IoT security market trends
In other IoT fields, SafeNiu mainly includes smart IoT device security, public display screens, IoT platform security, etc. From the perspective of segmented products, IoT terminal firmware security checks have basically maintained a stable market size, public display screen security has slightly increased, and IoT security platform products have basically remained stable. With the increase in the types and number of smart terminal devices, the demand for IoT terminal security will continue to increase, and other IoT security markets will also grow steadily. Among them, data protection for IoT terminal firmware and access control products for IoT smart terminals will be the most important markets.
2. Opportunities and challenges facing the IoT security market
2.1. Development trend of IoT technology
In recent years, the number of IoT terminals has exploded, and the IoT device management platform is also advancing steadily. IoT application solutions are widely used in agriculture, industry, information industry, smart cities, and personal applications.
2.1.1. Macroeconomic policy orientation
The Internet of Things is an important part of improving the country's digital capabilities, promoting industrial upgrading, improving people's quality of life, and improving public service capabilities. In the past two years, as one of my country's strategic emerging industries, policies to promote the development of the Internet of Things industry have been repeatedly introduced to provide support for the development of the Internet of Things industry.

The Ministry of Industry and Information Technology and eight other departments issued the “Three-Year Action Plan for the Construction of New IoT Infrastructure (2021-2023)”, which aims to initially build IoT infrastructure by 2023 through technological innovation, industry cultivation, application integration and system optimization, promote the digital transformation of the economy and society, and support the construction of a strong manufacturing country and a strong network country. Through this action plan, the Chinese government has demonstrated its high attention to the development of IoT technology and its determination to promote high-quality economic development through technological innovation and industrial upgrading.
2.1.2. Technology development trends

From the perspective of the perception layer, according to IDC data, the number of IoT connections in China will exceed 6.6 billion in 2023, and the compound growth rate is expected to be about 16.4% in the next five years. IoT terminal devices include sensor devices, smart home wearable devices, smart industrial terminals, smart city terminals, etc., and the security requirements of different types of terminal devices are not the same. The security requirements of IoT terminals mainly include the operation security of IoT terminal devices, the security of data collected by IoT terminals, and the access security of IoT terminal devices. The increase in the number and types of IoT terminals makes network protection solutions no longer universal. The requirements for security solutions brought about by the growth of IoT terminals include: compatibility with devices, fit with business, and minimization of performance impact.
From the perspective of the network layer, the widespread application of 5G networks is the main change in IoT technology in recent years. my country has initially formed a pattern of coordinated development of narrowband IoT (NB-IoT), wireless local area networks, 4G, 5G, and wireless ad hoc networks. Different network connection methods also bring more complex security challenges to the IoT network layer. The main risks faced by the network layer include encryption issues in network transmission, isolation issues of shared networks, and authentication issues based on edge computing needs.
From the perspective of the platform and application layer, with the increase in IoT application scenarios, IoT platforms with different business characteristics have been gradually established and improved, and the increase in IoT platform products has also brought more urgent security needs. With the increase in the number of perception layers and the increase in network speed, the amount of data, access volume, and computing volume that the platform needs to carry will also increase further. Whether it is the operational security of the IoT platform or the data security of the IoT platform, they are all issues that current platform operators need to consider.
2.2. Macro factors support and requirements for IoT security
The macro factors affecting IoT security can be divided into economic impact, policy impact and market impact. The impact on the IoT security market is analyzed from three dimensions: supervision, supply and demand.
2.1.1. Economic impact
Macroeconomic factors have both direct and indirect impacts on the market size of IoT security products. Macroeconomics not only represents the prospects of the IoT security market, but also represents users' demand for IoT security products.
- Overall market size impact
Economic changes directly affect Party A's consideration of the necessity of building the Internet of Things, as well as the expenditures on IoT security at the same time as IoT construction, and will also make companies have biased choices when making expenditures. When the economy is growing, companies are more willing to deploy overall solutions and platform products. When the economy is down, they are more willing to choose security products that can directly protect IoT devices. This is also the reason why in 2023, platform products in the fields of IoT, Internet of Vehicles, etc. will decline slightly, while terminal firmware reinforcement and terminal access control products will remain stable or even grow slightly.
- Sales price impact
Economic changes have also affected the cost control of IoT terminal suppliers. IoT terminals are engaged in a “price war” on the selling price, which will inevitably require extreme control of the cost of each component. The price of a single product has a greater impact on terminal products such as in-vehicle networking terminals and IoT terminals. This also means that security vendors need to control their own R&D costs, hardware costs, etc.
- Innovation Impact
The economic environment will also affect innovation and development in the field of IoT. When funds are sufficient and the market is active, companies are willing to choose to develop new IoT technologies and products, and simultaneously carry out IoT security construction. However, under economic pressure, R&D activities may be restricted, and users are more willing to focus on marketing. At this time, IoT security will become a stock market, and it will be difficult to make further breakthroughs.
- Capital Market Impact
Macroeconomic fluctuations will affect investor confidence and investment decisions. In the case of economic slowdown or increased uncertainty, venture capital may decrease, which will directly affect the fundraising and growth of IoT security startups. In 2024, there will be a certain lack of investment in my country's cybersecurity market. Without capital support, IoT security companies are more willing to shrink their production lines and invest costs in more advantageous projects. Therefore, in the field of IoT security, the market size and number of products of specialized manufacturers will be more stable.
2.1.2. Policy orientation
At present, the IoT security industry is still a policy-oriented industry, and compliance is still the main driving force for the future development of IoT security. In 2017, GB 35114-2017 “Technical Requirements for Information Security of Public Security Video Surveillance Networks” was implemented, which made mandatory requirements for the security protection of surveillance video information. Since 2018, the National Information Security Standardization Technical Committee has intensively launched a number of national standards for the Internet of Things. In the Information Security Protection 2.0, the requirements for IoT security are expanded, and the IoT device security, data transmission security, access control, device identity authentication, security monitoring and response, supply chain security and personal information protection are stipulated.
In recent years, the national, local and industry levels have made it clear that the security of the Internet of Things requires the simultaneous construction of security capabilities when building the Internet of Things.

