Yuan Information Ye Xiang: Internet monitoring and supervision is the premise and foundation for realizing threat exposure management

With the rapid development of the new generation of Internet technology, business development of enterprise organizations is increasingly dependent on the network. However, the instability and risk of attacks on the Internet are also increasing. In order to ensure the stable operation and security of network systems, strengthening the monitoring and supervision of the Internet has become a key requirement at the national network security strategic level, and is also a key factor for the safe development of enterprise digital transformation.
Zhejiang Yuan Information Technology Co., Ltd. has long been focusing on the research and development and application of Internet monitoring and supervision technology, based on“Internal control risks, external defense threats” protection concept, the company currently hasComprehensively build a dynamic governance system for digital asset security risks,It includes multiple capability elements such as threat discovery, identification, protection and response.Recently, Safe Niu interviewed Mr. Ye Xiang, general manager of Yuan Information, and discussed some common issues in enterprises' Internet monitoring and supervision work from the dimensions of value, process, challenges and methods of Internet monitoring and supervision.
Ye Xiang believes that as the threat landscape continues to change, only by adopting a proactive risk management mentality and creating a threat management process that can more comprehensively reflect the actual security risk situation can enterprise organizations truly reduce the number and losses of major security incidents.Carrying out Internet monitoring and supervision is not only a guarantee for the digital security development of enterprises, but also the prerequisite and foundation for the management of continuous threat exposure.
Ye Xiang

