Security researchers have uncovered a series of criminal campaigns that exploit cloud storage services such as Amazon S3, Google Cloud Storage, Backblaze B2, and IBM Cloud Object Storage. These campaigns were launched by unnamed threat actors with the goal of redirecting users to malicious websites and stealing their information using text messages.
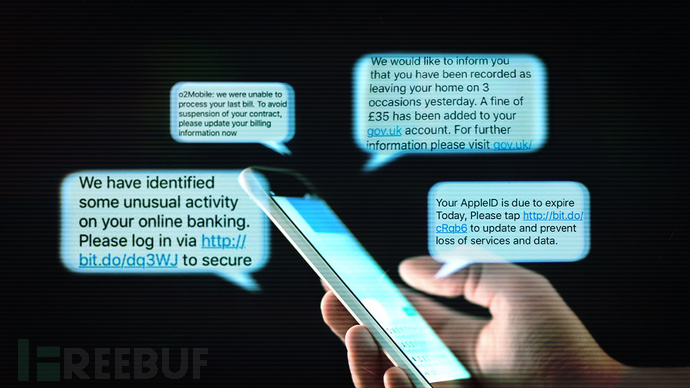 According to a technical article published today by Enea, the attackers had two main goals.
According to a technical article published today by Enea, the attackers had two main goals.
- Threat actors need to ensure that fraudulent text messages can be delivered to mobile phones without being detected by network firewalls.
- Threat actors attempt to convince end users that a text message or link they receive is authentic.
Threat actors use cloud storage platforms to host static websites with embedded spam URLs to make their messages appear legitimate and circumvent common security measures.
Cloud storage services allow businesses to store and manage files and host static websites by storing website assets in storage buckets, and threat actors exploit this capability to embed spam URLs in static websites stored on these platforms.
They distribute URLs to these cloud storage sites via text messages, which can often bypass firewall restrictions because well-known cloud domains are considered legitimate. Once users click on these links, they will be redirected to malicious websites without knowing it.
For example, the Google Cloud Storage domain “storage.googleapis.com” was used by attackers to create URLs that link to spam websites. Static web pages hosted in Google Cloud Storage buckets used the HTML meta-refresh technique to immediately redirect users to scam websites. Threat actors use this method to trick users into visiting scam websites, which often mimic legitimate offers such as gift card promotions in order to steal users' personal and financial information.
Enea has also observed other cloud storage services such as Amazon Web Services (AWS) and IBM Cloud using a similar strategy of reaching static websites hosting spam via URLs in text messages.
To protect against this type of threat, Enea recommends monitoring traffic behavior, checking URLs, and being wary of unexpected messages containing links.
Reference source: https://www.infosecurity-magazine.com/news/cloud-storage-exploited-sms/
This article is Independent opinions, no reproduction without permission, for authorization, please contact FreeBuf customer service Xiao Bee, WeChat: freebee2022






GIPHY App Key not set. Please check settings