The policy guides the layout of IoT security companies in their products in the future. At the current stage, the data security field in the Internet of Vehicles is an important technical development issue. On the other hand, this orientation will also be further extended to the field of IoT. That is, the data security market will be an important part of the IoT security field in recent years.
2.2.3. Market competition
From the supply-side perspective, according to the panoramic survey data of Security Cow, the competitive pressure in the field of IoT security is not as strong as that in the field of traditional network security, and this field has certain entry barriers.
Domestic IoT security manufacturers can be divided into: specialized manufacturers, cryptographic manufacturers, comprehensive security manufacturers, and other manufacturers. These manufacturers are concentrated in the middle reaches of the IoT security industry chain, cooperating and competing.

Decomposing the IoT security industry chain from the perspective of the IoT hierarchical architecture, different types of security vendors usually cover one or several fields. At present, the cybersecurity industry is in a fragmented stage. Compared with the cybersecurity industry, the IoT security field is less fragmented. In the IoT security field, video security is supplied by specialized security vendors. Comprehensive cybersecurity vendors usually focus on access gateways for physical network devices, risk detection for IoT devices, and IoT vehicle networking platform products. Cryptography vendors and identity security vendors focus on encryption authentication at all levels. In the IoT security field, vendors are highly focused, and IoT security vendors usually only need to compete with a few fixed friendly vendors, and different types of vendors are more inclined to cooperative relationships.
2.3. Technological innovation supports and demands IoT security
The IoT perception layer is developing towards intelligence, integration, and interconnection. The introduction of new technologies not only brings new requirements for IoT security, but also brings new technical support. The emergence of new technologies is a new driving force for the IoT security market.
- AI
IoT terminal devices are gradually being combined with AI technology to provide users with a better user experience. Smart terminals are usually connected to the Internet or linked with smart devices to control smart devices and obtain system upgrades. The security risks faced by AIoT include data risks, algorithm risks, network risks, etc. These risks may directly affect personal safety in the field of Internet of Vehicles, and there is a risk of personal privacy leakage in the field of video surveillance. Therefore, the protection of AIoT is an important demand of the IoT security industry. At the same time, the application of AI has also improved the recognition and analysis capabilities of IoT security, promoting the development of IoT security technology from another dimension.
- 5G
The high speed, large number of connections and low latency of 5G networks increase the risk of network attacks and pose a threat to privacy and data security. In 5G scenarios, it is necessary to improve identity authentication and access control, traffic encryption and micro-isolation. The IoT application scenario is an important application scenario in the 5G field. The increase in the application of 5G technology in the IoT will also introduce more 5G communication manufacturers and 5G security manufacturers to compete in the IoT security field.
- Edge computing
The 5G era has increased network speeds and made it possible to decentralize computing power, further popularizing the application of edge computing technology. In edge computing, data generation and processing are all on the terminal side, and its security protection capabilities are slower than those on the center side, so it is more likely to be attacked. The application of edge computing will increase the demand for security protection on the terminal side of the Internet of Things, including data leakage prevention of terminals, system performance security of terminals, and even physical security. At the same time, it is also necessary to avoid attacks on the central platform using edge devices. At present, there are few companies in the market that specialize in edge computing solutions. Usually, manufacturers who build edge computing systems directly internalize security capabilities into edge computing systems.
- IPv6
As the number of IoT terminals increases, the application of IPv6 technology effectively solves the IoT's demand for address space and node mobility. However, IPv6 itself also has security risks. In addition to the flood attacks and application layer attacks shared with IPv4, IPv6 also has some unique protocol attacks and IPv4 bypass attacks. IoT security vendors at the network layer need to build special solutions for IPv6 security needs, and also need to adapt their security products to the IPv6 system.
- cloud platform
The IoT's demand for space and business characteristics make cloud-based deployment of IoT platforms the choice of many non-private network users. The security risks of cloud-based IoT platforms are similar to cloud security risks. At this time, IoT security vendors also need to form effective cooperation with cloud vendors and cloud security vendors to jointly build an overall cloud scenario security solution.





GIPHY App Key not set. Please check settings