Currently, he is the general manager of Zhejiang Yuan Information Technology Co., Ltd., a master's degree from the School of Software and Microelectronics of Peking University, an outstanding chief security officer in the Yangtze River Delta, a senior engineer, a member of the expert committee of the Zhejiang Provincial Cyberspace Security Association, and an expert in Baoding-level review by the Zhejiang Provincial Public Security Department. More than 20 years of experience in communications and network security. He has worked for China Unicom, China Telecom, China Construction Bank and Wasu Group. Senior network security team leader, familiar with the communications and network security industries, with rich experience in technology enterprise operation management and network resources. Participated in the organization and construction of China's next-generation Internet and other large-scale networks, and won the first prize for scientific and technological progress in China Unicom and the radio and television industry.
01
safe cow: How is the current development of Internet monitoring and supervision in my country? Is it necessary for ordinary corporate organizations to actively carry out Internet monitoring and supervision?
Ye Xiang: Strengthen monitoring and supervision of the Internet,It cannot just stay at the national regulatory level, but should be carried out in multiple dimensions and at multiple levels.Judging from the current actual supervision situation, from the national, provincial, prefectural and municipal levels to counties, all levels of cybersecurity, public security, industry and information technology and other industry authorities are organizing and carrying out Internet monitoring and supervision work. At the same time, many industries with line management, such as the information technology departments in finance, education, medical, energy and other industries, are gradually building relevant regulatory capabilities and have put forward testing and supervision requirements for units and organizations in the industry.
We believe that business organizationsActively carry out its own Internet exposure monitoring work, be able to discover problems early and take measures to prevent and respond to regulatory notifications, which can better protect the security of corporate Internet assets, while improving compliance capabilities and avoiding legal risks.For the majority of corporate organizations, it is necessary to fully understand the significance and value of Internet monitoring and supervision in order to actively respond to the monitoring and supervision requirements of the competent authorities.
In addition to improving compliance and strengthening defense, it is also very important for enterprises to carry out Internet monitoring and supervision to achieve their own Internet exposure management. Especially for group enterprises with multiple branches and subsidiaries, building an internal monitoring system within the group can It makes sense to detect problems earlier and resolve them effectively before notifications from regulators or even on-site disposal arrive.
02
safe cow: How do you think companies should effectively carry out Internet monitoring and supervision? What are the key requirements and links?
Ye Xiang: Regarding the technical routes and concepts for realizing Internet monitoring and supervision, we believe that external defense threats and internal control risks are two important aspects of carrying out Internet monitoring and supervision work.
External defense threats refer to theIdentify and respond to external attacks and threats through traffic monitoring. Attacks or threats such as Trojans and viruses are often transmitted through network traffic, so monitor traffic for signs of these attacks and threats.By cutting off malicious traffic, you can prevent these attacks from affecting the system and achieve the goal of external risk prevention;
Internal control risks mainly refer toBefore an actual attack occurs, you can discover and resolve potential risks in advance by managing your own attack surface.This can be achieved by simulating hacker attacks for asset scanning and penetration testing to discover your own vulnerabilities and weaknesses, and take appropriate measures to patch and circumvent them.
03
safe cow: What difficulties and challenges will organizations encounter when carrying out Internet monitoring and supervision work?
Ye Xiang: The Internet has wide coverage, many points and wide areas, and is criss-crossed. In addition to the four major operators, there are many small telecommunications service providers (ISPs), which form a mesh structure among themselves, making it difficult to fully manage the entire network through a specific point.
in particularWith the advent of the cloud computing era, the location of corporate website systems is actually not limited to a certain jurisdiction.For example, a website company located in Henan may be hosted on Alibaba Cloud, and Alibaba Cloud's physical location may be in Zhejiang. In addition, Alibaba Cloud does not only have nodes in Zhejiang. Then, users may not be able to determine the true physical location of their website. This leads to difficulties in Internet supervision, because the management methods of jurisdictions cannot fully adapt to the actual situation. In a traditional dedicated line connection, a company's location usually corresponds to its location.
At a technical level, the integration of intelligence information in the process of Internet monitoring and supervision is also a difficulty, involving the correlation of massive data. Nowadays, each system often operates independently and works independently, lacking effective collaboration. However, linkage and information sharing between systems are very important for tracing the source and accurately determining the source of the attack. If systems in different regions can be linked and matched, we can more accurately understand the source of attacks. Therefore, strengthening the linkage between systems, the correlation of massive data, and the coordinated review of intelligence from multiple vendors are of great significance to achieve high-quality Internet detection and supervision.
04
safe cow: Continuous Threat Exposure Management (CTEM) is a new idea of proactive threat discovery and defense, which emphasizes continuous threat monitoring, response and disposal based on comprehensive asset identification. In your opinion, what are the inherent connections and differences between CTEM and Internet monitoring and regulation?
Ye Xiang: CTEM is mainly aimed at monitoring and managing an enterprise's own threat exposure, and includes 5 regular actions:Asset scoping, problem discovery, prioritization, business validation, actionAfter an enterprise discovers a problem, it needs to identify the seriousness of the problem and solve the problem, which is what we usually call a closed loop of risk management.
For the regulatory authorities, only the first two steps are required: discover the problem, define which supervised unit the problem belongs to, and notify it. Although the network supervision unit also has a closed loop. When the enterprise reports that the problem has been solved, it will carry out retesting, but it is up to the enterprise itself to solve the problem and ensure normal business.
So it can be understood like this:CTEM is a set of combinations to achieve network risk management, and Internet monitoring and supervision technology can be considered as the first two punches in this combination. It is also the premise and foundation for enterprises to carry out continuous threat exposure management.
05
safe cow: What technical means and tools are currently available that can help organizations carry out Internet monitoring and supervision more effectively?
Ye Xiang: We believe that the implementation of Internet monitoring and supervision needs to start from two major aspects: traffic detection and important asset monitoring.
The first is traffic detection,For the Internet, traffic is the main consideration. From a local perspective, territorial agencies are responsible for managing all traffic through their jurisdictions. Therefore, it is important to collect and inspect the traffic in a way that can detect the presence of attacks or viruses.
Furthermore, active monitoring of important assets.Mainly to solve the situation where some assets are located non-locally. Important assets mainly refer to systems and information systems, including websites and applications. The purpose of active monitoring is to assess risk, that is, to determine whether the system is vulnerable to attack, and to conduct a quantitative risk assessment to assess the size of the risk. Especially after cloudification, traditional traffic detection methods cannot detect these assets. The monitoring of important assets is related to the location of the unit where they are located, and active detection methods must be used.
Through practice, we have found that it is not easy to monitor and supervise the Internet. Before that,Enterprises must make corresponding technical reserves, and actively utilize some innovative technologies. at the same time,Enterprises should also deploy a unified supervision platform for multiple scenarios based on the operator's data environment.And according to your own needs, you can choose a customized scenario monitoring and supervision platform.
Internet monitoring and supervision is a need at the national network security strategic level.The monitoring and supervision technology is similar to the “snake's 7 inches” and is a key point in data security construction. It will become one of the most important objects of concern to the country in the future.. From the perspective of technological development, Internet monitoring and supervision need to continuously adapt to the future development of the Internet. For example, monitoring and policing equipment that supports IPv6 is critical. Although IPv6 has been around for many years, monitoring and regulatory equipment must be compatible with this new Internet protocol. With the application of new protocols and technologies such as 5G, the focus remains on monitoring the adaptability of regulatory technologies and the needs of regulated subjects.
06
safe cow:What progress has Yuan Information made in realizing Internet monitoring and supervision?
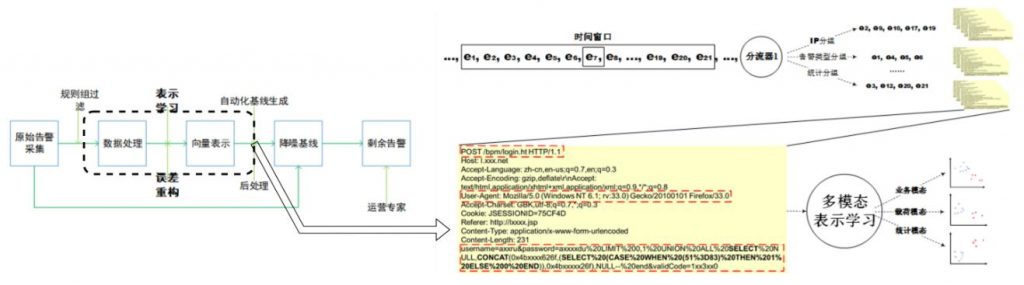
Ye Xiang: We currently propose an intelligent algorithm for the alarm overload caused by the explosion of network space alarm logs and the key issue of alarm defocus caused by the low signal-to-noise ratio of large-scale alarm logs.Used to generate explainable multi-modal network security event denoising baselines, which can adaptively generate event denoising baselines, filter low-quality events, and alleviate the information flow dependency explosion problem in event research and judgment.。

Current practical data shows that the effective noise reduction and compression rate of this technology for large-scale cyberspace alarm logs in the cyberspace security operation center can reach more than 99%. The automation level of alarm event analysis and judgment has been greatly improved, and the manual processing cost of the security operation center has been reduced by an average of 70%. %above.
In addition, Yuan Information has provided services for city-level, provincial-level and even national-level cyberspace security management and control.Coping with engineering application challenges of refinement, precision, collaboration, and globalizationproposes a scenario-based risk preference learning model, integrates data context with expert preferences, knowledge and experience, and realizes a human-machine collaborative cyberspace threat management platform solution, which better improves the risk management and control energy efficiency of critical information infrastructure; it also achieves The human-machine collaborative hunting mechanism that integrates experience and data, combined with global and coordinated cyberspace risk intelligent decision-making and refined security capability orchestration, greatly improves the automation, intelligence, and coordination of the response command process.





GIPHY App Key not set. Please check settings